It can be very frustrating to try exploiting machines and not succeeding, especially if your vulnerability report is showing a lot of vulnerabilities on the hosts you are trying to exploit. This is usually due to one of the following reasons:
- Not all reported vulnerabilities are exploitable. It may be because a firewall or IPS/IDS is successfully stopping the attack, or simply because your vulnerability scanner reported a false positive.
- Your Metasploit machine or network connection may prohibit a session from being opened.
If you think the latter may be the case, please ensure the following:
- Firewalls must be disabled on your Metasploit machine so the payload can connect back to the Metasploit machine after an exploit succeeded. The default port for this connection is 4444.
- You must disable (or even better uninstall) any anti-virus software before installing Metasploit because it may interfere with the installation because Metasploit exploits the same vulnerabilities as malware and is therefore stopped by some anti-virus software.
If you have checked all of the above but still cannot get a session, then you should try if your Metasploit installation is set up so that the Metasploit payload can actually connect back to Metasploit after a machine has been exploited. To do this, we'll launch a small executable on the target machine that connects back to Metasploit to create a session. If this test is successful, you'll know that there are no firewalls or configuration issues stopping the payload from connecting back to Metasploit. This test requires Metasploit Pro - if you don't have this version, simply register for a 7-day Metasploit Pro trial to do this test.
For this test, I'll be using two machines:
Metasploit HostTarget Host- Runs Metasploit Pro
- Target host for test
- Use browser to connect to Metasploit host
- Download and execute ClickMe.exe here
The little executable we'll be using is usually used for USB campaigns, which involve dropping USB keys in your target's parking lot and bathroom to see if anyone will plug the USB thumb drive into their machine and double-click the executable. While it was built for a different purpose, it will work just fine to test the inbound connection to Metasploit.
Here's how to test:
- The easiest way to get the executable to your test machine is to download it through the browser, so you should go to the Windows target machine and enter "https://" plus the IP adddress of the Metasploit machine with on port 3790, so in this example the link is https://10.1.95.74:3790. If you cannot connect from the target to the Metasploit machine, find out why - this may be the reason why you are not getting sessions.
- Since the SSL certificate is self-signed, you'll get a warning that it isn't trusted. Add an exception to allow this certificate to proceed.
- Log in.
- Create a new project or enter a test project that you've already set up.
- Click on the Campaigns button.
- Click on New Campaign
-
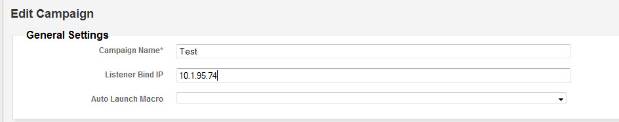
Enter Test as the name for the campaign and the IP address of the Metasploit host in the field "Listener Bind IP".
-
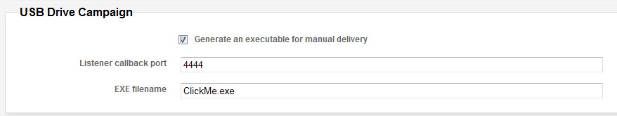
Activate the checkbox "Generate an executable for manual delivery".
-
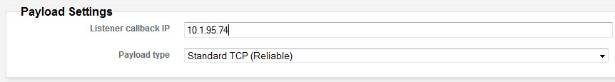
Ensure that the "Listener callback IP" also uses the Metasploit host's IP address.
- Save the campaign.
-
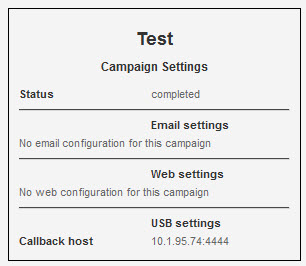
Click on Start Campaign. The campaign settings should now look like this:
- Click on Download Executable and download "ClickMe.exe" to the Windows host.
- Open and run "ClickMe.exe" on the Windows host. The file will execute but you will not see any user interface.
-
Return to the browser on the Windows machine and click on the Sessions tab. You should now see an open session. Note also the 1 in a blue circle next to the Sessions tab, indicating one active session.
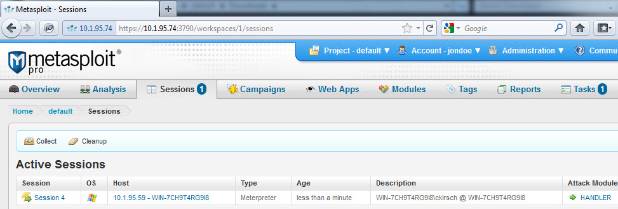
If you've successfully opened a session, your Metasploit host is correctly configured to receive connections from exploited machines.
If you are not getting a session on the machine, here are a couple of things you can try to identify the issue:
-
On the Metasploit host, check if the Metasploit service is listening on port 4444. On Ubuntu, open the terminal window and type netstat -an | grep 4444. The response should be:

If the Metasploit host is not listening, please ensure that the campaign is really started. - Verify that no firewall is active on the Metasploit host
- Verify that no anti-virus is active on the Metasploit host
- If you are having trouble executing the ClickMe.exe file, then you may have anti-virus blocking execution on the target machine. Disable AV, download the file and try again. Turn AV back on once you have completed the test.
If you're still having trouble getting Metasploit to work, please post your question in the Metasploit discussion forum (posting requires login/registration).