So there's this Thing...

We need to talk about Things, you and I. Specifically those connected Things. This isn't a weird breakup discussion regarding a relationship you didn't know we had (I hear that's called stalking actually, and is an altogether different type of problem). There may be Things on your network that are harbouring a security issue, and that's not a good place to be either. We can help you track them down (which does bear a slight resemblance to stalking, granted, but we're security people and they're just Things so it's allowed).
Mirai - definitely not a Vision of Love
A recent DNS attack sent parts of the Internet into temporary meltdown – not just because our ability to share cat videos and food pictures was impeded. It became apparent that there's a new kid in town – the Mirai botnet – which takes advantage of weak security in IoT devices. Default credentials are not the internet's friend.
Now, there are plenty of good articles already available for you to read about the technicalities of the Mirai botnet, including this blog post from the highly distinguished Mr Tod Beardsley – so I'm not going to rewrite an already well authored wordy wheel, but like I said earlier we do have something cool for you to find out if you have Things on your own network that could pose a risk.
IoTSeeker – it does exactly what it says on the package!
So without further ado, I'd like to introduce you to IoTSeeker – a tool created by the incredibly smart folks on the Metasploit engineering team. IoTSeeker allows you to hunt down IoT devices which are languishing in your eco-system poorly configured with the same creds that they were born with. It's nice and simple to use, and the scan output (example below) provides you with a list of Things and an indicator as to whether they need re-configuring to be in a more secure state.
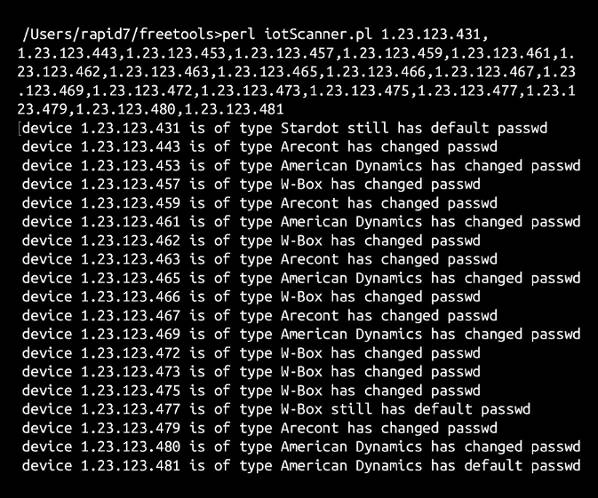
To run this tool you'll need to be on a Mac OS or a Linux OS, as IoTSeeker uses the perl module AnyEvent for high parallelism – which essentially means you can quickly scan A LOT of IPs. It's free, because we're nice like that, and we plan to keep updating it to include new Things that could be a problem. The steps on how to use IoTSeeker are available when you download the tool – and unless you have the attention span of an ADHD goldfish in a barrel full of squirrels, you'll be up and scanning in a minute or so, it really is that simple.
A very important note: this tool is provided for you to only scan assets for which you have administrative responsibility.
Download the IoTSeeker here.
Feedback welcomed, and happy Thing Seeking!
![[Free Tool] IoTSeeker: Find IoT Devices, Check for Default Passwords](/_next/image/?url=https%3A%2F%2Fwww.rapid7.com%2Fcdn%2Fassets%2Fblt303a9cc70f279667%2F683ddc713e68ee275a889818%2Fpost-img-58519.jpg&w=3840&q=75)