We just launched InsightIDR, the only fully integrated detection and investigation solution that lets you identify a compromise as it occurs and complete an investigation before things get out of control. InsightIDR does three things well: detect attacks with high fidelity, accelerate investigations, and end the drudgery of security data management. I'd like to take a minute to share how we got here and why we're so excited to show you InsightIDR.
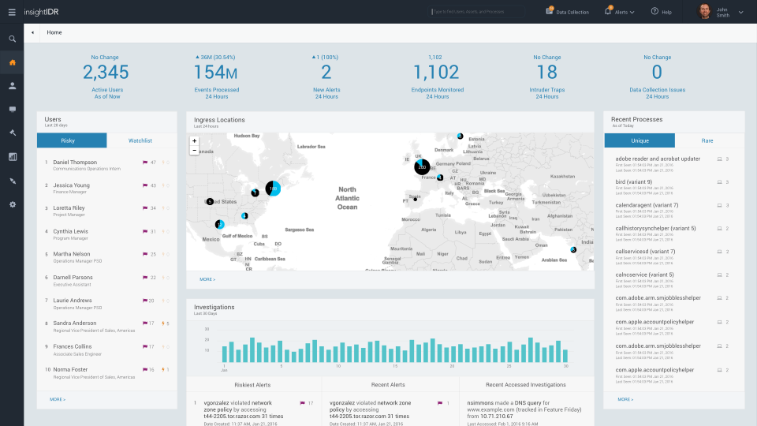
Cutting through the Noise to Detect Attacks
Detecting the top attack vectors behind breaches – compromised credentials, malware, and phishing is still a challenge. 90% of organizations are worried about compromised credentials, but only 40% can detect attacks using stolen passwords today[1]. InsightIDR can detect all three, with a special focus on catching intruders earlier in the attack chain, before they've stolen data.
From the Metasploit Project, Penetration Testing, and Incident Response services, we've leveraged our Red & Blue team experience to know how attackers operate, and the traces they leave behind. With attacks no longer dependent on malware and the perimeter, we found that the most effective approach was with User Behavior Analytics (UBA), which we released with UserInsight (now renamed InsightUBA). Both solutions integrate with your existing network and security stack, but not all signs of the attacker are found in logs. We therefore created Intruder Traps, which specifically detect attacker behavior such as network scans and password guessing attempts. InsightIDR combines UBA, Intruder Traps, and Machine Learning – we tailor the approach to detect the exact attack method. But we didn't stop there.
Investigate Incidents Faster (by an order of magnitude!)
This is a huge industry challenge. 62% of organizations receive more alerts daily than they can feasibly investigate, and that's from their SIEM alone[2]. On top of that, investigation combines the intricacy of piecing together a story with limited context with the annoyance of searching through disparate data sources and retracing users across assets, IPs, and assets. Simply validating a threat can take hours, and security analysts need to first know “where to look” before running search queries across the ecosystem.
Today's investigations take too long. With InsightIDR, every action on the network is correlated to the users and assets behind them, meaning that every alert and search across your data is displayed through a user lens. Every generated alert automatically comes with the surrounding Notable Behavior, valuable context that speeds up the validation and scoping of an incident.
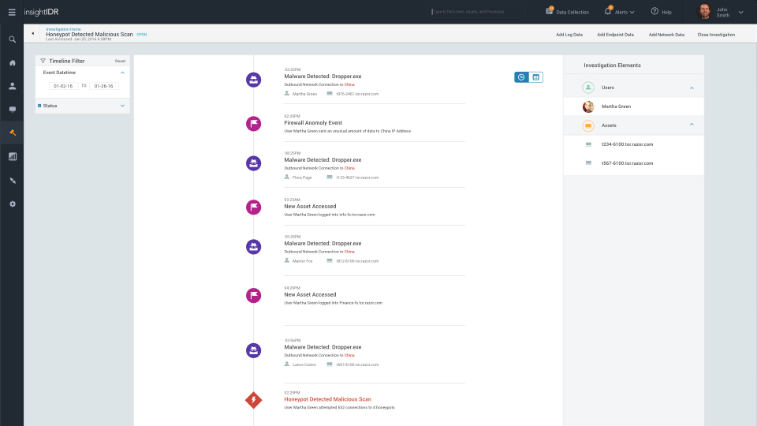
For example, an unmarked van parked near a bank isn't worth firing an alert about, but in case of break-in, is notable and valuable in context. If you need to dig deeper, you can search across all of your log data, including endpoints outside of the network. This deep endpoint interrogation means current processes, services, registry and more, helping find active attacks that evade traditional monitoring systems. And finally…
End the Drudgery of Security Data Management
Security stacks are sophisticated, often with several tools each generating alerts without a user or network context. For example, cloud solutions – most orgs (79%) allow approved cloud services, but only 33% have security visibility into those services[3]. In a single solution, we cover the entire ecosystem, from continuous endpoint detection to direct API integrations with leading cloud services, such as Office 365, Salesforce, and Box.
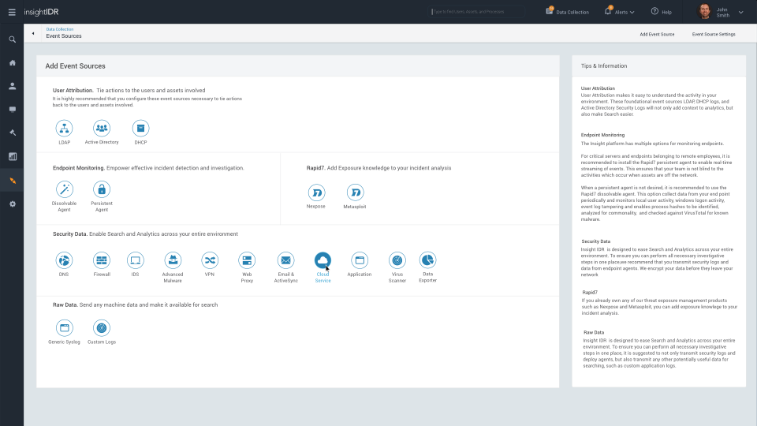
Due to our unique cloud approach, you no longer need to manage the hardware, maintenance, or data collection across your network. This leads to a faster time to value without requiring your staff to “Tune” and “Run” the deployment. Plus, you can even check the compliance box with custom dashboards to meet requirements.