After many conversations with our AWS customers and the AWS CloudTrail team, we recently released our AWS CloudTrail integration to automatically support the most important log events our customers wanted to be monitoring across their AWS environments. We found that some of the most common need for notifications included:
- Starting, stopping, terminating, rebooting instances
- Creating or deleting security groups
- Creating and deleting users
- Updating user profiles
- Adding and removing groups
- Updating role and password policies
- Signing certificate upload or deletion
Logentries will alert you in real time when any of these events occur so that you can react appropriately. But what do you do if something suspicious actually occurs in your AWS environment? For example, you get notified that a new security group has been created opening up all of your servers’ so that they are accessible from any IP address…or someone has created a new user with admin privileges for example??
You’ll likely want to dig into the logs on your different Ec2 instances to check if anyone has logged in and exactly what they have been up to. To help with investigation at the instance level, today we announced our new Windows Security Event Integration. Logentries will automatically notify you in real time when important events occur in your windows event logs such as when audit logs are cleared; failed user log-ins; changes are made to audit policies and more. For more details on enabling these for your Logentries account check out our integration guide.
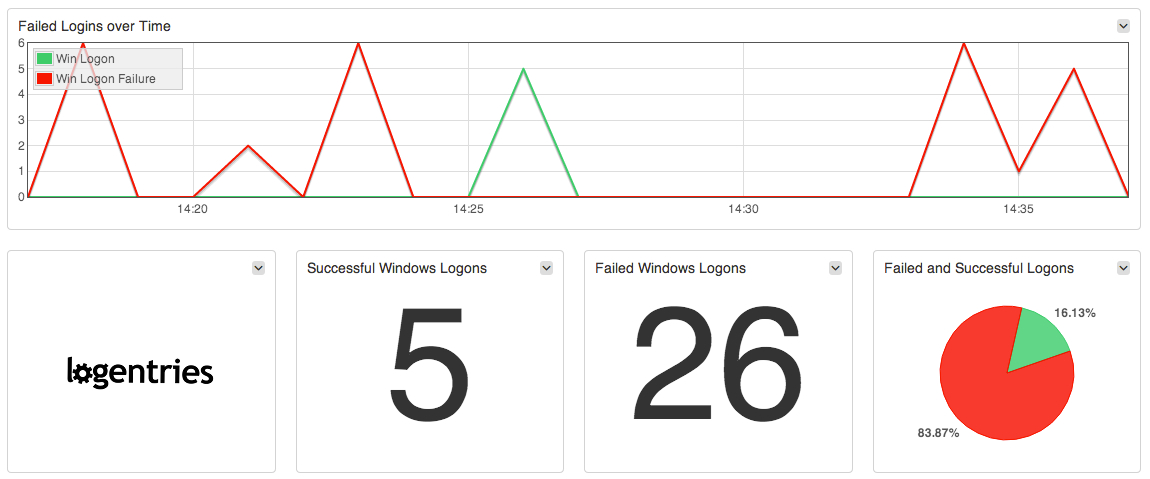
We’ve gotten feedback from across our Community, and from specific customers, to identify the relevant events that should be flagged or that you will want to know about when investigating security events in your Windows environment. Kirill Bensonoff, of ComputerSupport.com outlined the advantages of getting automated AWS CloudTrail and Windows event notifications together:
“Logentries enables our Operations team to know immediately when there are security events or potential issues. In addition to real-time alerting, we can also automatically correlate our Windows event notification with our AWS CloudTrail Log data to get a complete understanding of what is happening across our systems and users.”I also spoke with Brian Honan, CEO of BH Consulting on this topic recently, and in particular, the discussion focused on the challenges that organizations are facing as they move to the cloud – an environment that they are often not entirely familiar with. Brian is a security industry veteran and expert in the field of information security – in fact he’s literally written the book on The Cloud Security Rules. According to Brian, “Recent security breaches and subsequent investigations highlight the absolute need for effective proactive log monitoring to detect respond and prevent major security incidents. And in particular with corporates moving to the cloud and relying more on third party vendors to support their systems, having the ability to monitoring logs in those systems has become even more essential.”
One further complexity when dealing with Windows Event Logs can also be in simply understanding what gets logged where as well as understanding the event structure. Since Windows Vista there are now two categories of event logs in Windows. Windows Logs and Applications and Services Logs logs. The Windows Logs category includes the logs that were available on previous versions of Windows: the Application, Security, and System logs. It also includes two new logs: the Setup log and the ForwardedEvents log. Windows logs are intended to store events from legacy applications and events that apply to the entire system. These logs store events from a single application or component rather than events that might have systemwide impact. For a deeper dive on the different logs contained in each category, check out the Microsoft docs on event logs.
The windows event logs will also capture some useful info such as:- Source: The software that logged the event.
- Event ID: A number identifying the particular event type. The Event ID and the Source can be used by product support representatives to troubleshoot system problems.
- Level: A classification of the event severity. System and application logs have ‘Information’, ‘Warning’, ‘Error’ and ‘Critical’ severity levels. The security log has ‘Success Audit’ and ‘Failure Audit’ severity levels.
- User: The name of the user on whose behalf the event occurred.
- Computer: The name of the machine on which the event occurred.
- KeyWords: A set of categories or tags that can be used to filter or search for events. Examples include “Network”, “Security”, or “Resource not found.”
With the new Logentries Windows Event Log integration alerts can easily be applied to your relevant logs and events such that you can begin to easily track important system issues and spot suspicious events and trends.Our intention is to make security analysis easier for your cloud environments, so check it out and let us know what you think!
