_[Edited 10:05 AM PDT, October, 2014 for the Nexpose 5.10.13 release]_
[Edited 10:05 AM PDT, September 26, 2014 for the Nexpose 5.10.11 release]
A severe vulnerability was disclosed in bash that is present on most Linux, BSD, and Unix-like systems, including Mac OS X. The basis of this vulnerability (nicknamed Shellshock) is that bash does not stop processing after the function definition, leaving it vulnerable to malicious functions containing trailing commands. Common Vulnerabilities and Exposures (CVEs) associated with this flaw are identified as CVE-2014-6271, CVE-2014-7169, CVE-2014-7186, CVE-2014-7187, CVE-2014-6277, and CVE-2014-6278. Learn more about bashbug/shellshock.
The Nexpose 5.10.13 update provides authenticated and unauthenticated checks for CVE-2014-6271, and authenticated checks for CVE-2014-7169, CVE-2014-7186, CVE-2014-7187, CVE-2014-6277, and CVE-2014-6278. Note: This coverage requires a product update as well as a content update. See the release notes for more details and a list of covered operating systems.
You can create a scan template that will focus your scan on these checks, to the exclusion of anything else. This will help you focus on how you are affected by this particular vulnerability. After the 5.10.13 update, take the following steps:
Create a custom scan template.
- In the Nexpose Security Console Web interface, click Administration. On the Admin page, click the manage link for Templates, or just type the keyboard shortcuts TM. This opens the Scan Templates panel.
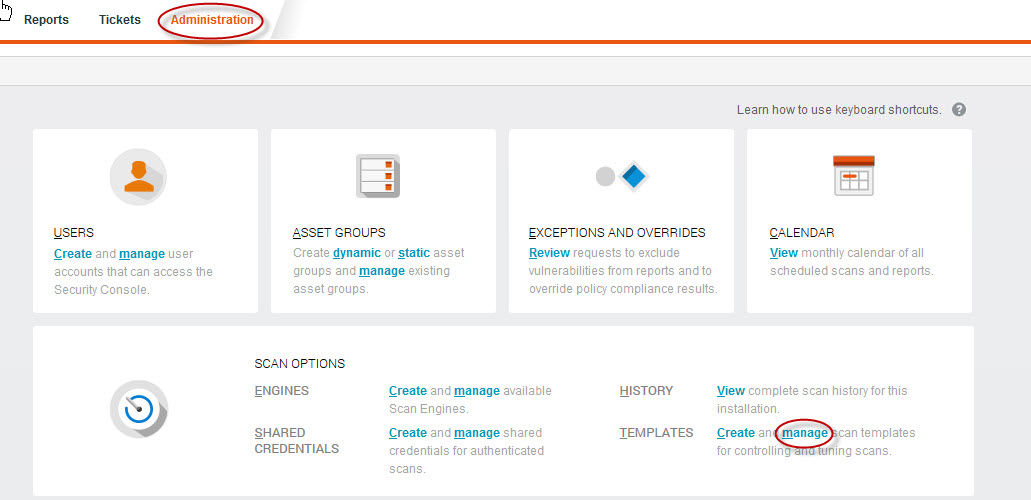
- Find the Full audit template and select the Copy icon.
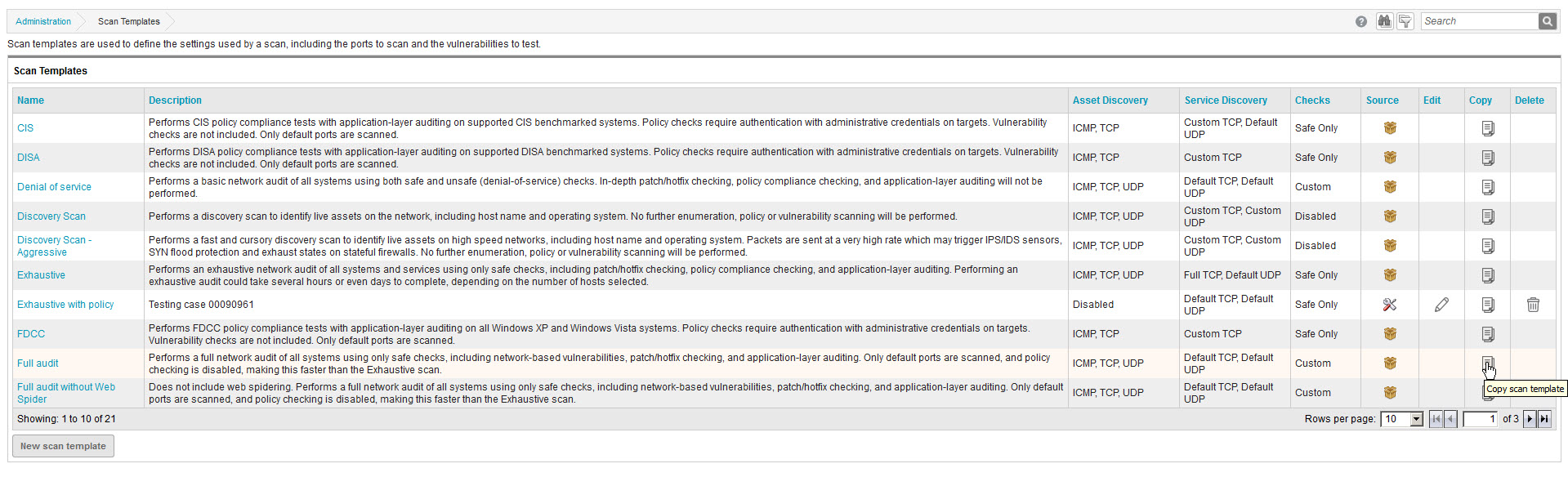
- Ensure the Vulnerabilities and Web Spidering options are selected. Clear the Policies option to focus the template on the checks specific to this vulnerability (which are not policy-related).
- Edit the scan template name and description so you will be able to recognize later that the template is customized for shellshock/bash bug.
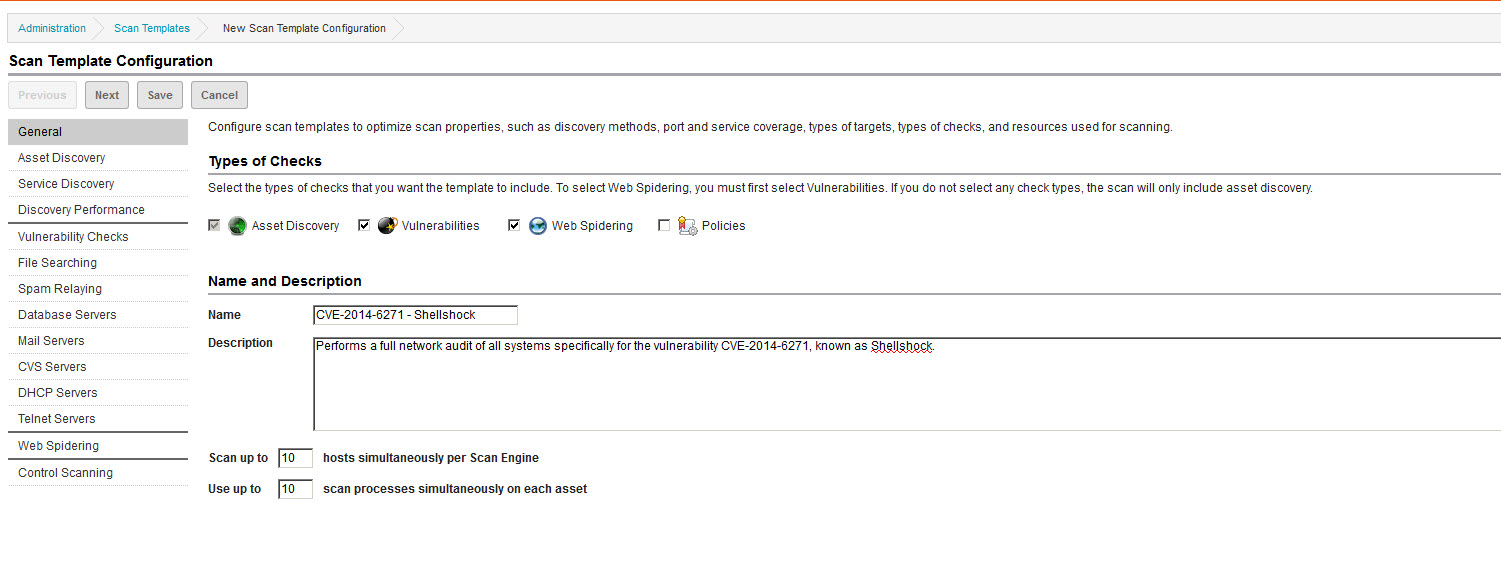
Select only the relevant vulnerability checks.
- Go to the Vulnerability Checks page. First, you will disable all checks, check categories, and check types so that you can focus on scanning exclusively for items related to this issue.
- Expand the By Category section and click Remove categories.
- Select the check box for the top row (Vulnerability Category), which will auto-select the check boxes for all categories. Then click Save. Note that 0 categories are now enabled.

- Expand the By Check Type section and click Remove check types.
- Select the check box for the top row (Vulnerability Check Type), which will auto-select the check boxes for all types. Then click Save. Note that 0 check types are now enabled.

- Expand the By Individual Check section and click Add checks.
- Enter or paste CVE-2014-6271 in the Search Criteria box and click Search. Select the check box for the top row (Vulnerability Check), which will auto-select the check boxes for all types. Then click Save.
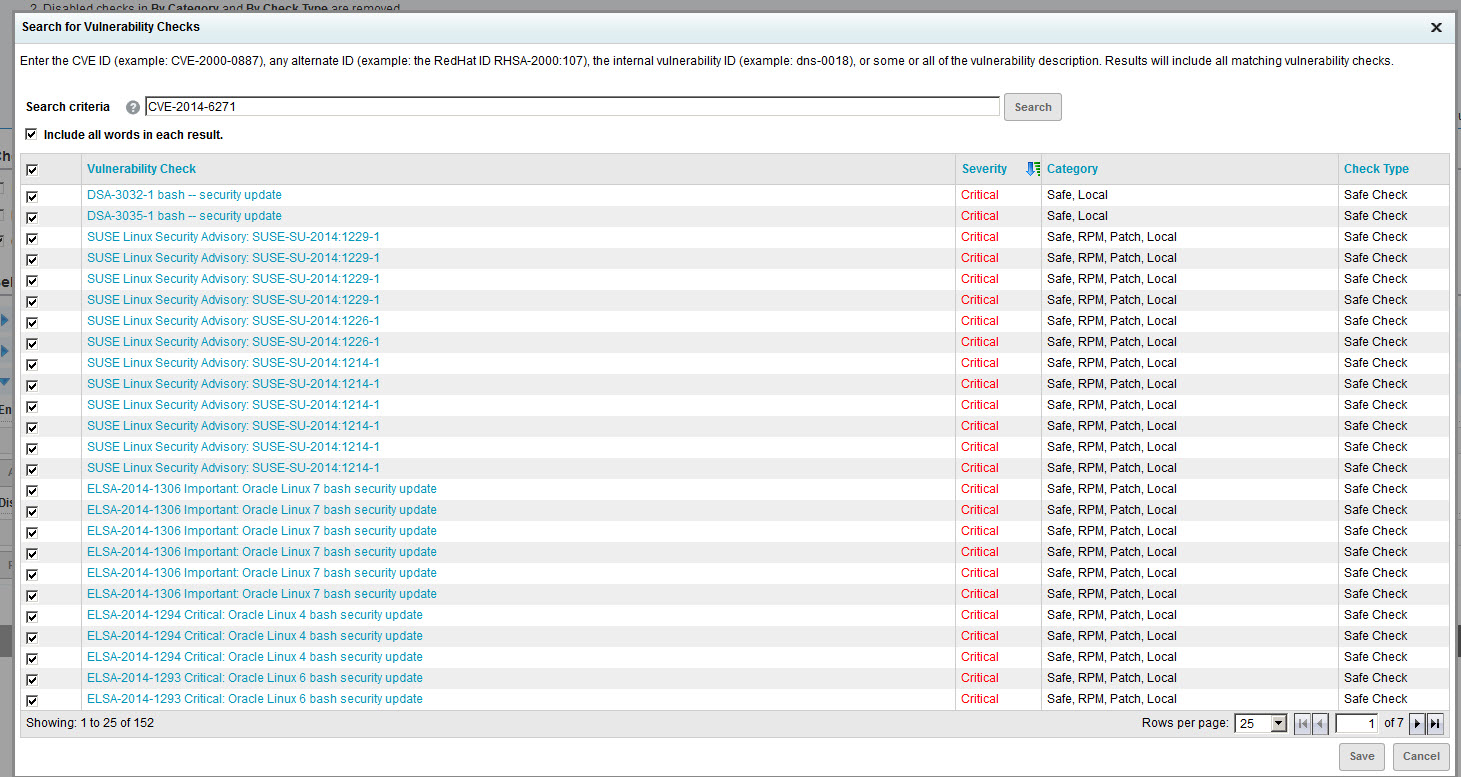
- Repeat step 7 for CVE-2014-7169, CVE-2014-7186, CVE-2014-7187, CVE-2014-6277, and CVE-2014-6278. In many cases, these vulnerabilities will already be selected because they are linked to CVE-2014-6271. Select any checks that are not already selected. For example, there are some additional checks associated with CVE-2014-6277; apply those.
- Save the scan template.
Create or edit a site to include:
- the new custom scan template
- credentials for the authenticated vulnerability checks