Robert Lemos wrote an interesting article about how CVSS alone does not necessarily give you enough information for effective remediation prioritization. Adding context about which vulnerabilities are being exploited easily using known exploits provides a much better way of determining whether or not a given asset is at risk from a real attack. Quoting the research completed by Luca Allodi and Fabio Massacci:
"The CVSS could be high, but you may have a low risk of being exploited, while you can get a low CVSS score and still be attacked. There is not much correlation between the CVSS only and the chance of being attacked.", Massacci says.
I agree. There are many other factors that should be in play when measuring real risk to an environment. Rapid7's products leverage knowledge about Metasploit exploits, ExploitDB exploits, and malware kits to better measure the "chance for attack" of a given vulnerability than just using CVSS alone. We call this Rapid7 Real Risk™ and use this as our default risk model in Nexpose. Check out this white paper on Rapid7 Real Risk™ and how it uses security intelligence to quantify risk. We think that this provides a great starting point out of the box and you can also customize to meet the needs of your environment. You can also check out this video which explains how we use industry knowledge to better identify risk.
CVSS is a great starting point and does allow for temporal and environmental components beyond the base score. Use CVSS in conjunction with industry knowledge of current threats to assess actual risk to your environment. Use Rapid7 Real Risk™ to accurately prioritize mitigation tasks to reduce overall risk as quickly as possible. For example, within Nexpose you can use the Prioritized Remediation report to determine which patches have the most impact in reducing risk to your environment:

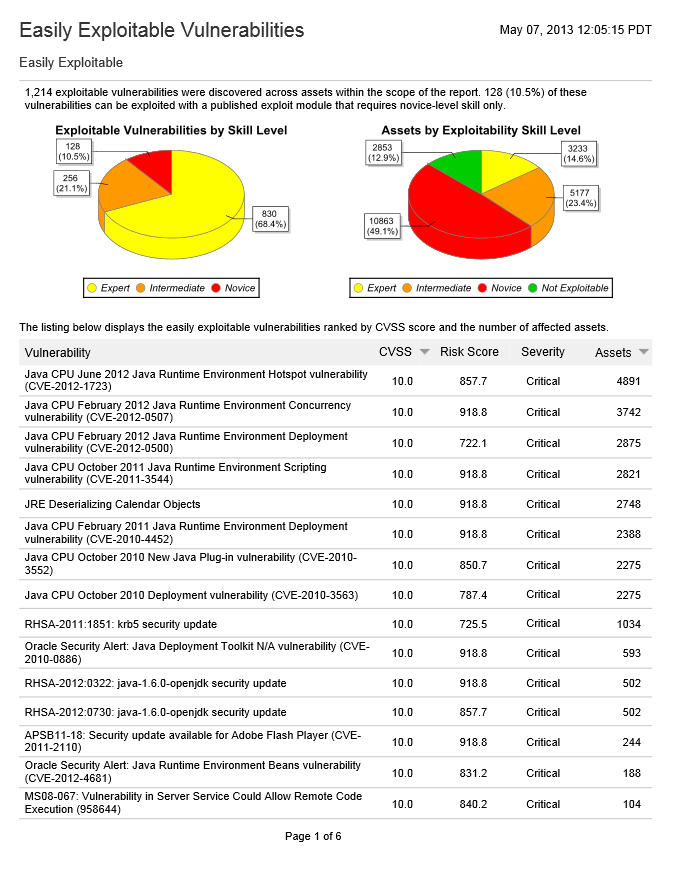
Also, check out the Easily Exploitable Vulnerabilities report which gives you a simple view of all vulnerabilities present in your environment that are susceptible to exploit by novice users: