Synopsis
Authentication is a critical step that forms the basis of trust on the Internet or any network based transactions. To state simply it verifies that the person or entity is who they claim to be. However authentication mechanisms are constantly under attack. Two Factor Authentication is an evolution to counter these security threats. This tutorial takes a look at various types of authentication methods and technologies behind them.
Different Types of Authentication Factors
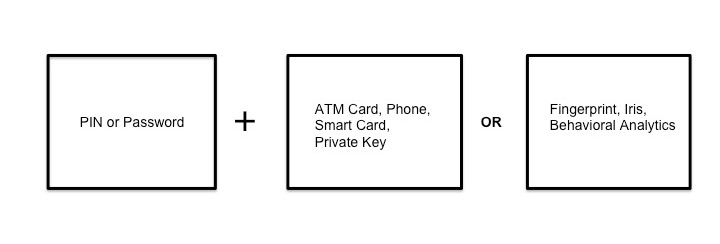
Three distinct factors are used while authenticating.
- “Something One Knows “or the Knowledge Factor (Passwords, PIN)
- “Something One Has” or the Possession Factor (ATM, Phone, Token, Device, PKI certificates)
- “Something One Is” or Biometric Factor (Fingerprint, Iris, Voice, Behavioural Analyses)
Knowledge factors such as passwords suffer from the vulnerabilities below.
- Brute Force : Guessing the weak passwords by attackers, dictionary attacks or shoulder surfing.
- Phishing/Vishing: Masqueraded fraudulent links can be sent over emails or sms to lure people to give away their password. Vishing refers to fraudulent calls.
- Key Loggers: Malware sits dormant on your device to capture and send passwords to the attacker.
- Man in the Middle Attacks: A person or a software sniffing the traffic any point between your device, router(wi-fi), ISP and Telecom provider.
Posession factors suffer from theft, accidental loss and duplicates. Biometric factors suffers from image capture and replay attacks. The solution therefore is to combine two or multiple factors together to provide far better security and address a large number of vulnerabilities.
Picture : Basic Scheme of Two Factor Authentication
The Knowledge Factor (Something One Knows)
Passwords
These are usually set during creation of accounts or issuing of cards and can (and should) be changed often. The stronger the passwords are, better is the security and will help withstand dictionary or brute force attacks.
Personal Information
These are mostly personal (birthdays, pet names, mother’s maiden names etc) information, which a stranger wouldn’t know.
Pre-Set Information.
Questions, Images are set during signups there are another form of memory based knowledge factors.
The Possession Factor (Something One Has)
These focus on verifying the ownership(posession) of devices and are implemented as one of the following.
- OTP (One Time Password)
- Phone to PC communication: Frequency(Audio), QR Scanners, Images
- PKI smartcards
There tends to be a trade off between convenience and security and there is lot of innovation underway in this space.
One Time Password
OTP is the simplest of all and it uses technique of synchronised number generation to prove the possession of hardware. One Time Passwords are random numbers (so they can not be predicted by hackers) valid for a small time window (smaller the better). Common technologies of generating OTPs are,
Time Synchronisation (TOTP): The backend (authenticating) server and the user side share a synchronised clock and is part of the OTP generation process along with predefined secret, set during the enrolling.
Algorithm Based (HMAC OTP): A mathematical algorithm, which generates random numbers based on pre-set random starter number and a secret hash function. Example: repeated hash (hash chain) on a set number. So every new OTP is a hash of the old OTP.
OTP generated is delivered to user in multiple ways:
- Over SMS or Call (proves that you have the phone): One time passwords generated by the servers and sent over a separate channel (not the internet but wireless networks) can be very effective as hacker needs to break into two channels before he can control the account. However this is vulnerable to vishing attack if the time window of the validity is high. This is also vulnerable to man in the middle attacks.
- Software or Hardware tokens (proof that you own the token and the Device): Hardware tokens are these tiny devices, which are time synched to a backend and produce identical random numbers. The hardware tokens can be quite cumbersome as you need to carry them around and if you have many accounts, it can be an impossible task. Software token are easier to manage and many popular ones such as Google authenticator can provide a very effective OTP solution.
- Print Cards: A very low cost way is to send print the OTPs on a paper and use them one after the other. A variation of these techniques is used for proving the card existence (say ATM card) is known as “Printed Grid”. Usually a matrix of number is printed on the back of the card and the website asks for random column and row numbers so that only the owner of the card can enter right numbers.
Phone to PC Communication
Another form of proving that one owns the phone during the transaction is to hold up the phone in front of the PC either to scan the QR code with the phone app, which in turn communicates with the backend server to complete the logic process.
In some cases invisible frequencies are used to communicate between PC and phone app.
A visual technique involves, Image banks and random images displayed between PC and phone can then be used to select the image and complete the login.
PKI (Public Key Infrastructure) Smart Cards
This is strongest security mechanism so far as they provide for mutual authentication (of the user and the website) and thus effectively dealing with phishing and many forms of man in the middle attacks. These can be in both software and hardware forms. The basic principle here is ability to communicate in an encrypted format without the need to exchange the secret keys before hand.
The way it works is, every website and the user has a pair of matched keys called public and private keys. The corresponding private key can only unlock the message encrypted with a public key. During the start of the communication user side uses servers side public key to encrypt and send its public key (or another secret key), which then is decrypted by the server side private key and used for encrypting the communication to user. This provides a very strong secure channel for both sides to communicate.
The key pair is downloaded (or sent over mail for hardware tokens) during signup (enrolment). Keys on the user side are further secured using a PIN or password. So the second factor here is the additional PIN entered into the token or the app which will then start the PKI authentication.
FIDO Alliance
FIDO (Fast Identity Online), is separate class of solution, but is under PKI smart card here, as it does use the technology and is a “Posession Factor”.
FIDO Alliance is attempting to solve cumbersome issues of owning and remembering multiple passwords, pins and tokens. It has written two specifications to address two distinct problems i.e lack of interoperability among strong authentication devices as well as the problems users face with creating and remembering multiple usernames and passwords.
- Password Less Experience (UAF Standard, Biometric based)
- Second Factor Experience (U2F Standard, PKI smart card that can work with any number of sites)
FIDO is gaining quite an acceptance due to the industry alliances and a nifty solution.
Biometric (Something One Is)
Physical
Physical biometric works on the premise of pre stored image of your fingerprint, voice or the iris. During the transaction a scan is done to get the corresponding biometric and compare with the stored backend image to authenticate. With many types of scanners getting integrated with the devices this is becoming more prevalent and easy to use.
However this suffers from a critical flaw. It works on stored(albeit hashed) images of your biometric and if compromised once can become a single point of failure.
Behavioural
This works on the premise that people tend to more or less behave the same way. This requires analyses and pattern recognition of historical transaction data of a person. During a new transaction the likelihood of that person is analyses based on the patterns and used as a factor while authenticating.
Further Reading and References
FIDO Alliance
http://www.networkworld.com/article/2227691/opensource-subnet/open-source-2-factor-authentication-wikid.html