The number one critical security control from the Center for Internet Security recommends actively managing all hardware devices on the network:
CSC 1: Inventory of Authorized and Unauthorized Devices
Actively manage (inventory, track, and correct) all hardware devices on the network so that only authorized devices are given access, and unauthorized and unmanaged devices are found and prevented from gaining access.
http://www.cisecurity.org/critical-controls.cfm
Here a some of the reasons you should actively inventory your hardware:
- Discover new assets that have not yet patched
- Detect returning hardware such as laptops that have missed previous updates
- Identify unauthorized hardware
Whatever the scenario, you'll want to establish your surface area in order to accurately assess your risk and remediate vulnerabilities.
Before you can track and correct assets on your network, you must first establish a method to inventory all of the assets connected to your network. Employing a DHCP dynamic discovery connection in InsightVM is a great way to determine what hardware is present on your network.
InsightVM dynamic asset discovery via DHCP parses DHCP server logs and supports two collection methods for gathering DHCP log entries:
- Directory watcher – watches a specified directory for new and updated DHCP log files.
- Syslog – listens on a TCP/UDP port to receive syslog messages much like a syslog server
InsightVM dynamic asset discovery currently supports Microsoft Server 2008 and 1012 using either directory watcher or syslog, as well as, Infoblox Trinzic using syslog.
How to Create a DHCP Discovery Connection
From the Administration page, find the Discovery Options section and click the Create link next to CONNECTIONS.
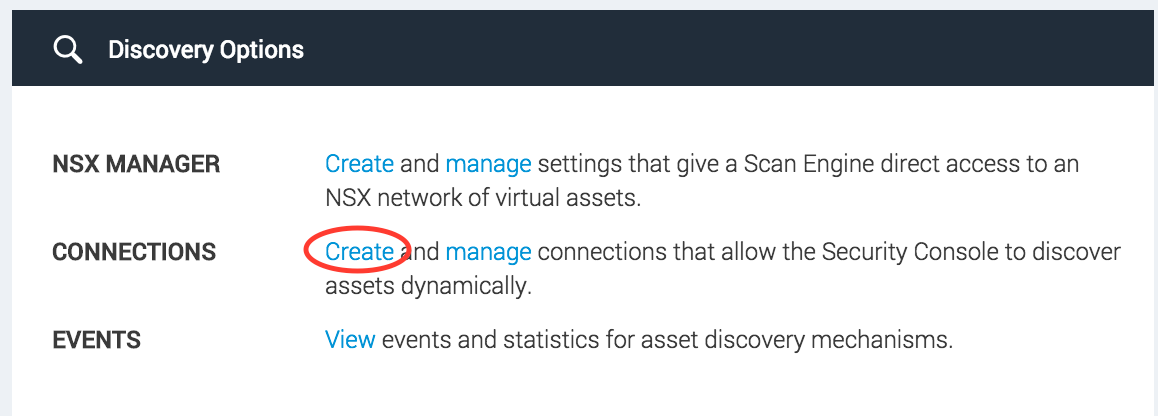
Next, fill in all three tabs of the form…
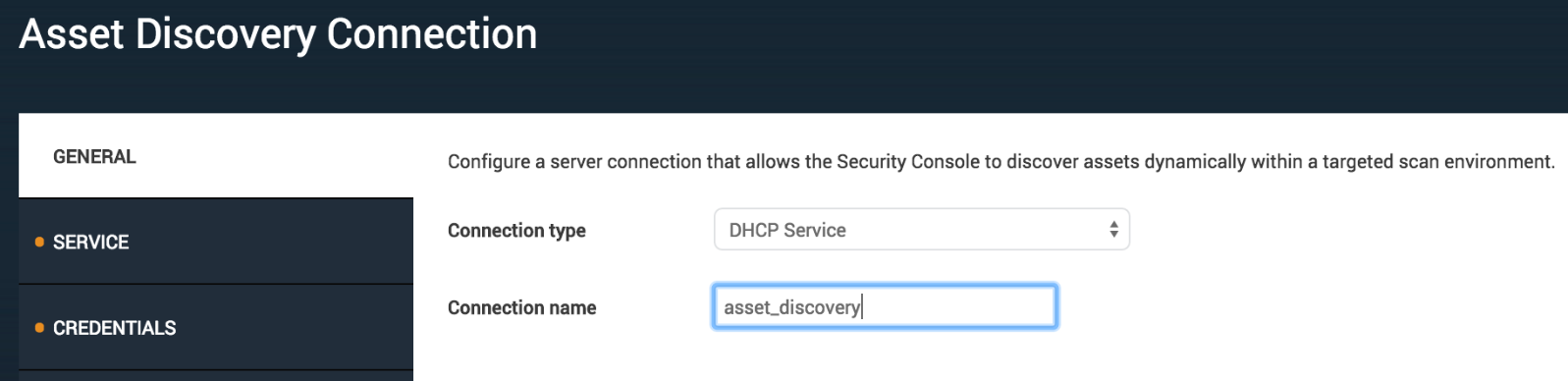
From the General tab, select DHCP Service and provide the name of your discovery connection.
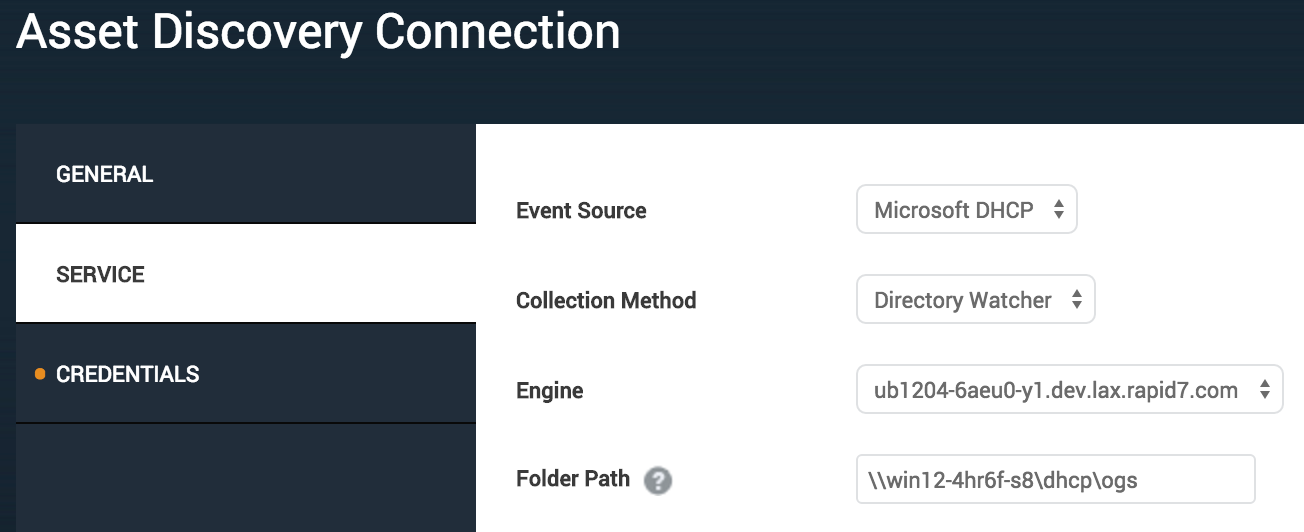
From the Service tab, select the event source, collection method, and engine. The source and collection method will determine what additional fields are required. In the example, using the directory watcher collection method for Windows Server mandates providing the fully qualified path to the directory where DHCP logs reside.
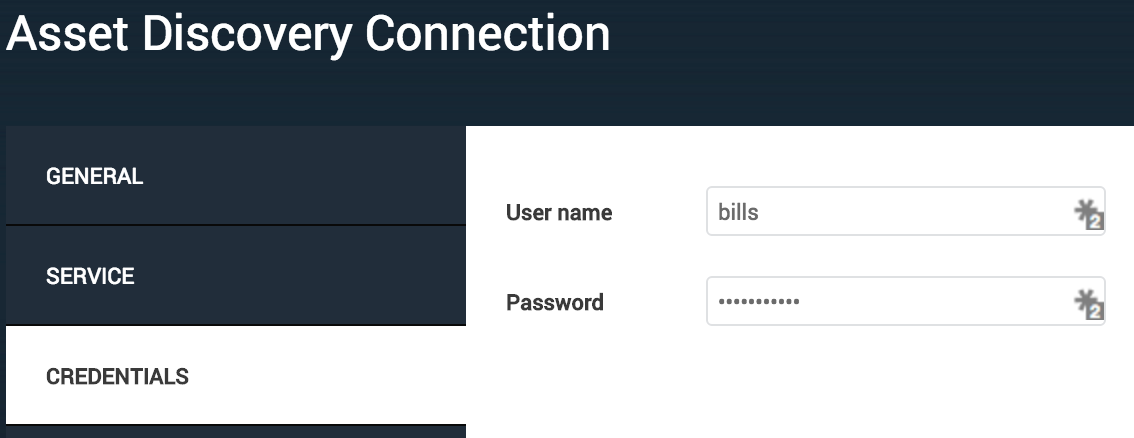
From the Credentials tab, provide the username and password for you to access the directory.
As the DHCP server logs events, they will be parsed and imported as assets discovered by connection. Previously assessed assets that appear in DHCP logs will continue to show only as assessed. Discovered assets have not been assessed and present unknown risk to your network.
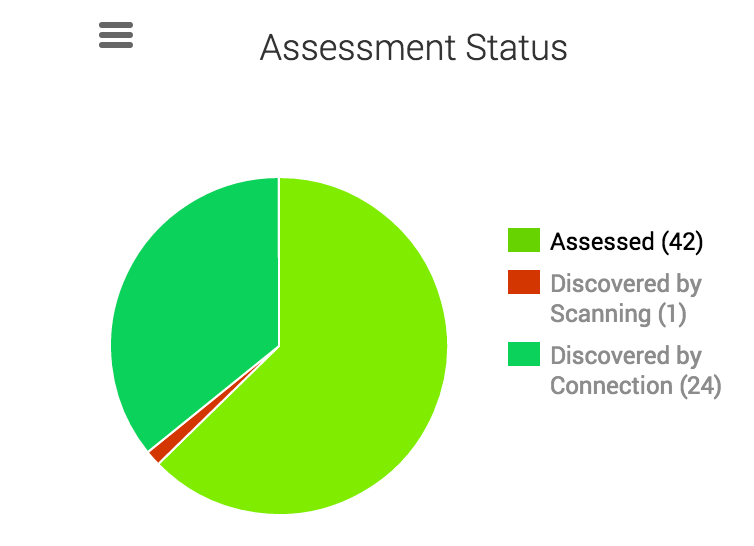
The Assessment Status chart on the Assets page gives you a clear indication of your un-assessed surface area. Additionally, the Discovered by Connection table enumerates the discovered assets that have not yet been assessed.