IT professionals set up service accounts to enable automated processes, such as backup services and network scans. In UserInsight, we can give you quick visibility into service accounts by detecting which accounts do not have password expiration enabled. Many UserInsight subscribers love this simple feature, which is available the instant they have integrated their LDAP directory with UserInsight. In addition, UserInsight has several new ways to detect compromised service accounts.
To do their job, service accounts often have to be given access to a large number of hosts on the network, making them a key target for attacks. Even when service accounts use long passwords, they can be hijacked using attacker honeypots and pass-the-hash attacks. We've seen this time and time again in penetration tests, and it's surprisingly effective.
When we researched how to detect compromised service accounts we realized that they typically only authenticate from one or two source assets, e.g. a backup server. On the flip-side, we often see service accounts authenticate to a large number of assets. Based on this research, we've added a new incident type that triggers when UserInsight observes a new source asset for a service account, in other words, a service account authenticating from a particular asset for the first time.
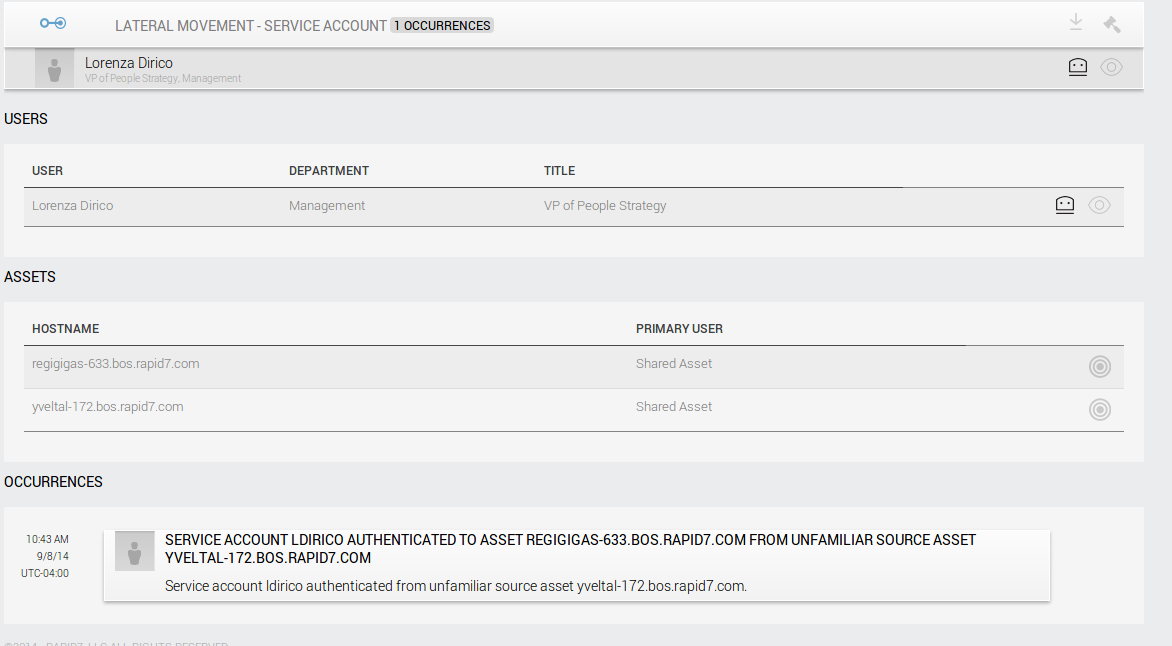
Note: The data in this screen has been anonymized/randomized and the service account is therefore named after a person, not a service.
Another way UserInsight is already detecting compromised service accounts is to detect service accounts trying to access the network from the Internet. The incident alert type "Ingress From Service Account" triggers when a service account ingresses to the network through VPN, ActiveSync, OWA and other external-facing services. The concept here is that service accounts are generally not real user accounts and should only be used internally.
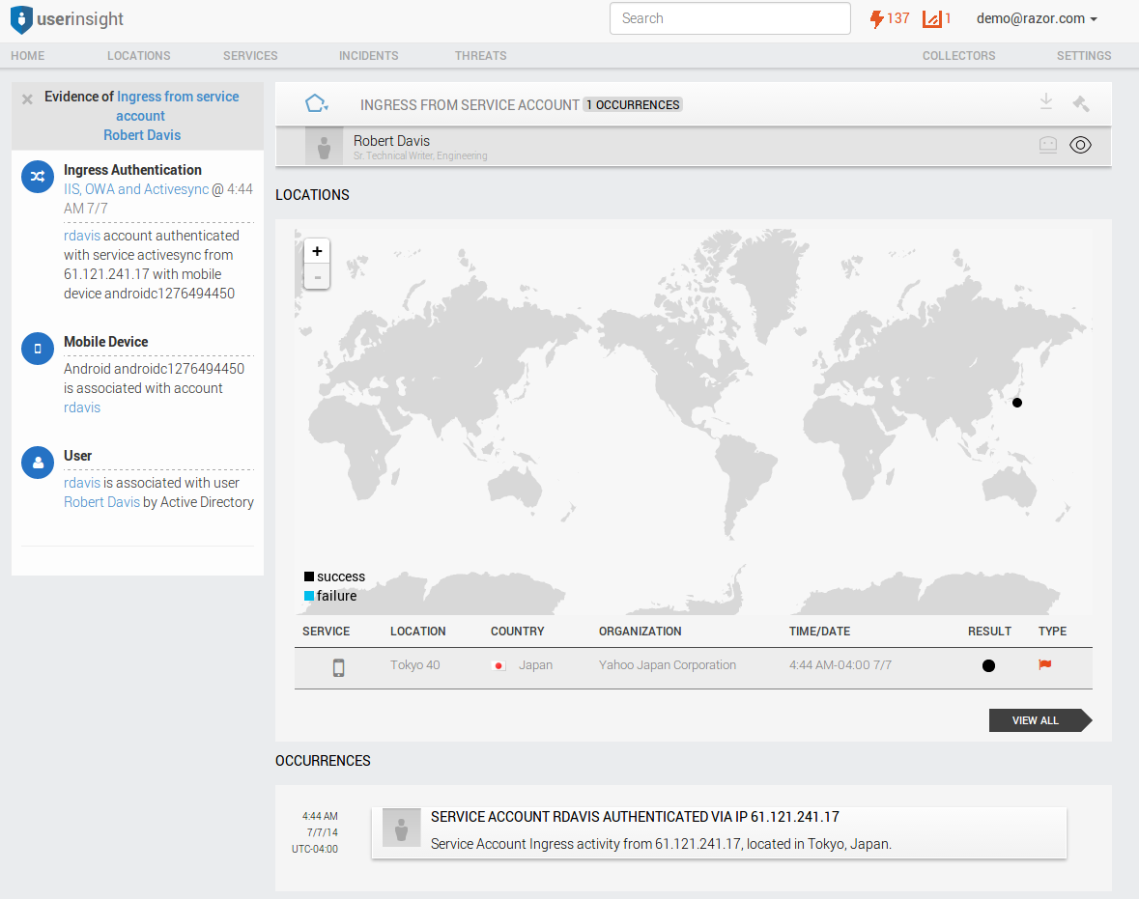
Note: The data in this screen has been anonymized/randomized and the service account is therefore named after a person, not a service.
In addition to service account specific alert types, UserInsight has many different ways to detect both local and domain credential abuse. Monitoring domain controller logs alone will not be effective in detecting these because this misses the prevalent use of pass-the-hash attacks using stolen credentials. UserInsight leverages the scanning technology from Rapid7 Nexpose to obtain endpoint logs and other information without requiring the deployment of an endpoint agent.