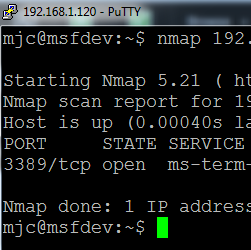
In the highlighted text below you can see that NMAP can check for the RDP service running. If you can't patch, this is important because attackers won't be able to exploit MS12-020 with the service closed. It's just basic information security hygiene to disable services that you don't need.
If you must run RDP, you'll have to patch this soon. To verify patches actually worked, you'll need a vulnerability scanner. You can download Nexpose Community Edition for free here: Free Vulnerability Scanner Download | Rapid7
It is important to note that RDP can run on any port, but TCP Port 3389 is the default.
To check one system:
mjc@msfdev:~$ nmap 192.168.1.105 -p 3389
Starting Nmap 5.21 ( http://nmap.org ) at 2012-03-13 16:59 CDT
Nmap scan report for 192.168.1.105
Host is up (0.00035s latency).
PORT STATE SERVICE
3389/tcp open ms-term-serv
Nmap done: 1 IP address (1 host up) scanned in 0.10 seconds
mjc@msfdev:~$
To check a network range:
mjc@msfdev:~$ nmap 192.168.1.0/24 -p 3389
Starting Nmap 5.21 ( http://nmap.org ) at 2012-03-13 17:07 CDT
Nmap scan report for 192.168.1.1
Host is up (0.0065s latency).
PORT STATE SERVICE
3389/tcp closed ms-term-serv
<SNIP>
Nmap done: 256 IP addresses (10 hosts up) scanned in 10.75 seconds
mjc@msfdev:~$