Every infosec conference is chatting about the Attack Chain, a visual mapping of the steps an intruder must take to breach a network. If you can detect traces of an attack earlier, you not only have more time to respond, but can stop the unauthorized access to monetizable data and its exfiltration.
Even as attackers and pen-testers continue to evolve their techniques, the Attack Chain continues to provide a great baseline framework to map out your security detection program.
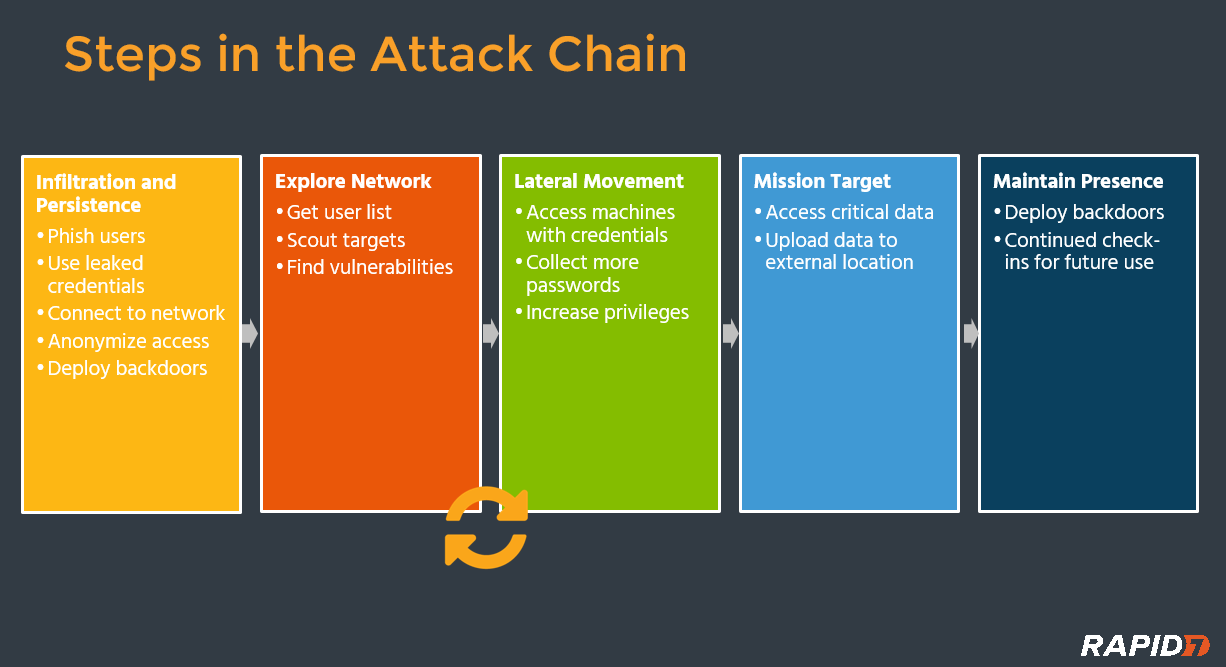
Many of today's detection solutions only alert on breach of critical assets or anomalous data exfiltration. At this point, the attacker is already at Mission Target, and the damage is likely already done. Similarly, it's dangerous to over-invest in a particular step – many organizations are focused on detecting malware, but once an attacker has internal access to the network, they have multiple ways to move from Infiltration & Persistence to Mission Target without using malware at all.
This is where Deception Technology comes in. Justin Pagano, our information security lead, remarks in our latest Security Nation podcast, “Deception tech is a subset of detection that focuses on creating an illusion for attackers…for something they want, to make it easier for you to detect when they're going after it.” And that is the most powerful aspect of deception – it can uniquely detect behavior that is otherwise very hard to spot.
Let's look at four techniques attackers use every day, and how deception can detect these stealthy behaviors.
1. Attacker has internal network access -> fires off a network scan (e.g. Nmap) to find next targets.
One of the rare times an attacker is at a disadvantage is when he/she first lands on the network. This is because the attacker must learn more about the network infrastructure and where to move next.
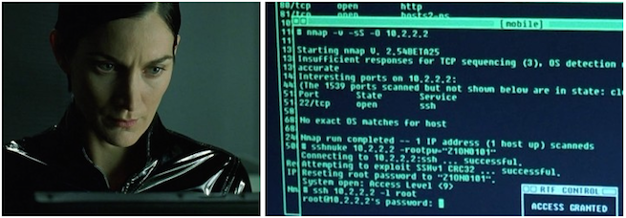
As these methods of gaining information continue to shift, they become increasingly difficult to detect by monitoring solutions today. This ranges from running a vulnerability or network scan to traffic collection and manipulation. Even comprehensive SIEM deployments struggle in detecting early reconnaissance, as it's challenging to identify by log and traffic analysis alone. A countermeasure is to deploy one or multiple Honeypots across the network, a decoy machine/server with no legitimate function for normal users that lurks and reports if it's been scanned, even if only on a single port.
2. Attacker queries Active Directory to see the full list of users on the network. Tries only 1-2 commonly used passwords (e.g. Fall2016!) across all of those accounts – this is referred to as a vertical brute force.
How would you detect this today? In log files, this would appear as one, two failed authentications. There have been cases where an attacker tries a few combinations each week to stay under the radar. This particular attack vector can be detected by creating a dummy user in Active Directory, say, PatchAdmin. This tantalizing user should not have any business purpose or be associated with any employee. If you alert on any authentications to this account, it's a great way to detect that someone is up to no good.
3. Attacker has compromised an employee endpoint. Proceeds to dump credentials / hashes via MimiKatz or other tools. Uses pass-the-hash to continue laterally moving to other machines.
There are a few challenges here. Hash extraction and privilege escalation can be performed using Windows Powershell, so no outside malware is required to be successful. That means the behavior can evade anti-virus and anti-malware defenses that rely on identifying “known-bad”.
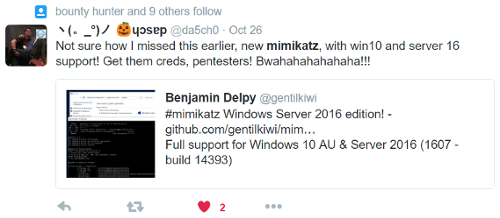
Further, most SIEM solutions don't have endpoint visibility, as it's challenging to setup log forwarding and can result in a lot of added data processing costs. Our Insight Agent PDF automatically injects a set of fake credentials onto each endpoint. If this credential is used anywhere else on the network, you'll receive an automatic alert. Of course, the fake credential doesn't grant access to any system, so they are safe to use.
4. Attacker has access to confidential materials and wants to move it off the network. Files in the folder get zipped and then copied elsewhere, often an external drop server or stolen cloud storage account.
There's a layer of complexity here as the attacker might be impersonating a legitimate employee or is a malicious insider themselves. While data exfiltration is late in the attack chain, it's important to detect critical files being copied or modified. Wade Woolwine, director of breach detection and response notes, “Most of the time, we see command and control actions going over HTTP/HTTPS ports.” This makes exfiltration difficult to detect via firewalls or existing monitoring solutions.
One way to tackle this is to create a dummy file (e.g. Q2-Financials.xls) and place it amongst high-value files. By monitoring all actions taken on this Honey File (opening, editing, copying), you can get file-level visibility without the effort of deploying a standalone File Integrity Monitoring solution. Most importantly, this trap needs to feed into a larger, defense-in-depth detection strategy. It's not hard to identify unauthorized access of critical assets; the challenge is figuring out the users involved, where else the attacker went, and the entire scope of the attack.
InsightIDR, our incident detection and response solution, comes standard with this growing library of deception technology: Honeypots, Honey Users, Honey Credentials, and Honey Files. This is used in combination with our User Behavior Analytics and endpoint detection to find intruders earlier in the attack chain. To see our deception technology in action, check out the Solution Short below.