Starting this week, we have added a new vulnerability category: Rapid7 Critical.
When we examine a typical vulnerability, each vulnerability comes with various pieces of information such as CVE id, CVSS score, and others. These pieces of information can be very handy especially when you set up Automated Actions in Nexpose. Here is an example:
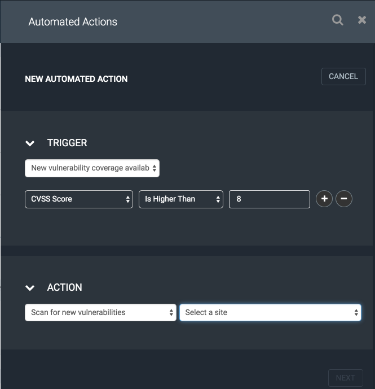
As you can see the example on the right, this trigger will initiate a scan action if there is a new coverage available that meets the criteria of CVSS score is 8 or above. This Automated Action is ideal for assessing for high-risk vulnerabilities right away. With Rapid7 Critical vulnerability category, we are giving you another indicator for high-risk vulnerabilities.
You might be thinking that the above Automated Action is good enough to catch high-risk vulnerabilities given the criteria is to take action as soon as a vulnerability with CVSS score 8 and above is released. Yes, you are right! For most circumstances, the above Automated Action would be good enough. However, the Rapid7 Critical vulnerability category ensures that you do not miss any high-risk vulnerabilities at all especially when the vulnerability is brand new.
When a vulnerability is new, it may not always have a CVSS score assigned it to it yet. When that happens, the above Automated Action may not be fully capable of assessing the new high-risk vulnerability simply because there is no CVSS score to check. With Rapid7 Critical vulnerability category, we are making sure that even if there no CVSS score yet for the vulnerability, you can still assess it with Adaptive Security right away.
Let me show you how you can use the Rapid7 Critical vulnerability category in Automated Actions.
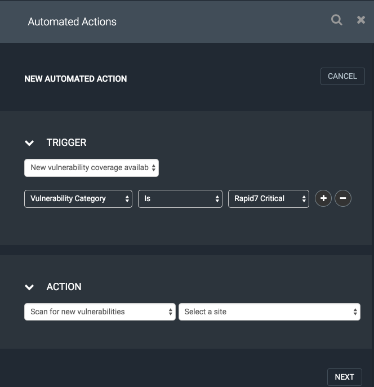
As you can see the example on the right, you would just create a new Automated Action, and select only one filter*; Vulnerability Category is Rapid7 Critical. This Automated Action will ensure that Nexpose initiates a scan for the high-risk vulnerability even though the vulnerability does not have a CVSS score assigned to it yet.
If you already have an Automated Action similar to the first example in this blog post which uses CVSS score as a filter, you should not delete it. The second Automated Action that you created will simply catch those critical vulnerabilities in case there is no CVSS score available yet.
As always, feel free to drop us any comments below, or reach out to Rapid7 Support if you have any questions.
* We do not recommend using any other filter along with Rapid7 Critical vulnerability category filter to make sure that the Automated Action initiates a scan for all critical vulnerabilities that are marked by Rapid7.
Eray Yilmaz
Sr. Product Manager