A few years ago, ransomware was primarily a consumer problem. However, cybercriminals behind recent ransomware attacks have now shifted their focus to businesses. One example of this is ransomware families such as Ryuk, which is commonly used to target enterprise environments. Users in these enterprises are typically targeted with phishing emails containing Microsoft Office document files with embedded malicious macro code. In another example, RobbinHood ransomware uses a vulnerable Windows kernel driver that is included along with the malware. This vulnerability is then used to install the malware on the host system.
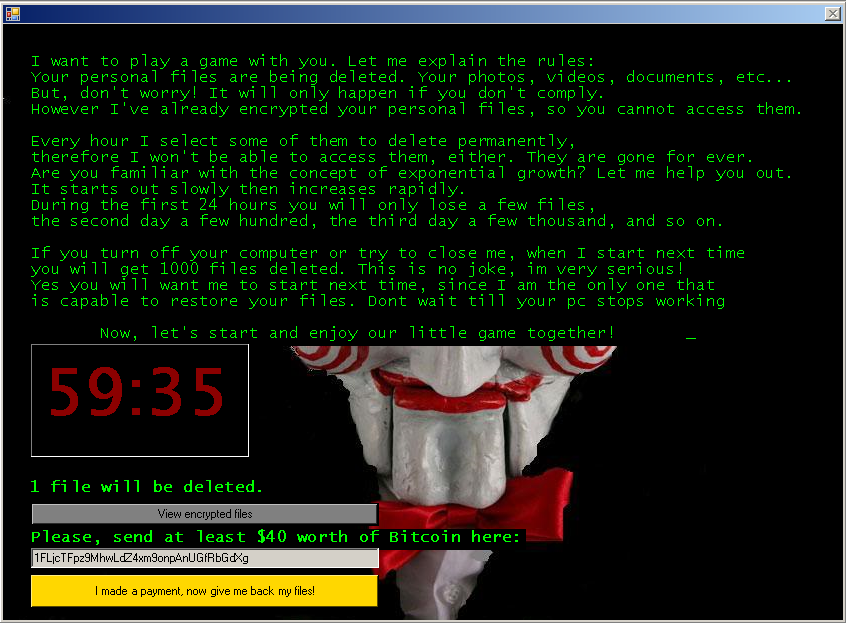
When it comes to preventing ransomware attacks, the No. 1 tip is to back up all your data and make sure you do a test restore. However, even with the latest-generation firewalls and antivirus on all desktops, ransomware can still get into a network. The most common attacks use email phishing with dodgy attachments, but we have also seen attacks using remote desktop services and infected data storage devices.
How to detect ransomware on your network
The first variants of ransomware used a small number of very specific file extensions, like .crypt. However, each new variant seems to use different extensions, and some even keep the file name intact. Because of this, you need to watch out for multiple symptoms of an attack, such as the five following signs:
1. Watch out for known file extensions
Even though the list of known ransomware file extensions is growing rapidly, it is still a useful method for detecting suspicious activity. Before you do anything, you need to get file activity monitoring in place so that you have both a real-time and historical record of all file and folder activity on your network file shares.
2. Watch out for an increase in file renames
File renames are not a common action when it comes to activity on network file shares. Over the course of a normal day, you may end up with just a handful of renames, even if you have hundreds of users on your network. When ransomware strikes, it will result in a massive increase in file renames as your data gets encrypted.
You can use this behavior to trigger an alert. However, if the number of renames goes above a certain threshold, you have a potential ransomware issue. Our recommendation is to base your alert on anything above four renames per second.
3. Create a sacrificial network share
Ransomware typically looks for local files first, then moves onto network shares. Most of the variants I have looked at go through the network shares in alphabetical order: G: drive, then H: drive, etc.
A sacrificial network share can act as an early warning system and delay the ransomware from getting to your critical data. Use an early drive letter likelike E:, something that comes before your proper drive mappings. The network share should be set up on old, slow disks and contain thousands of small, random files.
When doing small, random files, there’s no easy way to get the list of files in the right order to avoid a lot of seeking around the disk. Depending on how it is implemented, the cipher might need to be re-initialized for each file, which slows down the encryption process.
The slower the disk, the better. You could go to the extreme and put it behind a router and limit data throughput to this network share. It may add a slight delay to the logon process, but this honeypot may give you enough time to shut down client machines if they get infected with ransomware.
You could also set up an alert that triggers if a specific file was accessed somewhere within the network share. This would be a sure sign that something was going through your file shares. You just need to educate your users to stay away from this network share.
4. Update your IDS systems with exploit kit detection rules
Many IDS, IPS, and firewall systems come with exploit detection features. Exploit kits are used as a way to get ransomware onto a client through malspam or via compromised websites.
The two most common exploit kits (EK) associated with ransomware are the Neutrino EK and the Angler EK. Check if your network security monitoring systems are up-to-date and see if they have the capability to detect exploit kits.
5. Use client based anti-ransomware agents
In the past, companies like Malwarebytes have released anti-ransomware software applications. These are designed to run in the background and block attempts by ransomware to encrypt data. They also monitor the Windows registry for text strings known to be associated with ransomware.
Researchers are also looking at ways to “crash” computer systems when droppers are detected. Droppers are small applications that first infect target machines in preparation for downloading the main malware payloads. This will likely mean that the system is sent to IT where the attack should be discovered.
You should also inform your network users to avoid installing agents themselves. There is too much of a risk that they will install the wrong agent or they end up installing more malware on their systems.
Getting your data decrypted
Recently, the infosec industry rallied around a common goal to combat ransomware under the No More Ransom initiative. While the public face of this initiative is the portal nomoreransom.org, where almost 100 decryption tools are provided freely to anyone who may have the misfortune of being a victim of ransomware, the initiative is a true collective of organizations and law enforcement agencies combating ransomware and those behind such cowardly attacks.
Find out what variant of ransomware you are dealing with by reviewing any splash screens or by checking for information within ransom note text files. You can then search for a decryption tool on the nomoreransom.org website.
Managed Threat Complete
Leverage a practitioner-first experience that puts an elite SOC on your team.
LEARN MOREWill ransomware go away?
The simple answer to this is no. All indicators suggest that ransomware will remain a major and rapidly growing threat, fueled by anonymizing networks and payment methods. Expect to see an increase in ransomware variants that target websites instead of file stores. Linux.Encoder.1 is an example of this type of threat. When a website is attacked, the ransomware will hold the site’s files, pages, and images for ransom.
There are two key lessons here:
- Ensure you are backing up your website
- Keep the website operating system and CMS fully patched
Ransomware is also a growing problem for users of mobile devices. Lock-screen types and file-encrypting variants of ransomware will stop you from accessing anything on your mobile device, and file-encrypting variants will encrypt data stored on the device. You can decrease your chances of an attack by avoiding unofficial app stores and by keeping your mobile device and apps updated.
I’ll finish by repeating the advice: Ensure you backup all of your personal and work data, educate users on the risks, and disconnect problematic users from sensitive data.
