Based on a common pain and your positive feedback on last month's blog post entitled "Don't Be Noisy", we have started significantly expanding the scope of our noise reduction efforts. Rather than reinvent the great technology that intrusion detection/prevention systems (IDS/IPS), firewalls, and anti-virus products offer, we are aiming to provide an understanding of the massive amounts of data produced by these solutions.
Most monitoring solutions are too noisy to follow up on each alert
Like with noise-canceling headphones, you sometimes need to tune out the noise to successfully focus on what's important to you. One message we consistently hear from security teams is that they stand by most of their high maintenance investments in detection and prevention, but they just do not have the time to determine the root cause of every alert. For the organizations with the means, almost every alert from a , IPS, or other monitoring solution can be investigated and each system's rules constantly refined by the staff solely dedicated to optimizing them. However, these well-funded IR teams capable of providing this constant attention are rare, so we find that most people have to get very creative in how they decide which alerts warrant a few hours of investigation. Let me give one example of noise just for the three technologies I named above:
IDS/IPS: 20,000 alerts per day is more than most incident responders can handle
The best example I can give around an IDS generating noise is to paraphrase a customer that asked us for help with it:
I am the sole person that digs into these alerts and I see no less than twenty thousand (20,000!) in a given day. My process is to ignore anything rated 'low' or 'medium', then look for signature descriptions that have not consistently proven to be false positives in prior investigations. Often, I get even more concerned when the signature is tied to a few different internal IP addresses, so I put those at the top of the list. Nearly every time, however, these turn out to be the same individual moving a laptop from WiFi to a wired connection. I would not call them all 'false positives' because some turn out to be a little risky, but if I had just known it was the same person responsible for some more cutting-edge research, I would have been a lot less concerned.
Firewalls: Tens of thousands of events per minute are quite normal - but not useful
As the de facto starting brick for every organization's perimeter wall, firewalls are commonly flooding anything that listens to syslog on your network with tens of thousands of events per minute. A 'deny' does not translate to an alert from most systems and a single attempted download on a blocked port or IP address range can result in hundreds of denies, so the pure volume of denies is a lousy indicator of how concerning the activity is. On top of that, [you may start to see a pattern here] the traffic is all logged primarily with the internal and external IP addresses, so a large cluster of firewall denies can appear to be malicious behavior spreading across your network, when in fact, it is just someone like me that brings his laptop from conference room to desk to an office in another country over the course of three days.
Anti-virus: Finding the user connected to a malware alert can be a headache
Everyone loves to pick on A/V today as being ineffective, but that has nothing to do with the pain I want to discuss. In the surprisingly small number of organizations that have reliable centralized reporting for their endpoint protection solutions, it takes a great deal of digging to figure out which asset is infected and (again) to whom it belongs. Unless it looks to be spreading across the network, the modus operandi is to assume it was effectively quarantined by endpoint protection and spend your time looking into more suspicious alerts elsewhere.
Rapid7 UserInsight cancels the noise so you only hear alerts that are real
Our noise reduction approach is rather simple: tie all of this activity back to the users and point out the trends that help peel back the noise and see the signals. UserInsight is not the first solution to ingest data from a wide array of security infrastructure, but correlating activity with the responsible user in your organization is at the product's core. Similar to your unconscious brain automatically handling walking and eating for you, UserInsight automatically applies user context to all activity it processes before presenting any information or alerting. This means that the new functionality we had to build was to effectively process a wide variety of data types and present trends that can help you dig into the root cause of your tens to hundreds of thousands of alerts.
Here is a real world example:
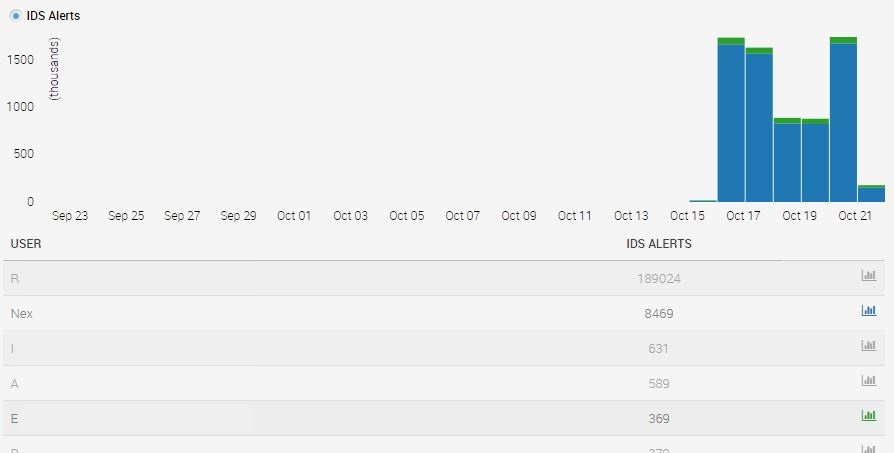
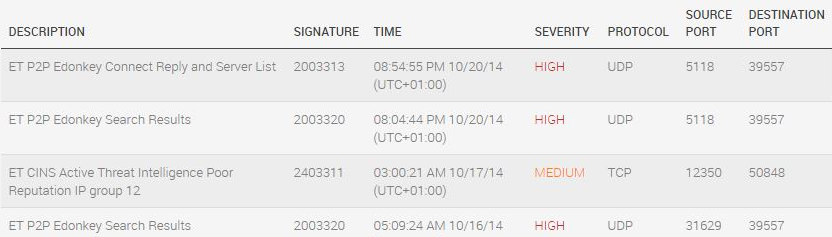
This chart shows the users that were the second and fifth noisiest IDS alert generators in Rapid7 in the past week. The blue represents a Nexpose scanner - no shock that it creates a great deal of noise in an IDS; I would be more concerned if it wasn't causing alerts in a default IDS. By comparison, the fifth noisiest user is the small amount of green on the top of the chart, so it would easily get lost in the noise. However, if I click on that (high-profile) user, I find the alerts shown in the screen shot below [a few columns are snipped because security says so]. This is the type of information you would hate to miss. High and medium alerts on multiple ports for a high profile user. They may turn out to be false positives, but investigating them is time much better spent than chasing down your Nexpose scanner.
We can do this for any data, so please let us know which security solutions you have in place right now that are providing a lot of data but where you are having trouble making sense of what's real. We already have the trending around vulnerabilities per user and failed vs. successful authentications.
Eat our own dog food, then release
This is currently in "dog food mode", so it will be rolled out to all customers extremely soon. As in, click on the "Active Users" link on your dashboard and you will probably see it by the time you finish reading this. Seriously. We are all about continuous integration here. The only problem our customers have with our smooth release process if that they sometimes don't hear about new features straight away, which is why we're blogging so much about new features.