Effectiveness in security operations is a common theme these days. Often, security teams already have a long list of ways to optimize their current programs and processes, but not enough time to endlessly fiddle with the details. Choosing methods to boost effectiveness usually comes down to scale of impact and, ultimately, priority.
One high visibility way to improve your response times, and, as a result, the success of your team is by shifting from a reactive security posture to a proactive one. Now, we know incident response is a reactive process by nature. But adding proactive elements can help lessen the stress when an incident does arise.
Here are our six recommendations:
1. Know Your Network
The first step in getting ahead in security is to have a clear picture of what you’re looking to protect:
- Which systems (cloud & on-premise) need to be protected?
- Are users logging into systems from their personal devices?
- How many people work remotely and which employees travel?
Make a list of all these endpoints and locations, from systems to devices to users. Then note the security processes, policies, and tools you already have in place to monitor them, and where the gaps are. With this analysis, you can patch the holes and strengthen your security posture.
2. Implement Proper Processes and Procedures
The two most important processes and procedures you should have in place to be proactive are incident response (IR) and intrusion detection (ID). IR and ID serve as your early warning signs when something goes wrong. So if you don’t have them in place, that’s an obvious signal that your security posture isn’t proactive.
To implement this, first look to security monitoring and intrusion detection systems. Then, develop a high-level process for responding to incidents that includes:
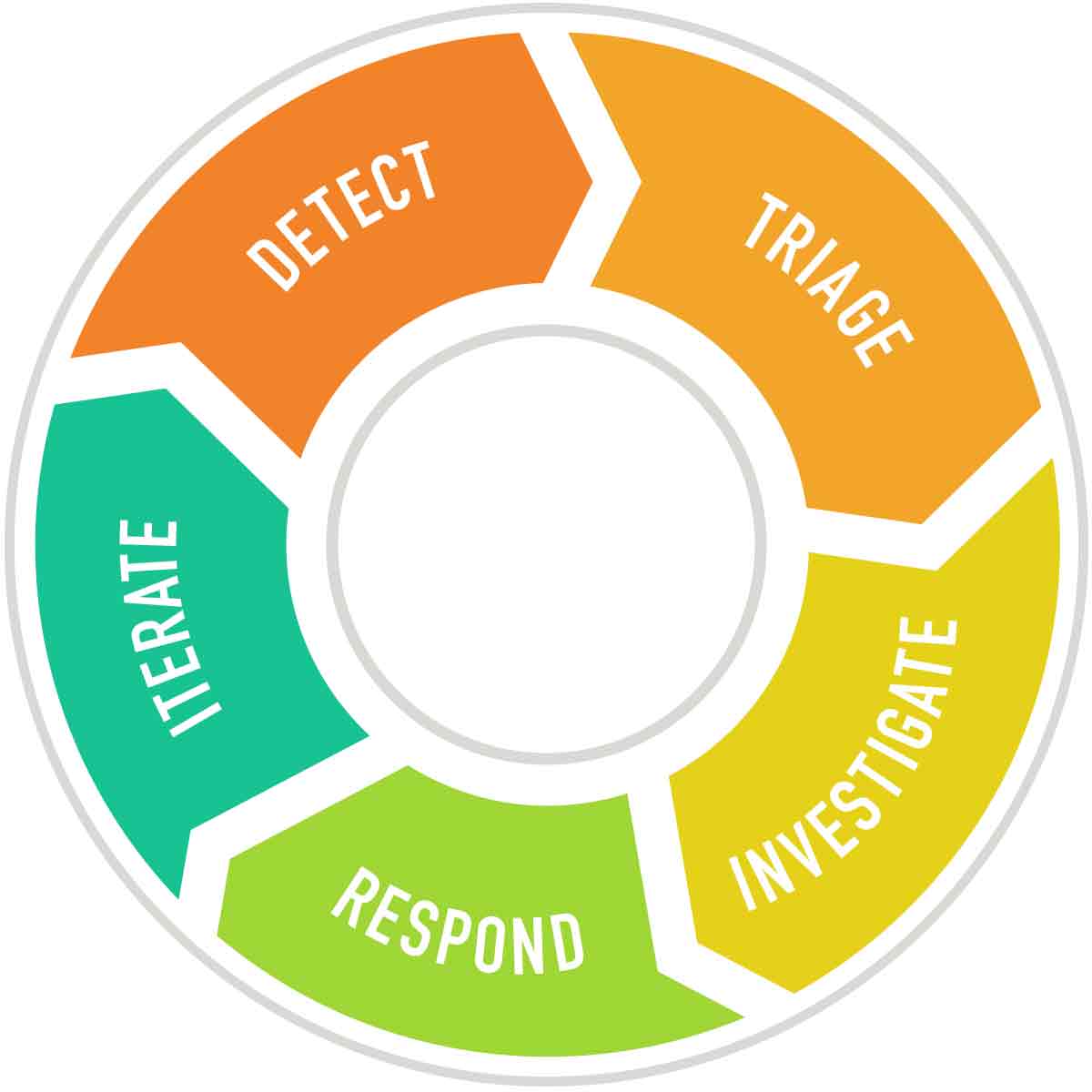
Once you have a clear process laid out, assign team members to each step so that, when an issue arises, everyone knows their place and can jump into action, accelerating the response and enabling you to get ahead.
For example, if malware is detected on your network, rather than scramble to figure out which machine is infected, you can strategically jump into action using a well-defined process. But be sure the process isn’t always linear, see #3 below on why.
3. Think Like an Attacker
One of our favorite tweets-turned-into blogs of last year was by Microsoft security’s John Lambert: “Defenders think in lists, attackers think in graphs.” Though it certainly doesn’t sum up all the challenges of being a defender, it fostered some interesting conversations.
The idea of “defending in graphs" is useful for a number of reasons. A graph allows for multiple hierarchies of response, whereas a list has only a single hierarchy. Plus, since this is how attackers think, we as defenders should, too.
This doesn’t mean that you can’t document and share processes and standardize common procedures. The point is you should be thinking about the relationships between present evidence and then determining the best course for investigations. This approach gets us away from the rigidity that plagues many security teams, enabling us to move faster and more strategically.
4. Create a Culture of Security Ownership
Effective and proactive security cannot be achieved without an organization-wide dedication to security. If employees don’t know what a secure password is and don’t use two-factor authentication, yet email compromises are on the rise, it can be impossible for security to get ahead. Instead, everyone needs to know the importance of security measures like two-factor authentication policies so that the company can become stronger together.
In this post, we define how to create a culture of security ownership. In short, it involves:
- Aligning security measure to business value
- Empowering everyone to become a security advocate
- Providing practical training
- Rewarding and enforcing security efforts
- Creating an open feedback loop
By creating an organization-wide emphasis on security, you can share the responsibility and get ahead of threats — ideally even before they become an incident.
5. Orchestrate and Automate Security Where Possible
With the right tools, processes, and people in place, you can begin to automate and orchestrate security to realize real reductions in time-to-response, as well as improved operational efficiencies.
As we explain in our latest eBook, “Security Automation Best Practices,” security automation can streamline repetitive tasks (e.g. phishing investigations) into cohesive and automated workflows. With manual and mundane tasks out of the way, teams can instead focus on more strategic and impactful work — the work that can truly get you and your team ahead.
6. Conduct Blameless Reviews Post-Incident
The key to an effective review after an incident has occurred is doing it in a way that doesn’t place blame on anyone. Not only will placing blame alienate people, it can also disincentivize them from sharing information in the future.
Instead, blameless reviews open up the doors of communication in a collaborative and honest way, enabling your team to move forward and accelerate time-to-response.
Layered Security is Proactive Security
Nothing is an absolute guarantee of security. Even with layers of protection in place, bad actors can still get in. But the more strategic layers you put in place, the better protections you have and the faster you can get ahead of many threats to your organization.
The benefits of taking the time to implement these layers now will help you down the road — we can guarantee you that.
Looking to make other processes more efficient? Download our guide on creating security processes that solve practical problems.
