Creating a Positive Feedback Loop
Recently I've focused on some specific use cases for vulnerability analytics within a security operations program. Today, we're taking a step back to discuss tying vulnerability management back in to asset management to create a positive feedback loop. This progressive, strategic method can mitigate issues and oversights caused by purely tactical, find-fix vulnerability cycles. And it can be done using vulnerability scan data, creating additional value from your ongoing security operations.
Consider the top four CIS Critical Security Controls from the lens of asset and vulnerability management:
- CSC 1 - Inventory of Authorized and Unauthorized Devices
- CSC 2 - Inventory of Authorized and Unauthorized Software
- CSC 3 - Secure configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
- CSC 4 - Continuous Vulnerability Assessment and Remediation
The top three controls can be roughly grouped together as "Do Asset Management." Number four can be roughly described as "Do Vulnerability Management". Often times organizations address these as completely separate problems, when in reality they are part of the same lifecycle:
- Many vulnerability management findings stem from oversights or problems with asset management programs.
- Many vulnerability scan details can be used to help audit and improve asset management programs.
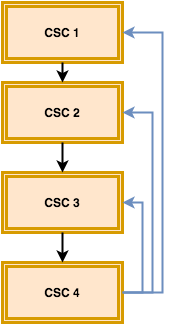
Consider the down-cycle flow here to be point one, and the up-cycle flow to be point two:
The down-cycle is a given, based on relationship between asset management and vulnerability management. The up-cycle requires proactive lifecycle management to properly implement. The examples below describe creating asset review processes as a practical way to leverage vulnerability management data for improved asset management.
Asset & Software Inventory Review
Vulnerability management scanning generally begins with preliminary network scanning using tools like nmap. Before reviewing vulnerability check results, the basic network scan data can provide significant value for a checks-and-balances review. Consider the following short vignettes, boiled down from actual conversations in the field.
Admin: "We just finally replaced the last of our Windows XP machines six months ago, it took forever! We finally had to put a task-force team together to get it done."
< Run a discovery scan, review results >
Consultant: "It looks like you still have 12 Windows XP machines in your environment."
< Cue: "We're putting the band back together" >
Consultant: "You would be surprised how many times I find non-secure FTP, or even TELNET running in an environment."
Admin: "We have a strictly locked down network; we know everything that's running out there and we definitely don't have FTP or TELNET."
Consultant: "Well, it can't hurt to do a search. It might just come back empty."
< Run a quick search in vulnerability scan data >
Consultant: "Yep, looks like there are a handful of each here."
Admin: "Oh ****, that one's in our DMZ."
< Cue: "Quick, to the Batcave!" >
The broad theme here is the vulnerability scan data is good for more than just vulnerability analysis; these vignettes do not represent specific vulnerabilities, but misdeployed or misconfigured assets within the environment. By creating an inventory review cycle, you can realize additional value from the scan data you are already collecting.
Vulnerability Remediation Review
While it is important to validate asset management through checks and balances review, it is also important to continue proactively validating vulnerability remediations as a check-and-balance for the vulnerability management program. Consider the following scenario, again pulled from field conversation.
Admin: "We had a massive fire drill a few months ago for [ insert topical buzz-heavy vulnerability ]. It was a lot of long nights, but it's good to have it done."
Consultant: "Well, we should set up some searches to make sure that vulnerability doesn't show back up in the environment again."
< Run a quick search for a specific vulnerability title or CVE Identifier >
Consultant: "Yeah, a few of these assets definitely have that same vulnerability. They must have fallen through the cracks, or someone re-installed the older software version after your cleanup effort."
< Cue: Fire Alarm >
That last item specifically describes a vulnerability regression, which I've written about before.
The Big Picture
The above scenarios outline a few basic risks associated with a tactical, find-fix vulnerability management approach. With a purely tactical approach:
- There may be unmanaged, untracked, and unnoticed assets on the network.
- There may be undesirable, unsecure, and unnoticed network services running on some assets.
- High criticality vulnerabilities may be reintroduced to the environment and remain unnoticed
By building a more strategic vulnerability management program with more thorough, iterative review cycles you can leverage your existing scan data to more effectively lock down your environment.
The need for strategic vulnerability management is not only linked to asset management validation; it is also linked to the penetration testing (CSC 20) response and remediation cycle. For more discussion, see my colleague Joe Tegg's talk from DerbyCon: "We're a Shooting Gallery, Now What?"
Looking to evaluate a new vulnerability management solution? Download a free trial of our vulnerability scanner here.
