You may fear that cloud services jeopardize your organization's security. Yet, your business relies on cloud services to increase its productivity. Introducing a policy to forbid these cloud services may not be a viable option. The better option is to get visibility into your shadow IT and to enable your business to use it securely to increase productivity and keep up with the market.
Step one: Find out which cloud services your organization is using
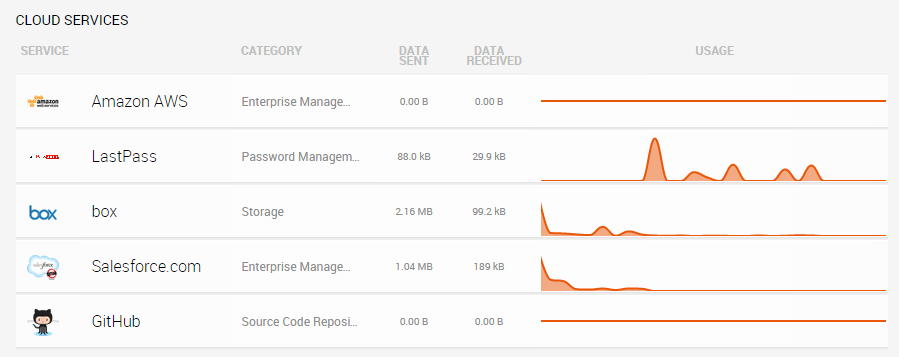
First, you'll want to figure out what is actually in use in your organization. Most IT departments we talk to underestimate how many cloud services are being used by a factor of 10. That's shocking. The easiest way to detect what services are commonly in use is by leveraging Rapid7 UserInsight, a solution for detecting and investigating security incidents from the endpoint to the cloud. For this step, UserInsight analyzes your web proxy, DNS, and firewall logs to outline exactly what services are in use and which users are subscribing to them. This is much easier than sifting through raw log files and identifying which cloud service may be behind a certain entry.
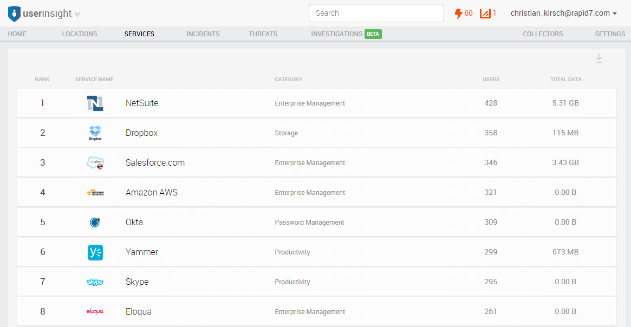
Step two: Have a conversation with employees using these services
Knowing who uses which services enables you to identify the users and have a conversation with them about why they use the service and what data is shared with this service. UserInsight makes it easy to correlate web proxy, DNS, and firewall activity to a user because it keeps track of which user had which IP address on the corporate LAN, WiFi, and VPN, All of this information is just one click away.
Based on this information, you can:
- Move the users to a comparable but more secure service (e.g. from Dropbox to Box.com),
- Talk with users about why a certain service is not suitable for use on the corporate network (e.g. eDonkey), and
- Enable higher security on existing services by consolidating accounts under corporate ownership and enabling stronger monitoring
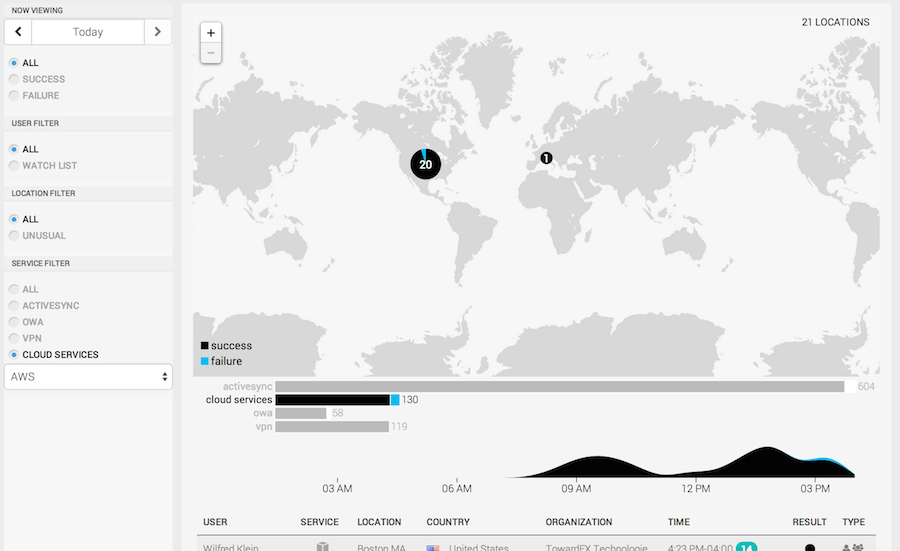
Step three: Detect compromised accounts through geolocation of cloud and on-premise accounts
Compromised credentials are leveraged in three out of four breaches, yet many organizations have no way to detect how credentials are being used. UserInsight can detect credential compromise in on-premise systems and in the cloud. One way to do this is through geolocation. If a user's mobile device accesses email in New York and then a cloud service is accessed from Germany within a time span of 20 minutes, this indicates a security incident that should be investigated.
UserInsight integrates with dozens of cloud services, including Salesforce.com, Box.com, and Google Apps to geolocate authentications even if they happen outside of the corporate network. The solution correlates not only cloud-to-cloud authentications but also cloud-to-on-premise authentications, giving you much faster and higher quality detection of compromised credentials. With Amazon Web Services (AWS), UserInsight can even detect advanced changes, such as changed passwords, changes to groups, and removed user policies. Read more about UserInsight's ability to detect compromises of AWS accounts.
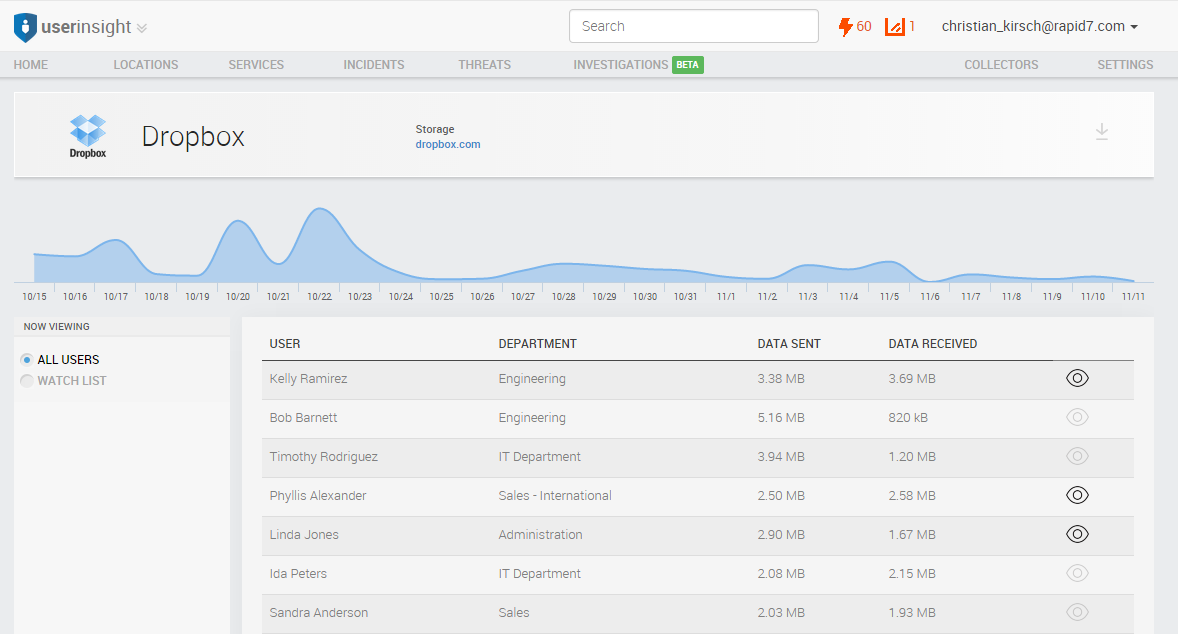
Step four: Investigate potential exfiltration to cloud services
If attackers compromise your corporate network, they often use cloud storage services to exfiltrate information, even if the company is not even using a particular service. When investigating an incident that involves a certain compromised user, you can review that user's transmission volume to figure out if and how much data was exfiltrated this way. UserInsight makes this exceedingly easy, breaking volume down by user and enabling you to see the volume on a timeline.