Disclosure Summary
ManageEngine OpUtils is an enterprise switch port and IP address management system. Rapid7's Deral Heiland discovered a persistent cross-site scripting (XSS) vulnerability, as well as a number of insecure direct object references. The vendor and CERT have been notified of these issues. The version tested was OpUtils 8.0, which was the most recent version at the time of initial disclosure. As of today, the current version offered by ManageEngine is OpUtils 12.0.
R7-2016-02.1: Multiple Persistent XSS Vulnerabilities
While examining ManageEngine OpUtils v8.0, an enterprise switch port and IP address management software, it was discovered to be vulnerable to a persistent cross-site scripting (XSS) vulnerability. This vulnerability allows a malicious actor to inject persistent XSS containing JavaScript and HTML code into various fields within the products Application Program Interface (API) and the old style User Interface (UI) . When this data is viewed within the web console the code will execute within the context of the authenticated user. This can allow a malicious actor to conduct attacks which can be used to modify the systems configuration, compromise data, take control of the product or launch attacks against the authenticated user's hosts system.
The first series of persistent XSS attacks were delivered to the OpUtils product via the network discovery process. When a network device is configured with SNMP, the SNMP OID object sysDescr 1.3.6.1.2.1.1.1 can contain HTML or JavaScript code. The code will be delivered to the product for persistent display and execution without proper input sanitization. This is a similar vulnerability to those disclosed as Multiple Disclosures for Multiple Network Manage Systems.
The following example shows the results of discovering a network device where the SNMP sysDescr has been set to <SCRIPT>alert(“XSS-sysDescr”)<SCRIPT> . In this example, when device is viewed within OpUtils API UI web console, the JavaScript executes rendering an alert box within the authenticated users; web browser.
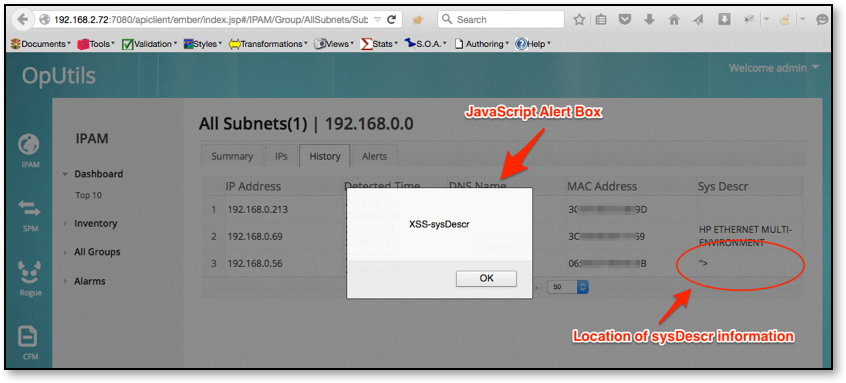
After switching version 8.0 from the API UI to the old UI schema several other XSS injection points where identified. This includes persistent XSS attacks, which was also delivered to the OpUtils old UI interface via the network discovery process. If the network device is configured with SNMP and the following SNMP OID objects contain HTML or JavaScript code, the code will be delivered to the product for persistent display and execution.
sysDescr 1.3.6.1.2.1.1.1
sysLocation 1.3.6.1.2.1.1.5.0
sysName 1.3.6.1.2.1.1.6.0
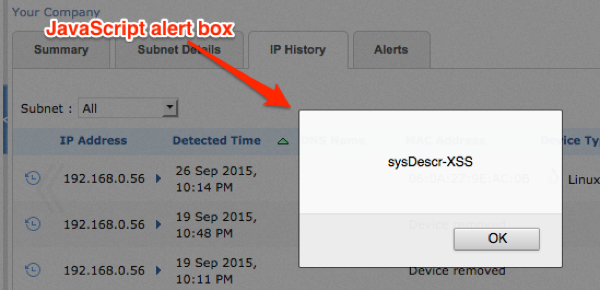
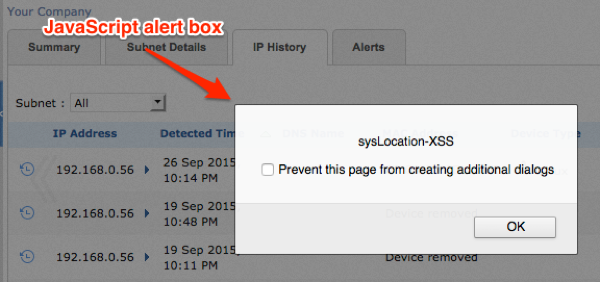
sysDescr and sysLocation triggered when viewed within IP History as shown in Figure 2 and Figure 3.
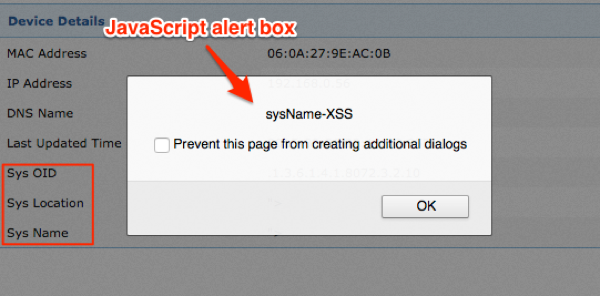
In addition, sysDescr, sysLocation, and sysName triggered when viewed within device history as shown in Figure 4.
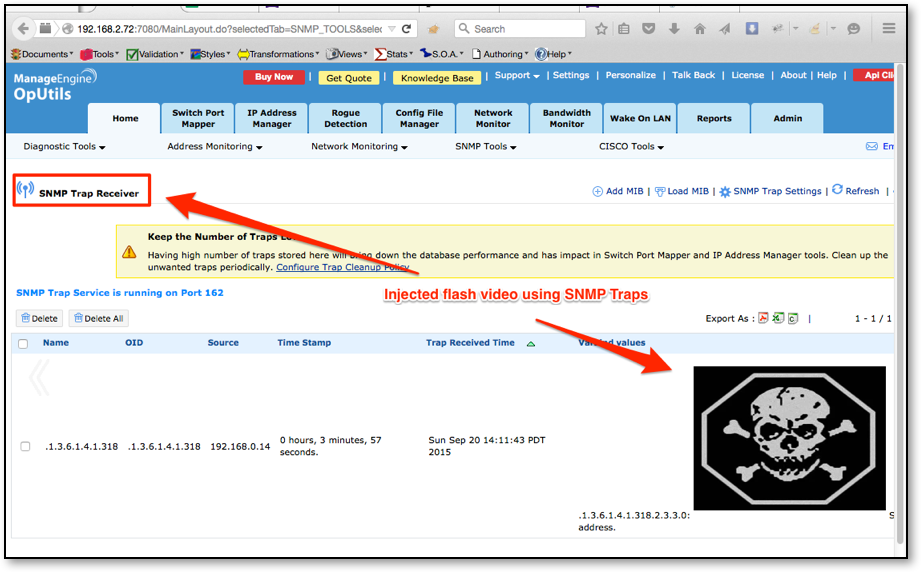
The second method of injection involved SNMP trap messages. By spoofing an SNMP trap message and altering the data within that trap message, a malicious actor can inject HTML and JavaScript code into the product. When the trap information is viewed within the SNMP Trap Receiver the code will execute within the context of the authenticated user. Figure 5 shows an example attack where a trap message was used with the following HTML code <embed src=//ld1.us/4.swf> to embed flash into the Trap Receiver section of the UI.
R7-2016-02.2: Multiple Insecure Direct Object References
During testing, it was discovered that URLs ending in .cc are accessible without proper authentication. This allowed for retrieval of a portion of the web page. The following URLs are able to be accessed without authentication:
http://IP-Address:7080/SystemExplorer.cc
http://IP-Address:7080/UserView.cc
http://IP-Address:7080/AuditView.cc
http://IP-Address::7080/AuditViewRogue.cc
http://IP-Address:7080/IPAMReport.cc
http://IP-Address:7080/ipAddressManager.cc
http://IP-Address:7080/ipAddressManagerInputPage.cc
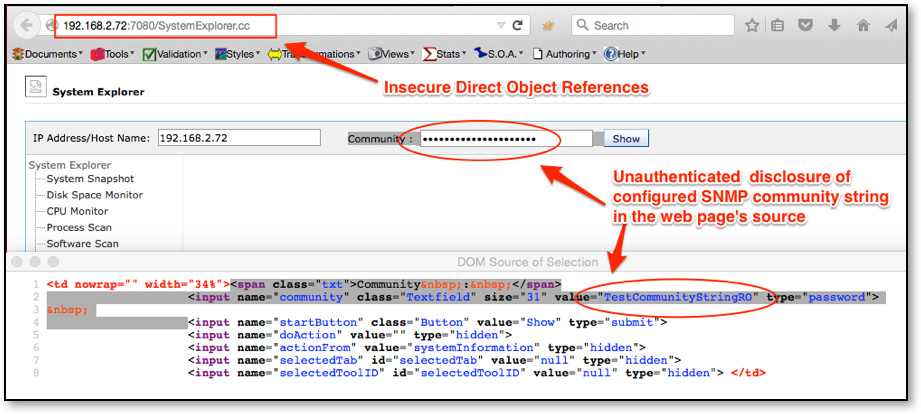
As a result of this direct access without authentication, an attacker is able to view the HTML of the web page SystemExplorer.cc. Here, it was discovered that the product's configured SNMP community string is transmitted in clear text as shown in Figure 6.
Disclosure Timeline
Thu, Jan 14, 2016: Issues discovered by Deral Heiland of Rapid7, Inc.
Fri, Jan 15, 2016: Initial contact to vendor
Mon, Feb 15, 2016: Details disclosed to CERT, tracked as VU#400736
Wed, Mar 9, 2016: Clarification requested by the vendor, via CERT
Thu, Mar 17, 2016: Public disclosure of R7-2016-02
