This week we've got a nifty new shellcode delivery scheme, we've normalized on Exploit-DB serial numbers, and a pile of new modules, so if you don't have Metasploit yet, you can snag it here.
DNS Payloads in TXT Records
To quote RFC 1464 describing DNS TXT records, "it would be useful to take advantage of the widespread use and scalability of the DNS to store information that has not been previously defined." I don't know about you, but to me, that sounds like a description for a universal shellcode delivery system. For this week's update, that's exactly what Peter "corelanc0d3r" Van Eeckhoutte has provided. Provided your target can make DNS queries against a domain you control, you can shuttle your alpha-encoded payload into an unwary DMZ or internal network.
The techniques for smuggling arbitrary data over DNS have been discussed for a little while now -- for example, Ty Miller proposed using rDNS to deliver shellcode as part of a client exploit back in 2008. Corelanc0d3r's payload stager makes things tons easier for pen-testers who would like to highlight this particular exposure. As with most of his updates, corelanc0d3r's payload itself makes heavy use of comment documentation, so I encourage you to check it out if you'd like to learn the details.
Also, in a related line of research, open source contributor Chris John Riley has provided a Rex library port of Samuel Tesla's Base32 encoder. While there isn't anything in the source tree that yet uses it, the astute reader can see where this is going. Thanks both to CJR and corelanc0der for some great work!
New EDB References
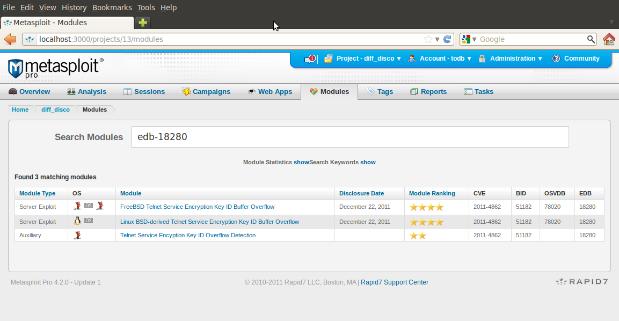

Today, we have over 130 modules in Metasploit that reference an Exploit-DB proof of concept exploit. These guys do some great work at archiving publicly available exploit code, and Exploit-DB has grown into a super-useful public resource for exploit writers and security researchers alike. So, as of this update, it's now much easier to search for exploits based on their Exploit-DB serial number.
As seen in the screenshot, searching for "EDB-18280" brings up three Metasploit modules that reference that particular Telnet exploit, and "search EDB-18280" in msfconsole returns an equivalent list. For module developers, this can be a quick way to tell if a) a Metasploit module exists for that PoC yet, and if so, b) how Metasploit's implementation differs from the public PoC.
Additional Modules
As to be expected, we also have a smattering of new modules for this week's update.
- hp_data_protector_cmd, by c4an, wireghoul, and sinn3r, exploits CVE-2011-0923 for HP Data Protector.
- manageengine_traversal, by sinn3r, exploits OSVDB-80262 for ManageEngine DeviceExpert.
- freepbx_callmenum, by muts and Martin Tschirsich, exploits EDB-18649 for FreePBX.
- ms10_002_ie_object, by sinn3r and Juan Vazquez, exploits MS10-002 for Internet Explorer.
- ricoh_dl_bof, by sinn3r, exploits OSVDB-79691 on Richo DC's DL-10.
- ultravnc_viewer_bof, by noperand, exploits CVE-2008-0610 for UltraVNC.
- enum_airport, by sinn3r, is a post module which collects data from a target's a local Airport preferences.
- enum_chicken_vnc_profile, by sinn3r, is a post module which collects a target's "Chicken of the VNC" profile.
Availability
If you're new to Metaspoit, you can get started by downloading Metasploit for Linux or Windows. If you're already tracking the bleeding-edge of Metasploit development, then these modules are but an msfupdate command away. For readers who prefer the packaged updates for Metasploit Community and Metasploit Pro, you'll be able to install the new hotness today when you check for updates through the Software Updates menu under Administration.
For additional details on what's changed and what's current, please see Jonathan Cran's most excellent release notes.
