A severe vulnerability was disclosed in the F5 implementation of TLS 1.x that allows incorrect padding and therefore jeopardizes the protocol's ability to secure communications in a way similar to the POODLE vulnerability.
The Nexpose 5.11.10 update provides coverage for this vulnerability, which has been given the identifier CVE-2014-8730. Learn more about CVE-2014-8730.
Note: This coverage requires a product update as well as a content update.
Note: This coverage requires that unsafe checks be enabled. These checks can verify vulnerabilities that threaten denial of service attacks, which render a system unavailable by crashing it, terminating a service, or consuming services to such an extent that the system using them cannot do any work. However, the nature of these checks means that they may cause disruption in your systems, including crashing systems or leaving them in an indeterminate state. You should run scheduled unsafe checks against target assets outside of business hours and then monitor them for abnormalities after scanning. It is also a good idea to run unsafe checks in a pre-production environment to test the resistance of assets to denial-of-service conditions.
In some cases, due to the high profile nature of this vulnerability, you may want or need to run rapid scans that check for CVE-2014-8730 exclusively. There are advantages and disadvantages to this “fast focused” approach, namely; scanning for only CVE-2014-8730 will allow your organization to quickly assess its risk exposure, the disadvantage is that if you modify your existing sites to scan only for this one vulnerability, you'll likely skew the historical data on these sites. If you want to proceed with the focused approach, you can create a scan template that will focus your scan on CVE-2014-8730, to the exclusion of anything else. If your license allows you may want to create a onetime use set of sites.
To create the custom scan template, after the 5.11.10 update, take the following steps:
Create a custom scan template.
- In the Web interface, click Administration. On the Admin page, click the manage link for Templates, or just type the keyboard shortcuts TM. This opens the Scan Templates panel.
- Find the Full audit without Web Spider template and select the Copy icon.
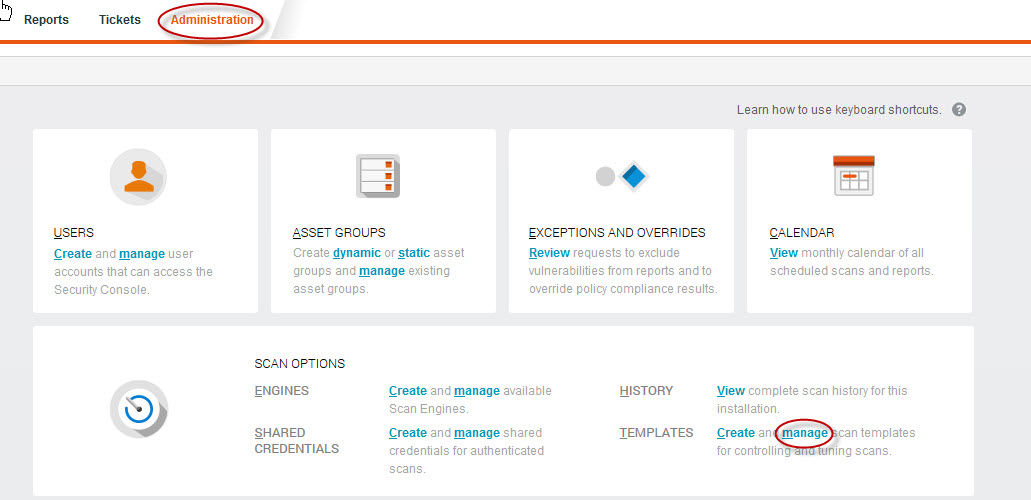
- Ensure the Vulnerabilities option is selected. Clear the >Policies option and ensure the Web Spidering option is cleared to focus the template on the checks specific to this vulnerability.
- Edit the scan template name and description so you will be able to recognize later that the template is customized for CVE-2014-8730.
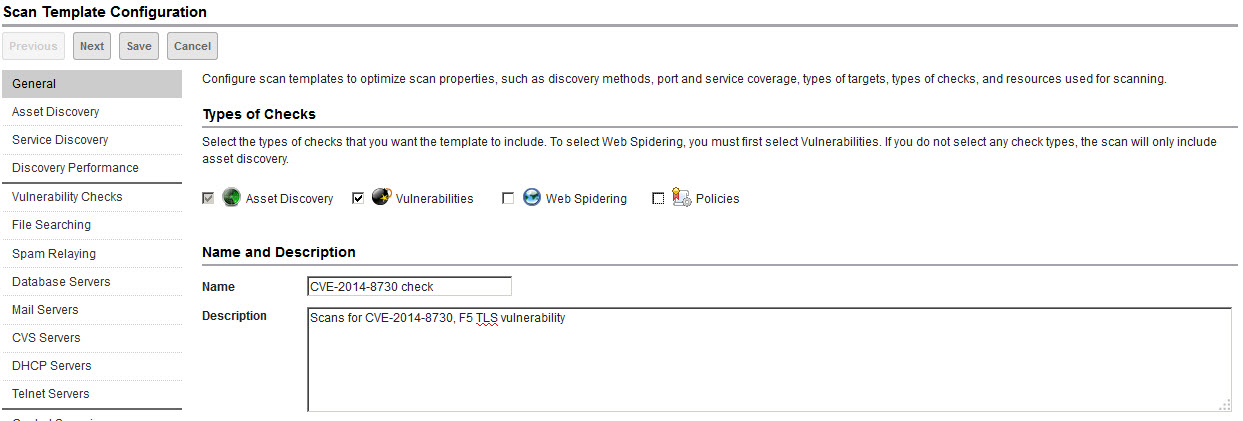
5. In the Vulnerability Checks page, select Perform unsafe checks.
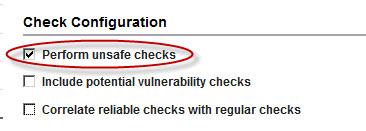
6. A warning will appear explaining that running unsafe checks may cause disruptions in your systems. Click Yes.
Select only the relevant vulnerability checks.
- On the Vulnerability Checks page, you will disable all checks, check categories, and check types so that you can focus on scanning exclusively for CVE-2014-8730.
- Expand the By Category section and click Remove categories.
- Select the check box for the top row (Vulnerability Category), which will auto-select the check boxes for all categories. Then click Save. Note that 0 categories are now enabled.
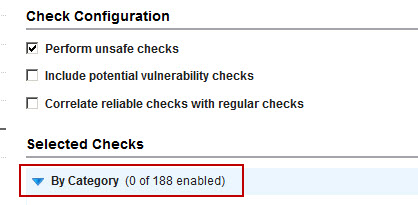
- Expand the By Check Type section and click Remove check types.
- Select the check box for the top row (Vulnerability Check Type), which will auto-select the check boxes for all types. Then click Save. Note that 0 check types are now enabled.
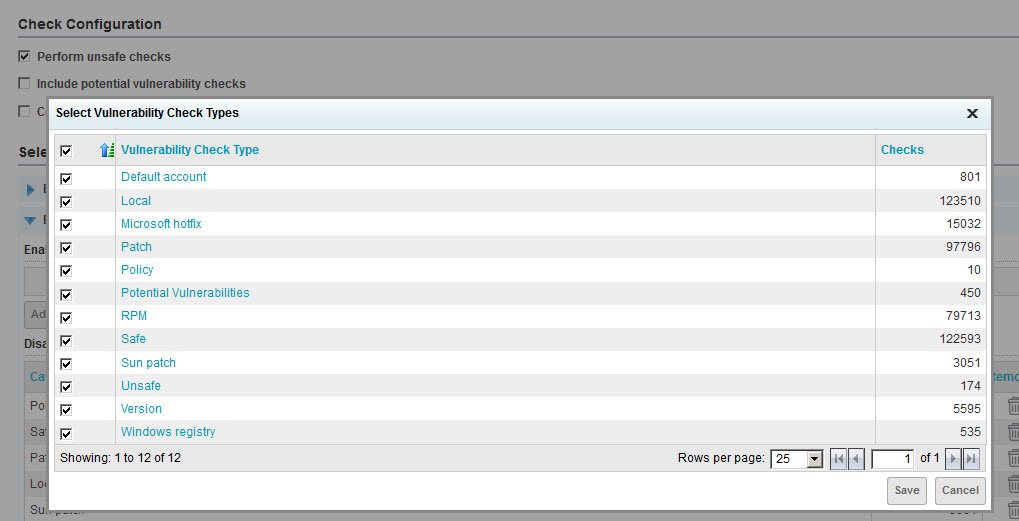
- Expand the By Individual Check section and click Add checks.
- Enter or paste CVE-2014-8730 in the Search Criteria box and click Search. Select the check box for the top row (Vulnerability Check), which will auto-select the check boxes for all types. Then click Save.
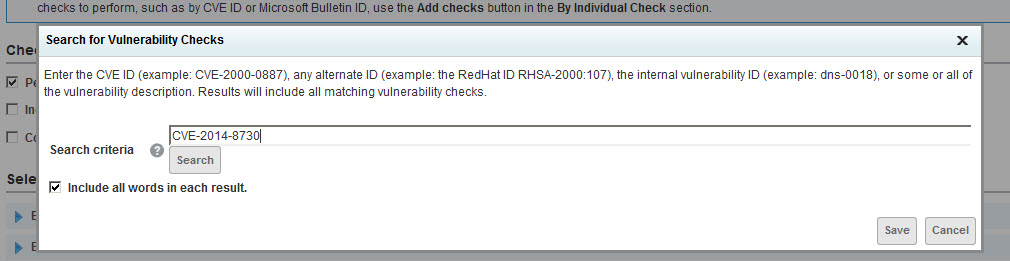
- Save the scan template.
Create or edit a site to include:
- the new custom scan template
Start scanning!