When building out next year's security initiatives, how do you prioritize and choose projects? At Rapid7, we recommend modeling your security program to the Attack Chain, a graphical representation of the steps required to breach a company.
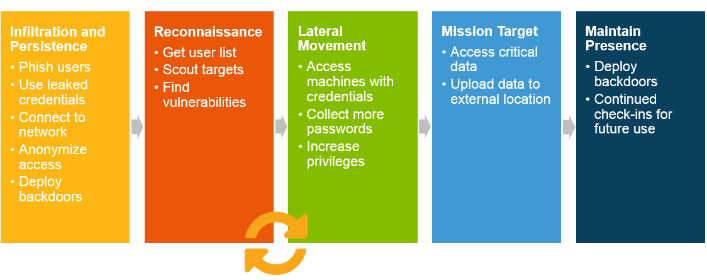
For every successful breach, whether it be from a credential-based attack, malware, or the exploitation of a vulnerability, attackers need to perform at least one or multiple steps in the chain. If you can detect, investigate, and remediate the attack earlier in the chain, this stops data theft, whether it be Credit Card information, Protected Health Information, or your proprietary financials and schematics.
Our four tips when expanding your security program:
1. Prioritize early attack chain detection.
While it's important to identify unauthorized access of valuable assets, this also means that if the activity is malicious, the intruder is already at Mission Target. By identifying earlier traces of the attack, such as Infiltration, Reconnaissance, and Lateral Movement, your security team can respond before data is stolen.
2: Focus on the highest-probability attacks first.
This year's Verizon's Data Breach Investigations Report (DBIR) continues to tell the same story - compromised credentials, malware, and phishing are the top 3 attack vectors behind breaches.
Many organizations have detection in depth for malware, but cannot detect compromised credentials or phishing. Our knowledge of the attacker derived from the Metasploit project and Rapid7 Global Services confirms this finding – our penetration testers have a near 100% success rate by leveraging account takeover techniques and impersonating your users to stay under the radar.
3. Identify gaps in your security program.
Evaluate your security program to ensure the detection of compromised credentials, phishing, and malware during the first three steps of the chain. By identifying these gaps in coverage, this will provide direction for future initiatives. This is a huge improvement over a scattershot approach or taking action in response to pain or executive visibility.
4. Avoid duplications per step to reduce overspending.
There are so many security monitoring solutions available today. When bringing in a new tool, it's been a challenge to quantify its value, especially if it has overlap with other solutions. If the tool only monitors a specific part of the network, this can cause alert-fatigue as each siloed solution blasts alerts. For this reason, choose solutions that not only have the least overlap, but also fit into your available security bandwidth. For example, SIEM deployments take significant setup, professional services, training, and tuning. The time investment combined with the required technical expertise to create and manage rules can greatly expand the time investment needed to see value from the solution.
At Rapid7, we've combined our Red & Blue team expertise with this Attack Chain methodology into our User Behavior Analytics solution, InsightIDR. By correlating all of the activity across your network and security stack to the people behind them, you can detect stealthy attacks, investigate incidents faster with user context, and expose risky internal behavior from endpoint to cloud. InsightIDR's high accuracy and cloud approach empowers you to watch your entire ecosystem, even if you are fighting the adversary with a small team.