Stored server cross-site scripting (XSS) vulnerabilities in the web application component of OpenNMS via the Simple Network Management Protocol (SNMP). Authentication is not required to exploit.
Credit
This issue was discovered by independent researcher Matthew Kienow, and reported by Rapid7.
Products Affected
The following versions were tested and successfully exploited:
- OpenNMS version 18.0.0
- OpenNMS version 18.0.1
OpenNMS version 18.0.2-1, released September 20, 2016, corrects the issues.
Description
Two cross-site scripting (XSS) vulnerabilities were identified in the web application component of OpenNMS via the Simple Network Management Protocol (SNMP).
These vulnerabilities can allow an unauthenticated adversary to inject malicious content into the OpenNMS user's browser session. This could cause arbitrary code execution in an authenticated user's browser session and may be leveraged to conduct further attacks. The code has access to the authenticated user's cookies and would be capable of performing privileged operations in the web application as the authenticated user, allowing for a variety of attacks.
R7-2016-24.1, XSS via SNMP Trap Alerts
First, a stored (AKA Persistent or Type I) server XSS vulnerability exists due to insufficient filtering of SNMP trap supplied data before the affected software stores and displays the data. The stored XSS payload is delivered to the affected software via an object in a malicious SNMP trap. Once the trap is processed it is stored as an event. OpenNMS's Trapd service processes SNMP trap data and accepts traps with any SNMP v1 or v2c community string. The affected software is capable of accepting traps from hosts registered or unknown to the system. Traps containing XSS payloads from hosts unknown to the system will execute when the user navigates to the events list page (http://host:8980/opennms/event/list).
R7-2016-24.2, XSS via SNMP Agent Data
Second, a stored server XSS vulnerability exists due to insufficient filtering of SNMP agent supplied data before the affected software stores and displays the data. The stored XSS payload is delivered to the affected software during the SNMP data collection operation performed during a discovery scan. The malicious node utilizes an SNMP agent to supply the desired XSS payload in response to SNMP GetRequest messages for the sysName (1.3.6.1.2.1.1.5) and sysContact (1.3.6.1.2.1.1.4) object identifiers (OIDs). The XSS payload provided for both the sysName and sysContact objects will execute when the user navigates to the page for the malicious node (http://host:8980/opennms/element/node.jsp?node=<ID>) where ID is the malicious node ID).
Exploitation
XSS payloads can be injected into the OpenNMS web application via both SNMP traps and the SNMP agent.
SNMP Trap
The trap OID 1.3.6.1.4.1.43555 was used to send an SNMPv2 trap in which the trap variables contain the single object sysName (1.3.6.1.2.1.1.5) set to the XSS payload <IMG SRC=/ onerror="alert('SNMP Trap Test')"></IMG>. The attack trap was sent using the Net-SNMP snmptrap tool as follows:
snmptrap -v2c -c public OpenNMS_Host '' 1.3.6.1.4.1.43555 SNMPv2-MIB::sysName \
s "<IMG SRC=/ onerror=\"alert('SNMP Trap Test')\"></IMG>"
When the user navigates to the events list page, the XSS payload is returned in a response to the user's browser session and executed. An alert box is displayed that contains the string "SNMP Trap Test", as shown below.
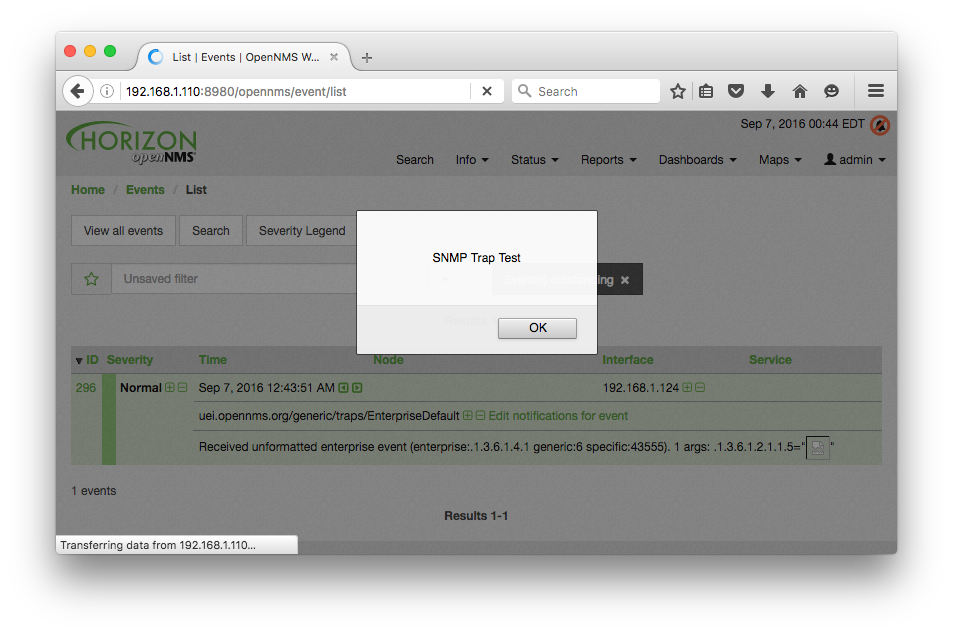
SNMP Agent
A malicious node is operating an SNMP agent that returns the XSS payload <script>alert("sysNameTest");</script> for the sysName (1.3.6.1.2.1.1.5) OID and <IMG SRC=/ onerror=alert(/sysContactTest/) /> for the sysContact (1.3.6.1.2.1.1.4) OID. Once the discovery scan locates and scans the malicious node, the user clicks the Info > Nodes menu item and then clicks the link for the name of the malicious node <script>alert("sysNameTest");</script>. When the node page loads the XSS payloads are returned in a response to the user's browser session and the code is executed. An alert box is displayed that contains the string "sysNameTest", as shown below, followed by an alert box that contains the string "/sysContactTest/".
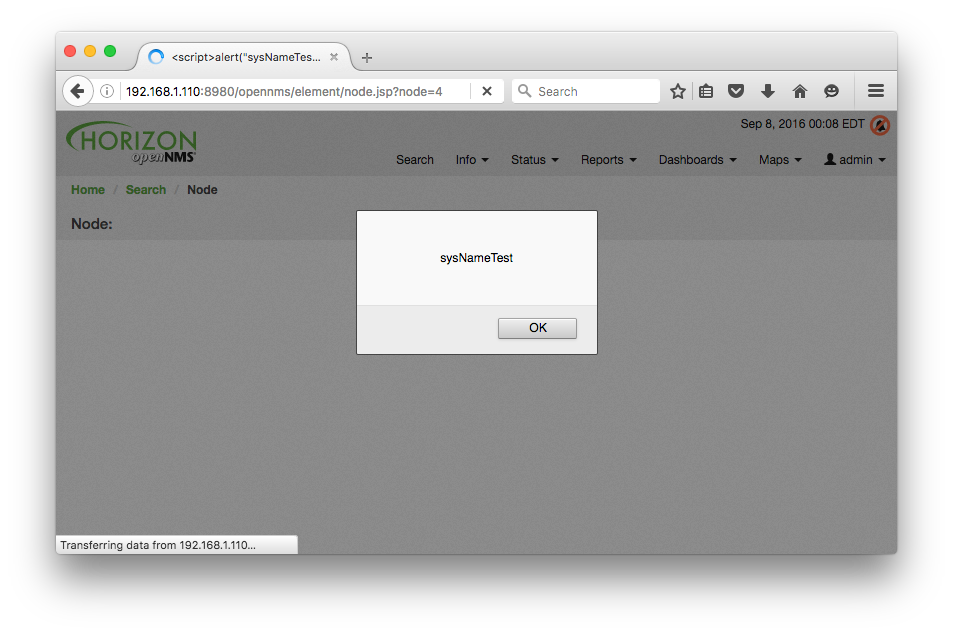
Mitigations
Users should update to version 18.0.2-1 to avoid these issues. Absent this fixed version, there is no practical way to use the SNMP functionality of the product in a safe and secure way. SNMP services should be disabled or blocked until this patch can be applied.
Disclosure Timeline
This vulnerability advisory was prepared in accordance with Rapid7's disclosure policy.
- Sun, Aug 14, 2016: Discovered by Matthew Kienow
- Wed, Sep 07, 2016: Disclosed by the discoverer to Rapid7
- Thu, Sep 08, 2016: Disclosed to vendor by Rapid7 at [email protected]
- Thu, Sep 08, 2016: Vendor acknowledged the issue as NMS-8722
- Wed, Sep 14, 2016: Patch committed as PR#1019
- Sun, Sep 20, 2016: Version 18.0.2-1 released
- Fri, Sep 23, 2016: Disclosed to CERT/CC
- Tue, Sep 27, 2016: CVE-2016-6555 and CVE-2016-6556 assigned by CERT/CC
- Tue, Nov 15, 2016: Disclosed to the public

