Patch Tuesday last week saw the release of Microsoft security bulletin MS15-034, which addresses CVE-2015-1635, a remote code execution vulnerability in Microsoft Internet Information Services (IIS) running on Windows 7 / Server 2008 R2 and later. This vulnerability can be trivially exploited as a denial of service attack by causing the infamous Blue Screen of Death (BSoD) with a simple HTTP request.
In order to provide better assessment of your assets' threat exposure to this vulnerability, we have released a safe remote check for MS15-034 in the Nexpose 5.13.3 update. This check does not require credentials and runs against IIS versions 7.5 and higher.
How do I run the MS15-034 remote check against my assets?
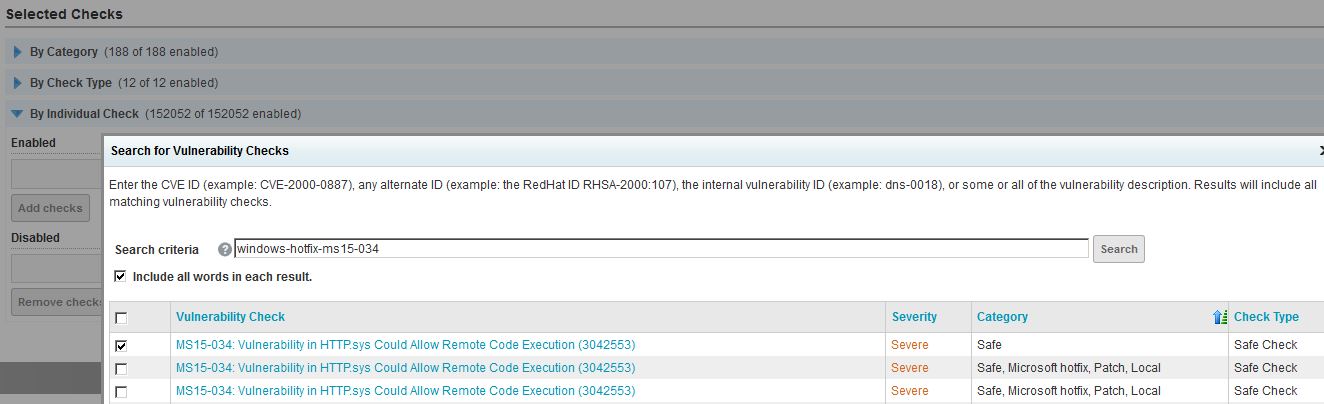
This remote check is automatically included in the default "Full Audit without Web Spider" scan template. To enable this check in a custom scan template, simply go to the Vulnerability Checks section of your scan template configuration to add individual checks. Search for the vulnerability ID "windows-hotfix-ms15-034" to bring up a list of all MS15-034 checks, sort them by "Category", and select the check that is not labeled "Local".
Will this remote check cause a BSoD on my server?
The range header value used in this check, "bytes=0-18446744073709551615", is considered by the security community to be a safe parameter for deterrmining the vulnerability status of CVE-2015-1635. Several other values are known to cause BSoDs on the target server and are not used by Nexpose.
What are some limitations of this remote check?
The remote check is configured to send a request to the root page of the web server, which is a valid resource in most common deployments. If your IIS deployment is configured to handle requests to root differently (e.g., error 404), then this check may not be able to accurately detect the vulnerability.