Experienced penetration testers know what to look out for when testing production systems so they don't disrupt operations. Here's our guide to ensure smooth sailing.
Vulnerabilities are unintentional APIs
In my warped view of the world, vulnerabilities are APIs that weren't entirely intended by the developer. They hey are also undocumented and unsupported. Some of these vulnerabilities are exploited more reliably than others, and there are essentially three vectors to rank them:
- Exploit success rate: Some exploits will get you a session every time, which is why folks luuuurve MS08-067. Others are more hit-and-miss, or they may only work on the first try but not the second.
- Target system stability: Other exploits can get you a session but the process makes the system unstable. Think of a denial of service module as an extreme case of this vector.
- Fingerprinting: Does the exploit reliably fingerprint the target system to ensure that it only works on tested target systems. Using an exploit on the wrong system can potentially destabilize the target system.
Understanding Metasploit reliability rankings
As part of Metasploit's rigorous 3-step quality assurance process, we rank exploits by reliability. Knowing the ins-and-outs of the rankings protects the stability of the systems so your IT operations buddies remain happy bunnies.
Each Metasploit exploit, and indeed each module, is classified according to five reliability levels. Modules include exploits as well as auxiliary modules, such as brute forcing modules, and payloads. Understanding the reliability rankings is key to safely test production systems.
- 5 Stars - Excellent: Safe to use on production systems. The exploit gets you a session every time (barring environmental factors) and provably cannot destabilize the target system, e.g. SQL injection, CMD execution, RFI, LFI. Memory corruption exploits are typically not given this ranking unless there are extraordinary circumstances, e.g. WMF Escape().
- 4 Stars – Great: Safe to use on production systems. The exploit has a default target and either auto-detects the appropriate target or uses an application-specific return address after a version check.
- 3 Stars – Good: Not recommended for use on production systems. The exploit has a default target and it is the "common case" for this type of software, e.g. English, Windows XP for a desktop app, 2003 for server.
- 2 Stars – Normal: Not recommended for use on production systems. The exploit is otherwise reliable, but depends on a specific version and can't reliably auto-detect or doesn't autodetect at all.
- 1 Star – Average: Not recommended for use on production systems.The exploit is generally unreliable or difficult to exploit.
- 0 Stars – Low: Not recommended for use on production systems. The exploit is nearly impossible to exploit (under 50% of cases) for common platforms.
- Manual: Not recommended for use on production systems. exploit is so unstable or difficult to exploit and is basically a DoS
Five Tips for Safe Penetration Testing
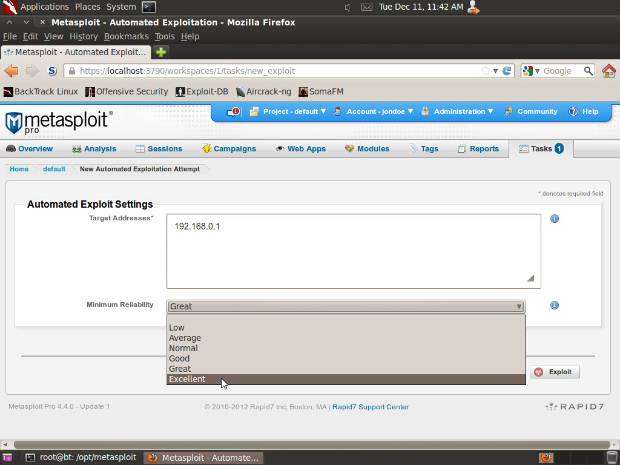
- Only use exploit modules with a reliability ranking of "Excellent" or "Great" on production systems: You read the blog post - you know why!
- Communicate with IT operations: Use only Before testing on production systems, it may be a good idea to talk to the application owners ahead of time to ensure that they're aware, buy into the process, and alert you if anything has gone awry.
- Test during maintenance windows: To play it extra safe, conduct your penetration test during official maintenance windows. We recommend not testing systems that are being serviced since this will make troubleshooting more difficult.
- Use the Audit Report to analyze situations: Of course, production systems can also go down without your having had any part in it. To protect you from unwarranted allegations, use the audit report in Metasploit Express or Metasploit Pro to prove when you did and did not touch certain systems.
- Throw the kitchen sink at test systems: Testing only with 4 and 5 star modules is great for production but less reliable vulnerabilities can still let a malicious attacker in who doesn't care about target system stability. If you have a test system that mirrors your production environment, throw everything you've got at it to cast a wider net. We still recommend also testing production it may not be a perfect image of your test environment.