One of the first steps in your penetration test is to map out the network, which is usually done with an active scan. In situations where you need to be stealthy or where active scanning may cause instability in the target network, such as in SCADA environments, you can run a passive network scan to avoid detection and reduce disruptions. A passive network scan stealthily monitors broadcast traffic to identify the IP addresses of hosts on the network. By initially running a passive scan, you can identify known hosts while evading network monitoring tools, such as intrusion detection systems (IDS). The data obtained from a passive network scan can be used to perform a targeted active scan with Metasploit's Discovery Scan.
Metasploit Pro's Passive Network Discovery MetaModule
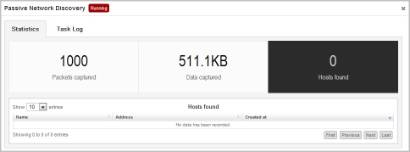
The Passive Network Discovery MetaModule available in Metasploit Pro runs a live packet capture on a specific network interface to capture DHCP requests and ARP requests. If you want to have more granular control over the packet capture or you want to reduce the size of the packet capture, you can use Berkeley Packet Filters (BPF) to specify the types of packets that the MetaModule captures.
The packet capture runs until it reaches the maximum Pcap file size or the time limit you have configured for the MetaModule. When the MetaModule run completes, it stores the captured data and generates a comprehensive report of its findings.
Sniffing the Network in Switched Networks
Most networks today are switched, which makes sniffing traffic harder. Unlike a hub, a switch only transmits the packets on the port of the target host instead of broadcasting it to the entire network. While this is great for minimizing traffic, it means that you'll only see packets that were meant for your machine, which defeats the point if you're trying to use network sniffing for discovering hosts on the network.
However, some manufacturers add ports for network analysis on the router that show you all traffic on the switch. Depending on the manufacturers, the ports are called Port Mirroring, Switched Port Analyzer (SPAN), or Roving Analysis Port (RAP). Depending on your model, you may have to switch on port mirroring in the switch's settings.