ControlsInsight helps organizations measure how well critical security controls are deployed and configured throughout the enterprise. Yet, as hard you may try, it's extremely difficult to protect every asset on your network perfectly, and it's often necessary to prioritize "misson-critical" assets that store important or sensitive business data. Clearly, securing the laptop computer of Sally, the chief financial officer, is much more important than securing Joe the intern's laptop, which probably holds more cat pictures than financial models.
The asset filtering feature in ControlsInsight, based on Rapid7 RealContext, is one way to track the status of controls for groups of assets that have been tagged as critical. But what about a scenario when you want to verify the configuration of controls for a particular asset? While the Assets tab lists all assets being assessed, if you know the IP address or host name of the asset you'd like to analyze, the search functionality in ControlsInsight will quickly get you the information you need.
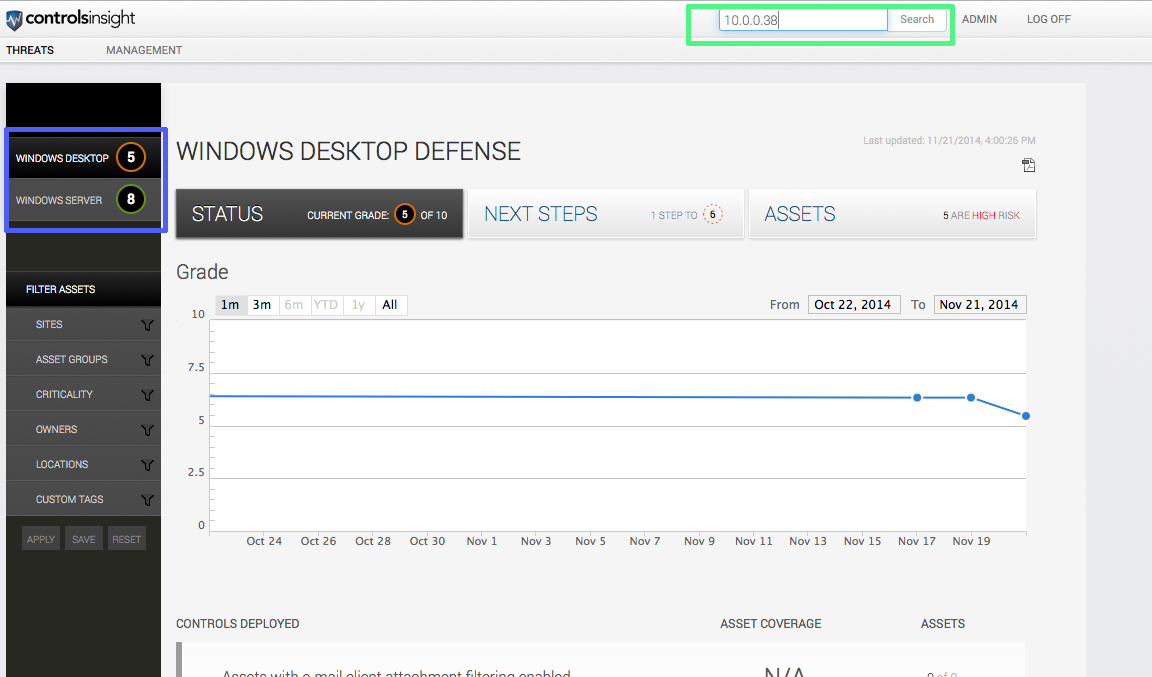
Let's say we know that Sally's computer has the IP 10.0.0.38 on our network. Start by selecting the type of assets you'd like to analyze (we've selected Desktop assets in the example), and entering the IP address in the search box:
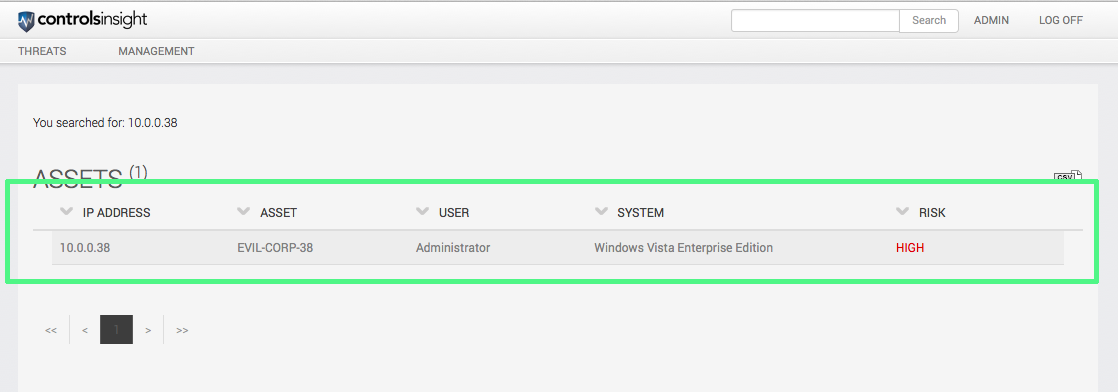
After selecting the asset that represents Sally's desktop, we can see that she's still using Windows Vista Enterprise Edition (not seeing the assets you expect? check out our blog post on the subject).
Oh no! It looks like Sally is running a high-risk system. She's one of the last people we want running a high-risk system, so let's do something about it. While we might want to have a sit-down with Sally about her choice of operating system, our first order of business is to make sure Sally is as well-protected as possible while she goes about her work. Let's click on the asset to find out what we can do to help.
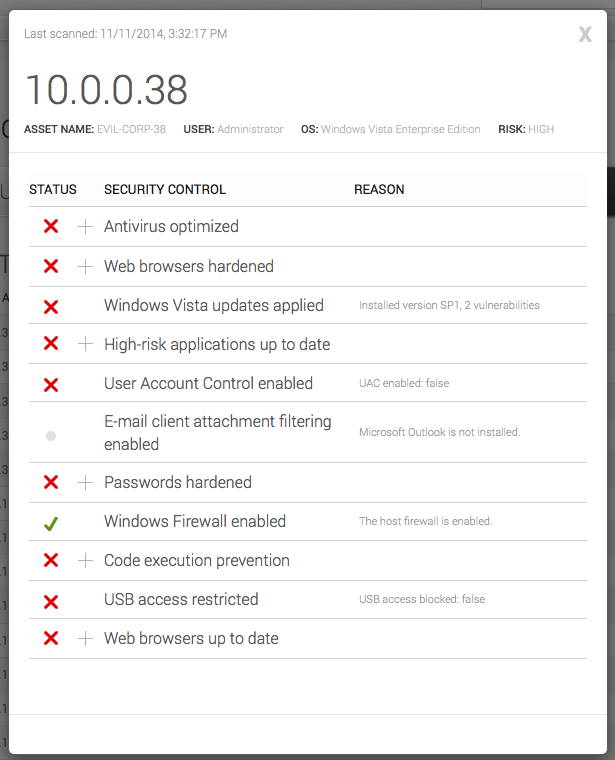
So it looks like there's lots of room for easy improvement of Sally's computing environment. Note that if rules like this are being tripped on one employee's computer, it's often symptomatic of not enough safeguards being in place company-wide, relating to things like antivirus operation, web browser updating, and default settings for fresh Windows installations. The Next Steps tab in ControlsInsight helps to prioritize corrective action at the enterprise level, but sometimes it's necessary to address a deficiency on a particular asset first. Let's look at the list from Sally's laptop again with a focus on some of the easy-to-correct controls.
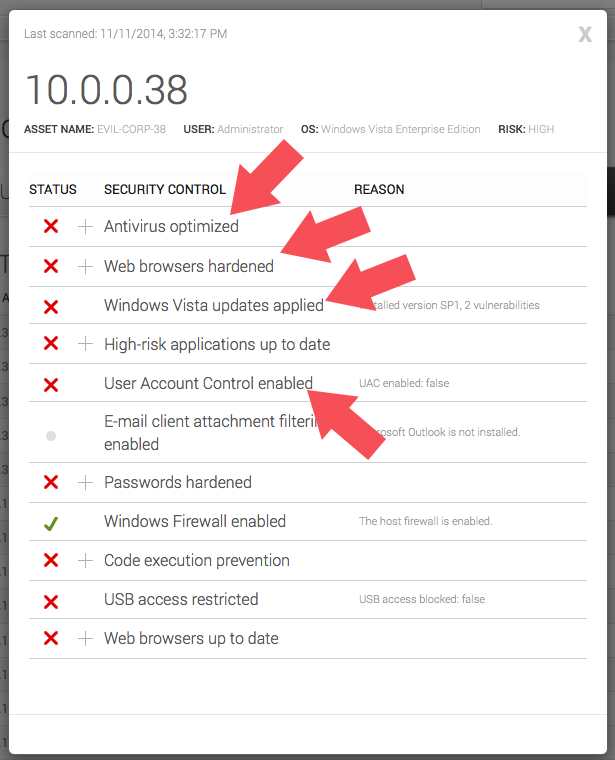
System updates, antivirus, and web browser updates are some of the cornerstones of a good user defense. They're also fields that users are very familiar with, so they're a good place to start when securing users on your network.
ControlsInsight provides you with a detailed breakdown of what exactly is wrong with the asset and the specifics of checks that have failed. Let's expand some of these controls to see what's wrong:
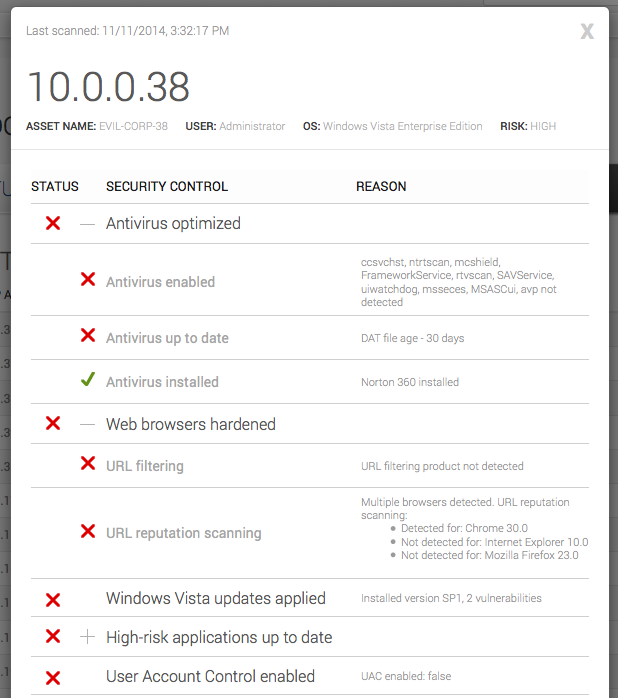
After expanding some of the controls, we've got a clear view of the problems that were found. Let's look at some of the remediation steps that could solve them:
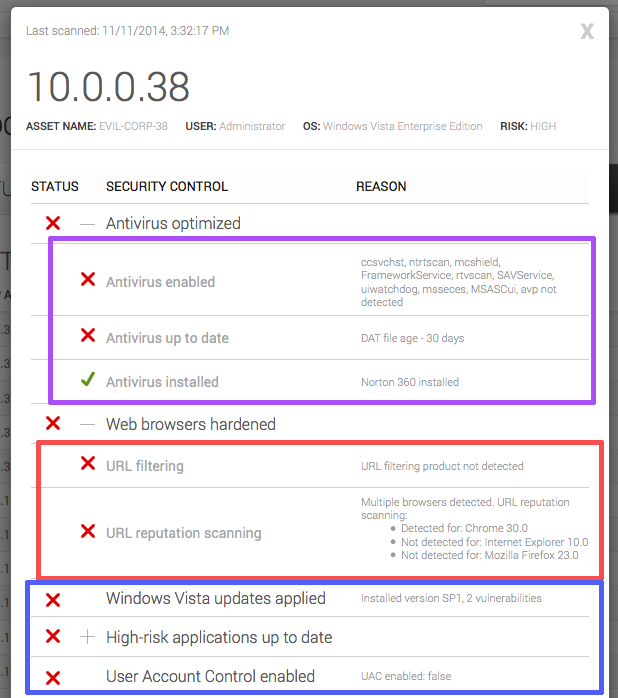
Fixing antivirus
It looks like Sally has an antivirus program (in this case, Norton 360) installed, which is great news! It looks like it hasn't been updated in a while though. There are a few ways we can fix this:
- Ensure local updating is turned on in the IT team's base Windows images/installations.
- Talk to Sally about why she disabled her antivirus updating, and see what we can do/change to make it easier for her to leave it on (and update Sally's computer while we're there).
Hardening web browsers on your network
It looks like Sally's web browsers are a little less-than-perfect with regards to URL filtering and reputation scanning. As the web is one of the primary transmission vehicles for all sorts of malicious code, let's go over a few simple things that we can do to secure Sally's web experience:
- A good practice to increase web security on your network is to pre-install or provide a "trusted" web browser version/build. This way, we can change the default state of web browsers on the network from vulnerable/default to less-vulnerable/customized, and reduce the support surface for IT from every-browser-version-ever to a few versions (that may change over time). While there is some IT overhead to supporting a "trusted" version (and making sure that they keep up with updates to the browsers), it's often much more cost effective to spend properly on IT than face a data breach.
- Another good practice for hardening web browsers is to roll out a URL filtering strategy/default file along with turning on reputation scanning for your users, in the browsers your users use the most often (whether that be Firefox, Safari, Opera, or any of the tens of browsers out there).
System updates
In addition to Antivirus and web browser issues, it looks like the computer that Sally is running on has an older version of Windows Vista, which has UAC (User Account Control) disabled. While it is very difficult to corral all the high risk applications a user might have running on the system, it's often worth investing in updating the platform the applications run on (which in this case in Vista) to provide protection across the board. Here are some steps IT could take to fix these controls:
- Talk to Sally about whether she disabled UAC (and if so, why) and update Sally's computer with a newer Service Pack, and enable User Account Control.
- Update the Windows fresh install images being used at the company to ensure that UAC and newer Service Packs are always installed for users.
After fixing these vulnerabilities on Sally's computer, we can enable her to get back to doing what she does best, securely and safely.
Remember that security is often very much a human issue as it is a technological one. Treat your end-users with courtesy and respect, and be empathetic to their needs, while protecting them from the big bad world out there.
Anything you've done in your company that you've found especially helpful in managing mission-critical assets? If so, tell us about it in the comments below!