I am proud to announce that Nexpose 5.1.0 now supports "pass the hash", a technique to remotely authenticate against a Windows machine (or any SMB/CIFS server) with the mere possession of LM/NTLM password hashes, without needing to crack or brute force them. Nexpose is able to use the hashes to perform credentialed scans to produce very detailed scan results of all sorts of local and remote vulnerabilities that may otherwise not be detectable.
And penetration testers, rejoice! Metasploit Express and Pro were also updated this week (version 20120124000003) to automatically communicate these hashes to Nexpose. When Metasploit successfully exploits a target host and collects its password hashes from the SAM database (ie. the host status is shown as "looted"), a Nexpose scan task initiated from the Metasploit interface can use the hashes to authenticate against the host and run a credentialed scan.
The combination of these two tools is extremely powerful. In a matter of minutes, a penetration tester can go from the phase of discovery, to exploitation, to generating a comprehensive Nexpose report of all vulnerabilities affecting the target, with every step being automated.
Practical Uses of Pass the Hash
For penetration testers, pass the hash can be scarily efficient. For example, some companies follow the practice of defining a local Windows administrative account with the same very strong password on all desktops, to simplify maintenance. This is common when imaging desktops with the same disk image without bothering to randomize the local administrator password. What this means is that when only one machine is compromised, Metasploit collects the password hashes, and penetration testers instantly gain administrative access to the entire corporate network thanks to this shared administrative account, without having to brute force or crack the password.
As another example, pass the hash works just as well in Windows domain environments. When a domain administrator logs into a machine member of the domain, his password hashes are sometimes stored in the memory of the lsass.exe process. Again, if this machine is compromised, the hashes can be collected by various tools, giving the attacker instant administrative access to the entire domain.
Demonstration: Pass the hash from Metasploit Express/Pro
In Metasploit Express or Pro, after a Windows host has been scanned and exploited, and after collecting the system data using one of the exploit sessions, the host page shows the host status as looted, and the Windows password hashes are listed under the credentials tab. So far, nothing new, see:
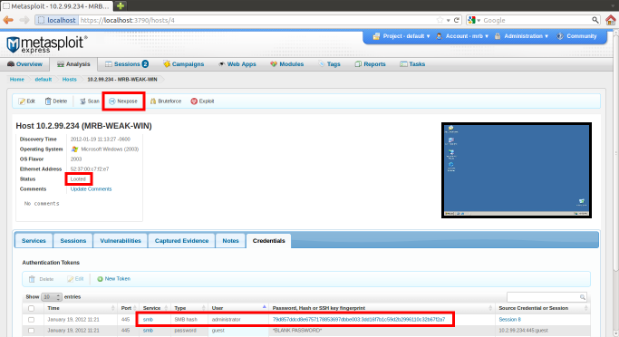
We can see the administrator password LM and NTLM hashes. For the reader's information, they correspond to the password test.3!@-pass but we do not need to know this. At this point, click the Nexpose button to launch a scan. This brings you to the Nexpose scan task page:
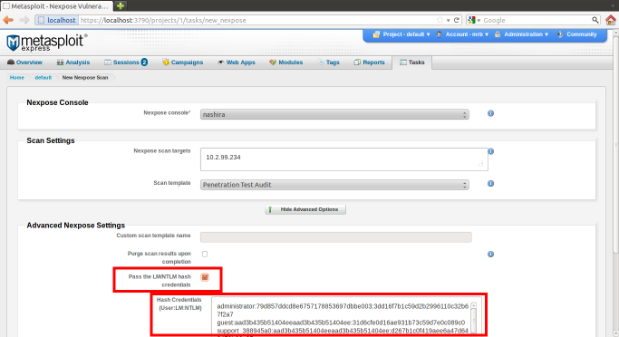
Click the new checkbox "Pass the LM/NTLM hash credentials" to enable the feature. The text field under it is automatically populated with all hashes collected by Metasploit (the end user is free to edit/add/remove any hash).
Finally, click "Launch Nexpose" at the bottom of the page and Nexpose will perform a credentialed scan. That's it!
Demonstration: Pass the hash from Nexpose
In Nexpose, when editing a site, click the Credentials tab, and you will see the new login type option called "Microsoft Windows/Samba LM/NTLM Hash (SMB/CIFS)":
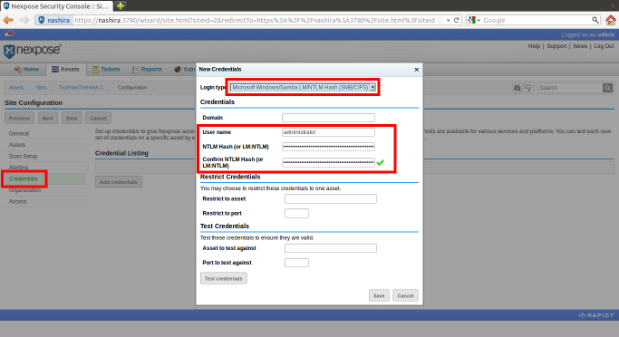
Assuming you obtained the LM/NTLM hashes some way or another, fill out the user name and hash fields manually. Use the hashes of an administrative account for the best scan results. The hash field can either be the NTLM hash alone (eg. 3dd16f7b1c59d2b2996110c32b67f2a7), or the LM and NTLM hashes separated by a colon (eg. 79d857ddcd8e6757178853697dbbe003:3dd16f7b1c59d2b2996110c32b67f2a7). The reason the LM hash can be optional is because most SMB/CIFS services, such as Windows and Samba, disregard the LM response at the protocol level when the NTLM response is valid.
I recommend to test the hashes before saving them to make sure they were not mistyped: fill out the "Asset to test against" field with a host name or IP address and click "Test credentials". If the test passes, hit Save to save the credentials, hit Save again to save the site, and the next scan launched for this site will be a credentialed scan.
Demonstration: Pass the hash from Metasploit Framework
Finally, for users of Metasploit Framework, the nexpose plugin, which interfaces with a remote Nexpose console, exposes the pass the hash feature as well. Like other Metasploit plugins, a database needs to be configured first; the example below uses postgres@localhost. Here is an example session of how the plugin can be used to pass either the LM and NTLM hashes, or only the NTLM one:
db_connect postgres@localhost
load nexpose
nexpose_connect nxadmin:[email protected] ok
nexpose_scan -c cifshash:administrator:79d857ddcd8e6757178853697dbbe003:3dd16f7b1c59d2b2996110c32b67f2a7 target.lan
(or NTLM only:)
nexpose_scan -c cifshash:administrator:3dd16f7b1c59d2b2996110c32b67f2a7 target.lan
Replace administrator:79d8...:3dd1... with the username, LM and NTLM hashes. Replace console.lan with the Nexpose console host name or address. And replace target.lan with the scan target name or address.
Bottom Line
Pass the hash is an extremely useful technique, especially because there is no way to defend against it once the hashes are stolen (it is arguably a design flaw of the SMB/CIFS protocol authentication mechanism). Its integration into Rapid7's products gives a lot of power to penetration testers.