Vulnerability correlation is a feature of Nexpose where a vulnerable result from one vulnerability can be overridden by an invulnerable result from another. As an example of how this works and why it is a useful option to have enabled, take CVE-2011-3192, a fun DoS vulnerability that affected Apache HTTPD back in 2011. Nexpose has one unauthenticated vulnerability check (lets call it V1) that will run against all discovered Apache HTTPD instances and analyzes the HTTPD service's behavior to determine if it is vulnerable to CVE-2011-3192. Nexpose also has several authenticated, patch-based vulnerability checks (lets call them V2) that will run against any targets for which Nexpose supports running such checks. V2 checks for and analyzes the Apache HTTPD packages installed on the target to determine if it is vulnerable to CVE-2011-3192. Assume you have a Red Hat target running Apache HTTPD as provided by Red Hat and you are using Nexpose to do credentialed vulnerability scanning. Without vulnerability correlation enabled, if the target is fully patched against RHSA-2011-1245, meaning that only invulnerable results were obtained from V2, a vulnerable result from V1 would seem like a false positive. With vulnerability correlation enabled, V2 overrides V1, eliminating the perceived false positive.
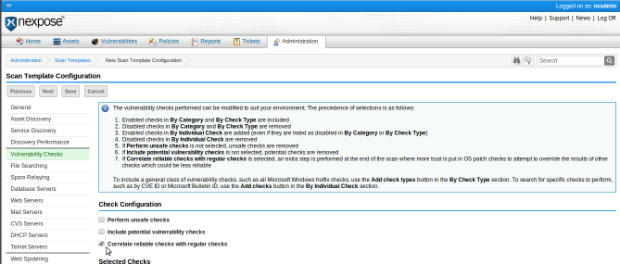
As of the release of Nexpose 5.5.11, released on February 20, 2013, vulnerability correlation is enabled by default in all shipping scan templates except those for PCI. Rapid7 strongly recommends that this be enabled in any existing or future custom scan templates as well, and to enable this please see the documentation on configuring scan templates, or the screenshot below: