One of my key objectives for developing the new vSploit modules was to test network devices such as Snort. Snort or Cisco enterprise products are widely deployed in enterprises, so Snort can safely be considered the de-facto standard when it comes to intrusion detection systems (IDS). So much that even third-party intrusion detection systems often import Snort rules.
Organizations are often having a tough time verifying that their IDS deployment actually work as intended, which is why I created several vSploit modules to test whether Snort sensors are seeing certain traffic. Since vSploit modules were made to trigger Snort alerts, they don't obfuscate attacks to avoid detection.
However, not every rule is used in every environment. For example, if you aren't using Microsoft Frontpage on your network, you likely won't want to use Snort's Frontpage rules. On the other hand, if you are running Frontpage you may not want to try exploiting it because it may affect the production system. Because of Metasploit Framework's flexibility, you can use the vSploit Generic HTTP Server module to host a small web server that answers all testing requests, so production systems won't be affected.
You can run vSploit modules with a mix of Metasploit Framework, Metasploit Pro, and Metasploit Express, providing there is end-to-end network connectivity to the vSploit instances:
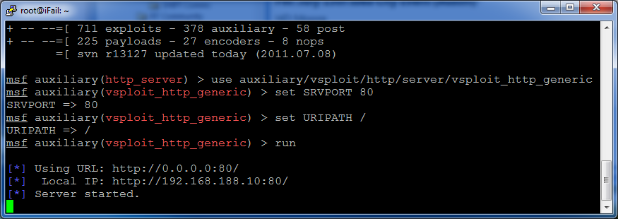
To try out the new vSploit modules, start up the vSploit Generic HTTP Server.
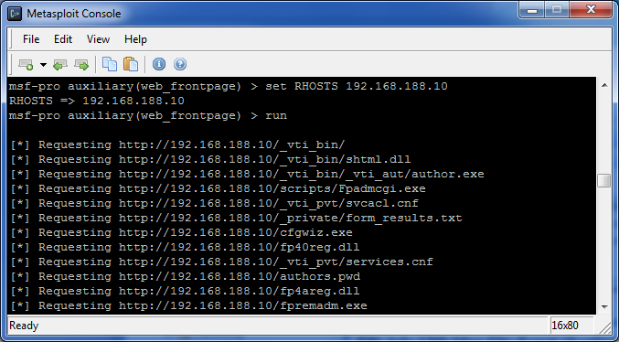
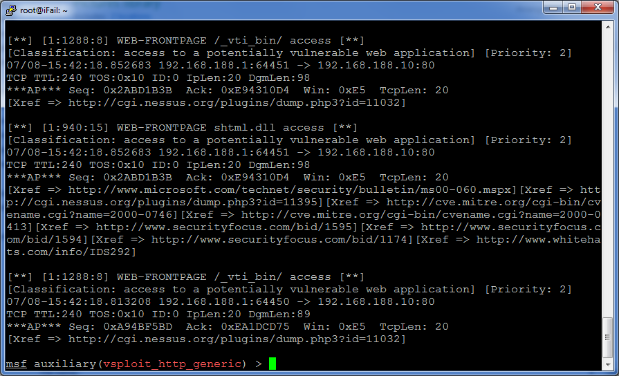
Then launch Frontpage-related attack attributes:
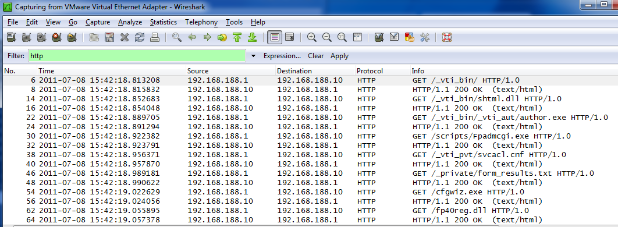
Verify that the packets are being transmitted in Wireshark:
Finally, verify that Snort IDS sees the activity:
Metasploit vSploit Modules will be released at DEFCON 19.