During a recent business trip in Boston, Tod and I sat down in a bar with the rest of the Metasploit team, and shared our own random alcohol-driven ideas on Metasploit hacking. At one point we started talking about hacking webcams. At that time Metasploit could only list webcams, take a snapshot, stream (without sound), or record audio using a meterpreter... normally that should be enough for most cases, but hey, wouldn't it be cool if you could actually chat with the compromised user face-to-face? You never know, right? Maybe you're monitoring one particular user during a penetration test, and you notice all kinds of unsafe things he's doing, and you have the urge to jump in and go "hey, I am watching you!" and lecture him about security? Yeah, you can do that now. But obviously the possibilities are endless with this new capability, so as always I encourage you to use your imagination :-)
The technology we're borrowing to achieve video chatting is called Web Real-Time Communications, or WebRTC for short. WebRTC is a free, open source project (hooray for open source!) that enables web browsers to do voice calling, video chat, and file sharing with simply JavaScript APIs and HTML5. Many applications or websites have already implemented WebRTC. To experience its awesomeness, you can go to sites like Webcam Toy and try it yourself.
Anyways, back to Metasploit hacking. So what we've done here is we implemented WebRTC as a Windows meterpreter feature. If you wish to chat with a compromised user, simply issue a command like the following:
meterpreter > webcam_chat
[*] Video chat session initialized.
A couple of things will happen under the hood when you use the webcam_chat command:
- It will first find a suitable browser on the remote machine: Chrome (version 23 or newer) or Firefox (version 22 or newer). Unfortunately Internet Explorer doesn't support WebRTC natively, so we'll see what Microsoft wants to do.
- Once a suitable browser is found on the remote machine, it will open that, and then initialize the video session.
- On your box (attacker), Metasploit will also find a suitable browser (again Chrome or Firefox), and then it will try to join the video session. When you're about to join, your browser will ask you to allow the webcam to turn on. Obviously you need to click yes/allow/share.
- And now let the fun begin.
Demonstrations
As an attacker, your interface has the basic features like a YouTube video. You can full-screen (either yours or the remote user's), mute, and control volume (default at 50%). It looks like this:
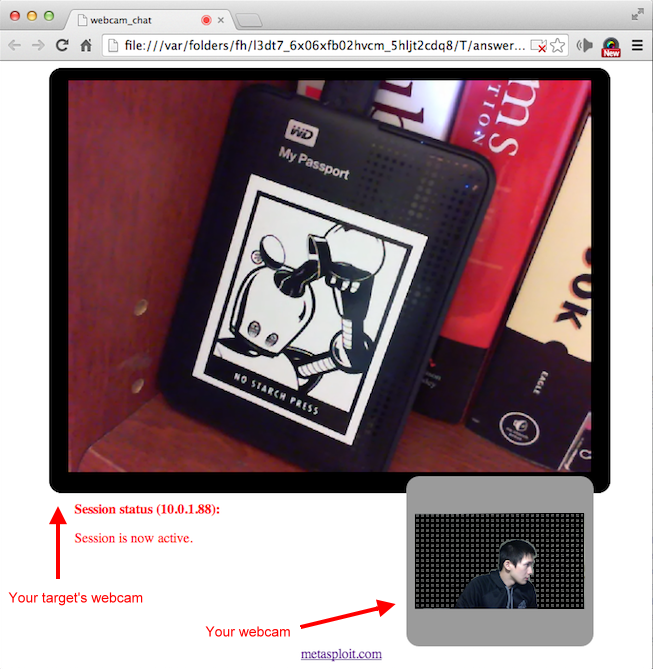
The remote user's interface is different. It does not let the user do full-screen or volume control (but if they know how to use the Developer's Tools, I guess they will figure out, except normally I don't think you need to worry about it from average users).
Defeat webcam privacy invasion
I know what you're thinking. It kind of sucks if someone breaks into your computer, and it's really creepy if they're using your webcam. Well, on the subject of how to prevent illegal hacking is a multi-billion dollar question, and as far as I can tell nobody has quite figured out the perfect solution. I can tell you what to do or buy all kinds of things within your budget, but if you so insist on clicking on a "Please download this file and run it to accept your free trip to Hawaii", then there isn't much we can do about it. Wait, that's not true -- I can run the webcam_chat command to get in your face and yell at you to stop clicking on things :-)
If you're concerned about people spying on you with your webcam, there IS something you can do about it. Nothing fancy, instead of doing your normal silly things with the webcam facing you, how about you simply cover it up? If you're feeling fancy, you can always buy one of those webcam covers like the following from Amazon:
