If you're only looking through your log files, reliably detecting early signs of attacker reconnaissance can be a nightmare. Why is this important? If you can detect and react to an intruder early in the attack chain, it's possible to kick the intruder out before he or she accesses your critical assets. This is not only good for you (no monetary data is stolen), but it's also critical because this is the only time in the chain that the intruder is at a disadvantage.
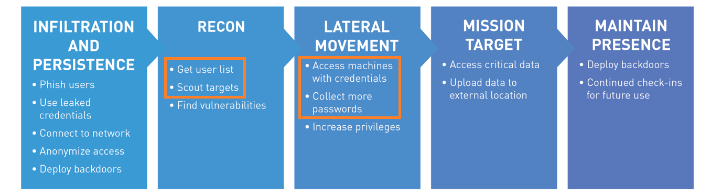
Once an attacker has an initial foothold on your network (above, Infiltration and Persistence), their work is not complete. Their next steps are reconnaissance: learning more about the environment and where they need to pivot to next. This behavior, such as network scans, password guessing attempts, and pass-the-hash is very different than the actions your users take every day and leaves tangible, identifiable traces.
InsightIDR, our full incident detection and investigation solution, comes standard with Honey Pot and Honey User intruder traps. Most of our customers find these features easy-to-use and helpful: “[Honey Pots]…are a great idea for detecting illegitimate network scans,” says Nick Hidalgo, Director of IT at Redner's Markets. To combat pass-the-hash and memory scraping techniques, we've now added a new trap: Honey Credentials. In the same way that banks place exploding dye packs in money bags, marking the money to identify it later, Honey Credentials show a clear trail of an intruder moving laterally across your network. Keep reading to learn how the intruder trap suite works in InsightIDR.
Plant Decoy Credentials Around Your Network
On each of our endpoints, password hashes are stored locally on the machine. This allows us to login to work without being connected to the Internet. However, since they are stored on the machine, attackers can use tools, such as Mimikatz, to pull either the password hashes or even the cleartext passwords from the target. These hashes can be reused to attempt authentication elsewhere on the network, and is a favorite technique of penetration testers and real attackers alike.
Honey Credentials work by injecting a set of fake credentials onto your endpoints. If an attacker steals this fake credential and attempts authentication, you'll receive an automatic alert. Two common scenarios: (1) a user attempted to log in with a Honey Credential on that asset, or (2) a user is attempting to use Honey Credentials to pivot to another endpoint. As the fake credentials don't grant access to any of your systems, they are therefore very safe to use.
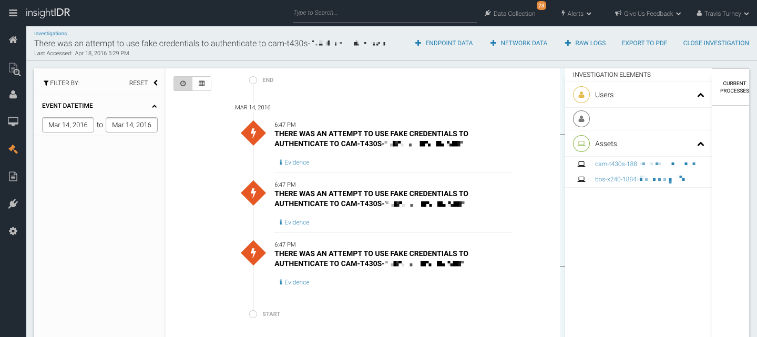
Expanding our Intruder Trap Library
Our vision with InsightIDR is to help you detect and investigate attackers from endpoint to cloud. This mindset extends to the way we ingest data. Instead of looking at your readily available log files, from our red team and blue team experience, we know the steps attackers must follow and the traces left behind.
One example is a low-and-slow password guessing attack. Instead of trying hundreds of passwords on one asset, which can be rather noisy, an attacker may try two or three passwords across every asset on the network. Since we don't want alerts everytime there are three authentication failures (guilty of that just this morning), a low-and-slow attack largely goes undetected. With another intruder trap in InsightIDR, Honey Users, you can identify this technique earlier, accelerating your compromise to containment. For a general overview of InsightIDR, check out our on-demand 20 minute demo.
How Do I Deploy Honey Credentials?
Honey Credentials are available now in InsightIDR and InsightUBA. Honey Credentials are automatically deployed to endpoints using the Continuous Endpoint Agent (Persistent Agent). To set up the agent, you can use Microsoft's System Center Configuration Manager or deploy using a PowerShell script. The agent begins immediately after being installed.
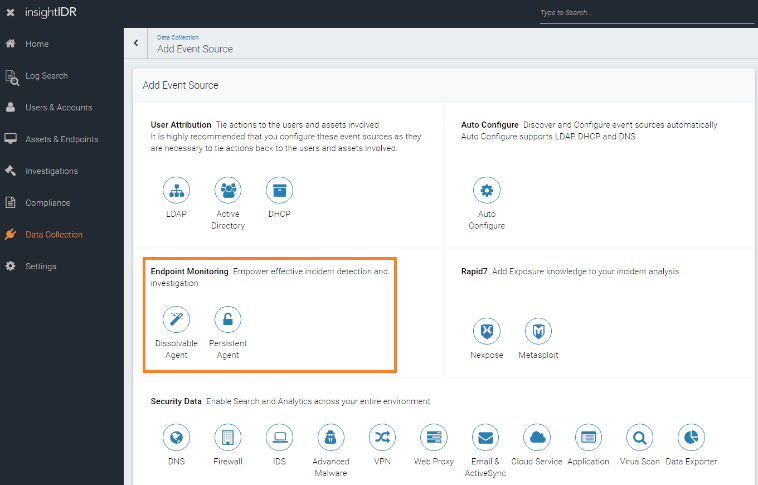
If InsightIDR detects use of the Honey Credential, you'll be automatically alerted. If you need any further assistance, don't hesitate to reach out to your Customer Success Manager.
