Synopsis
As a penetration tester I have many tools that I use to help with web application testing, but the one tool that never lets me down is Burp suite by portswigger. Burp suite is an intercepting proxy that allows you to modify and inspect web traffic, it comes in two flavors, free and paid. The free version is powerful enough to assist any pen test engineer, whereas the paid version will add extra features to make your tests go smoother and faster.
I am going to walk you through the beginning of how to setup Burp suite and make it work efficiently with Firefox. Before you continue please make sure you own your own web application and its hosting server. I will recommend a virtual server you can download and place on your own network to test without worrying about any legal issues. “DO NOT” use any server that is not yours.
Downloading and Installing Burpsuite
To download Burp suite, please visit https://portswigger.net/burp/download.html and choose the Free Edition. Burp suite comes in two application packages, you can choose to download the exe format for Windows or if you are on Linux or Mac you can choose the java platform. The java package will work on any OS that handles java such as Windows, Mac or Linux. We will stick with the java version in this article due to its broad platform use.
Downloading bWAPP, an extremely buggy web app
bWAPP can be downloaded as a Virtualbox server or you can download the files necessary to run on your own Apache server. To download the Virtual Box instance go to https://sourceforge.net/projects/bwapp/files/bee-box/ and to download the files for Apache go to https://sourceforge.net/projects/bwapp/files/latest/download?source=files . I am not going to show you how to install Virtualbox or show you how to install the files if you already have Apache installed on another server. Please follow the instructions that bWAPP provides.
Install FoxyProxy for Firefox.
FoxyProxy is an addon for Firefox that will let you switch between multiple proxy servers. To install FoxyProxy please go to https://addons.mozilla.org/en-US/firefox/addon/foxyproxy-standard/ and follow the instructions. Once the installation is done it should restart Firefox and when it comes back up you should now see an icon between your search bar and address bar.

Let’s get hacking
Now that we have everything we need to start exploiting our new “buggy” server, we need to open Burpsuite to configure it. Please follow the steps below.
- Choose the “Proxy” tab and then the “Options” tab.
- Under proxy listeners you will see a listening ip address and port already setup and running. Normally it is 127.0.0.1 and port 8080. If you are using port 8080 for anything else on your computer you will need to edit the setting and change the port to something you are not using. Click the Intercept tab which is to the left of the Options tab and make sure Intercept is off.
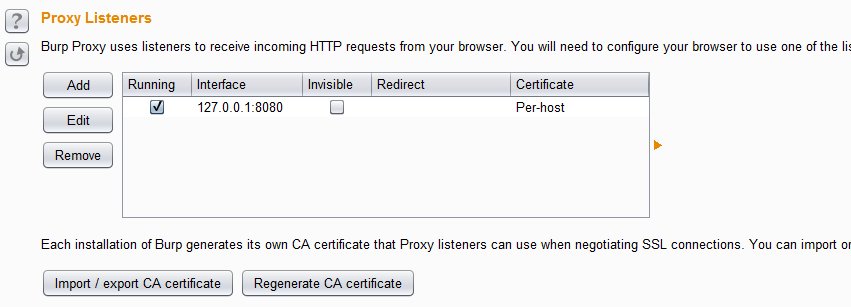
3. Now open Firefox and left click on the FoxyProxy icon. You will see a new window open, you will need to choose “Add new proxy”.
4. Under Manual Configuration enter 127.0.0.1 for Host or IP Address and 8080 for Port. That’s it, press OK at the bottom and then close out of the FoxyProxy config window.
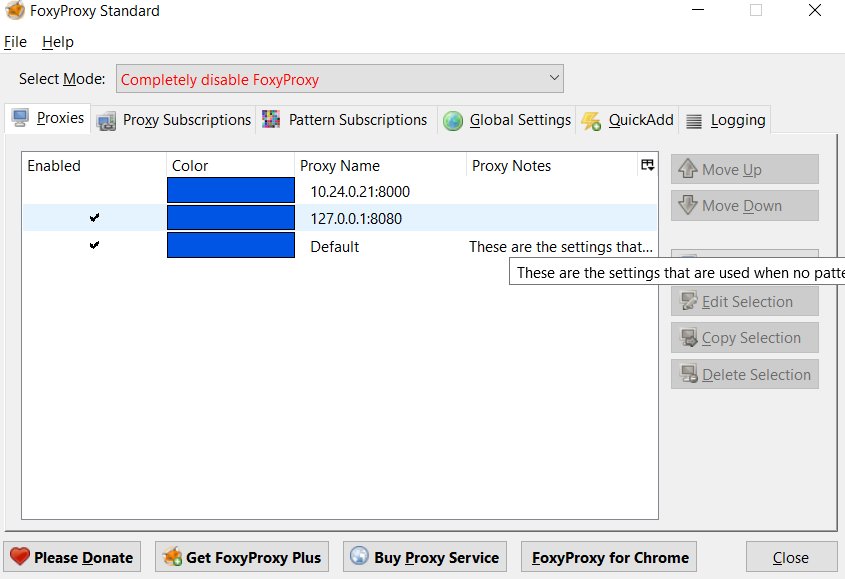
5. In Firefox right click on the FoxyProxy icon and choose the new proxy you setup. Once a proxy is chosen the little icon should turn blue and start turning in circles.
6. Now go to the address of bWAPP that you setup. The address should be either your apache server you already had setup and copied the files needed for the bWAPP web page or the virtual box virtual server that you setup. For me it was http://10.24.0.247/bWAPP/login.php (remember to have followed the setup instructions from bWAPP)
7. Login in with user: bee and password:bug
8. Under the bugs menu choose security low and SQL Injection (AJAX/JSON/jQuery).
9. With this being an AJAX/JSON feature a search will automatically start displaying into the page when you start typing so we will not be able to tamper with the URL. This is where Burp comes in.
10. Start typing in a movie. I know for a fact The Incredible Hulk is listed. Type just Incr and then switch over to your burpsuite.
11. Under the Proxy Tab and HTTP History right click on the last GET request and send it to the Repeater.
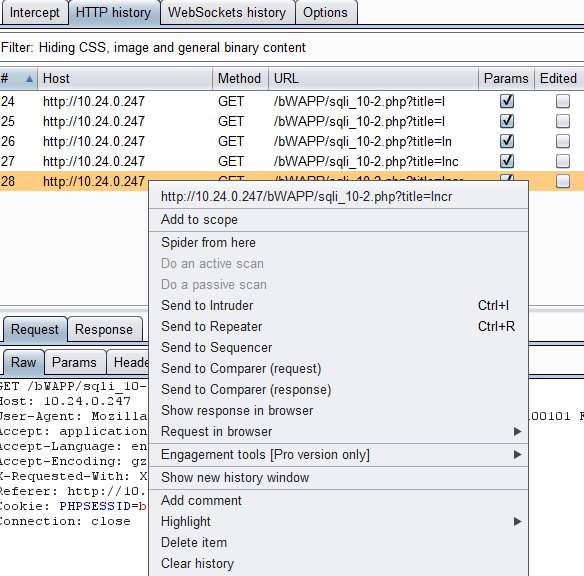
12. Click the Repeater Tab and you will see the RAW tab. In the RAW tab you will see in the first line “GET /bWAPP/sqli_10-2.php?title=Incr HTTP/1.1” after the word Incr type ” %’+or+title+like+’%Knig” The %cab will also search for any movies that start with cab in its name and also start with Incr.
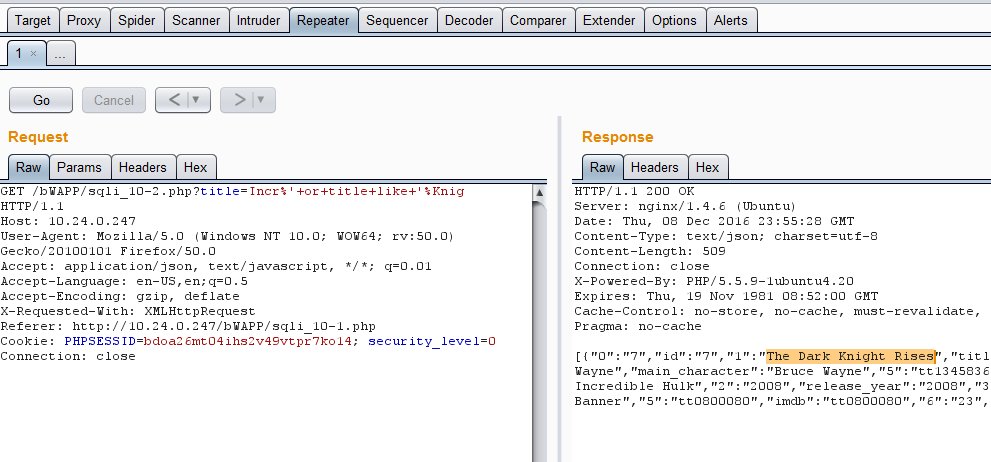
13. Press Go at the top and in the response at the bottom you will now see that it shows not only The Incredible Hulk but also The Dark Knight Rises.
Conclusion
This proves that I have created a working injection. From here we can now start extracting more information from the database with other sql commands. This does not always work for a lot of web applications. Most web app programmers will prevent these types of exploits by taking defenses. To view a cheat sheet for SQL injection prevention visit OWASP’s web site by going to https://www.owasp.org/index.php/SQL_Injection_Prevention_Cheat_Sheet