Introduction
Automated tank gauges (ATGs) are used to monitor fuel tank inventory levels, track deliveries, raise alarms that indicate problems with the tank or gauge (such as a fuel spill), and to perform leak tests in accordance with environmental regulatory compliance. ATGs are used by nearly every fueling station in the United States and tens of thousands of systems internationally.
Many ATGs can be programmed and monitored through a built-in serial port, a plug-in serial port, a fax/modem, or a TCP/IP circuit board. In order to monitor these systems remotely, many operators use a TCP/IP card or a third-party serial port server to map the ATG serial interface to an internet-facing TCP port. The most common configuration is to map these to TCP port 10001. Although some systems have the capability to password protect the serial interfaces, this is not commonly implemented.
Approximately 5,800 ATGs were found to be exposed to the internet without a password. Over 5,300 of these ATGs are located in the United States, which works out to about 3 percent of the approximately 150,000 [1] fueling stations in the country.
An attacker with access to the serial port interface of an ATG may be able to shut down the station by spoofing the reported fuel level, generating false alarms, and locking the monitoring service out of the system. Tank gauge malfunctions are considered a serious issue due to the regulatory and safety issues that may apply.
Who is affected?
An Internet-wide scan on January 10th, 2015 [3] identified approximately 5,800 ATGs with TCP port 10001 exposed to the internet and no password set. The majority of these systems belong to retail gas stations, truck stops, and convenience stores. A number of major brands and franchises were represented in the dataset. An unknown number of ATGs are exposed through modem access. The majority of the ATGs appear to be manufactured by Vedeer-Root, one of the largest vendors in this space, and were identified on IP ranges associated with consumer broadband services. The graphs below indicate the top 10 states with exposed ATGs followed by a breakdown of ATGs by ISP.
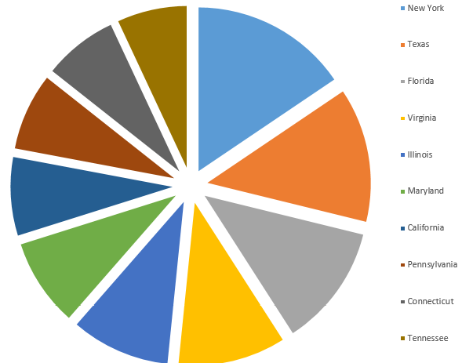
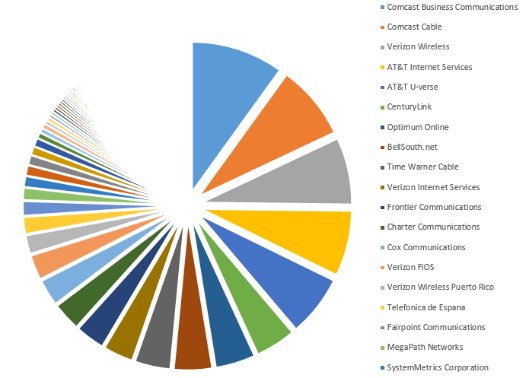
How serious is this?
ATGs are designed to detect leaks and other problems with fuel tanks. In our opinion, remote access to the control port of an ATG could provide an attacker with the ability to reconfigure alarm thresholds, reset the system, and otherwise disrupt the operation of the fuel tank. An attack may be able to prevent the use of the fuel tank entirely by changing access settings and simulating false conditions, triggering a manual shutdown. Theoretically, an attacker could shut down over 5,300 fueling stations in the United States with little effort.
How was the issue discovered?
Jack Chadowitz, founder of Kachoolie, a BostonBase Inc. spin off, reached out to Rapid7 on January 9th, 2015 [3] after reading about Rapid7's previous research into publicly exposed serial port servers. Mr. Chadowitz became aware of the ATG vulnerabilities through his work in the industry and developed a web-based portal to test the exposure as well as a secure alternative solution. Mr. Chadowitz asked Rapid7 for assistance investigating the issue at a global level. On January 10th, Rapid7 conducted an internet-wide scan for exposed ATGs with TCP port 10001 exposed to the internet. Rapid7 sent a Get In-Tank Inventory Report request (I20100) to every IPv4 address [2] that had TCP port 10001 open. The response to this request included the station name, address, number of tanks, tank levels, and fuel types.
Is this being exploited in the wild? How exploitable is it?
To the best of our knowledge this issue is not being exploited in the wild. However, it would be difficult to tell the difference between an intentional attack and a system failure. Public documentation from Vedeer-Root provides detailed instructions on how to manipulate ATGs using the serial interface, which also applies to the TCP/IP interface on port 10001. No special tools are necessary to interact with exposed ATGs.
What can be done to mitigate or remediate?
Operators should consider using a VPN gateway or other dedicated hardware interface to connect their ATGs with their monitoring service. Less-secure alternatives including applying source IP address filters or setting a password on each serial port.
Footnotes
1. The 2012 US Census counted 112,000 gas stations, however the 2015 number has been estimated by an industry expert to be closer to 150,000 (including private facilities).
2. Rapid7 used the existing Project Sonar infrastructure to conduct the ATG scan. This system skips networks where the owners have explicitly requested that their systems be excluded from future scans. At the time of the ATG scan, approximately 6.5 million addresses were excluded from the routable IPv4 address space.
3. An earlier version of this post incorrectly stated the dates as 2014, not 2015.