Synopsis:
Suricata is an open source threat detection engine that was developed by the Open Information Security Foundation (OISF). The Beta was released at the end of 2009, with the standard version coming out in the middle of 2010. Suricata can act as an intrusion detection system (IDS), and intrusion prevention system (IPS), or be used for network security monitoring. It was developed alongside the community to help simplify security processes. As a free and robust tool, Suricata monitors network traffic using an extensive rule set and signature language. Suricata also features Lua scripting support to monitor more complex threats. The Suricata engine and HTP library are available under the GPLv2, with versions that run on Windows, Mac, Linux, Unix and FreeBSD.
Why Choose Suricata?
Suricata is an excellent, low-cost tool that helps to give greater insight into a network. Despite this, it needs to be viewed as a single layer in a comprehensive security plan, rather than a complete solution to security issues.
One of the most common alternatives is Snort, which has long been a favorite tool of many admins. Although Suricata is much newer, it has several advantages. The two are based on different architectures, however they can both use the same signatures. A key difference between them is that Suricata is multi-threaded, which means that it can use multiple cores at once. Engaging multiple CPUs allows Suricata to process multiple events at the same time without having to interrupt other requests. Multi-threading also enables Suricata to load balance across the CPUs, as well as improve overall performance in network traffic analysis. This is advantageous because it means that Suricata can process large quantities of traffic without needing to cut back on rules.
The engine is designed to take advantage of the newest multi-core CPU chip sets, as well as utilize hardware acceleration for greater processing power. The high efficiency of Suricata, its IP reputation support and automated protocol detection all help to make it an effective tool for giving greater visibility into a network.
Suricata is compatible with a range of third party Snort tools. It uses standard input and output formats like YAML and JSON, which allow easy integration with tools like Splunk, Kibana and Elasticsearch. Another key advantage of Suricata is that it has an excellent development and support community. Together they have built up extensive resources including installation guides, user guides, FAQs and troubleshooting.
Using Suricata as a Host Based IDS, Passive IDS or an Active Inline IDS and IPS
Suricata can be used in three major roles. The simplest is to set it up as a host based IDS, which monitors the traffic of an individual computer. This isn’t especially efficient or practical, but it can be a great way for someone to familiarize themselves with Suricata. As a passive IDS, Suricata can monitor all of the traffic that goes through a network and notify the administrator when it comes across anything malicious. When Suricata is set up as an active inline IDS and IPS it can monitor inbound and outbound traffic. It can stop malicious traffic before it enters the network, as well as alert the administrator.
Setting Suricata up as an IPS might seem like the most obvious choice – why would you want to only monitor malicious traffic instead of blocking it? Unfortunately, implementing an IPS isn’t that simple – they often block legitimate traffic as well if they aren’t configured properly. It can be quite difficult to tune the rules to make sure that only malicious traffic is blocked. If you are considering using Suricata as an IPS, it may be best to use it as an IDS first to make sure that it isn’t blocking any important traffic. Another issue with using Suricata as an IPS is that it can introduce a single point of failure into your systems.
The Open Information Security Foundation
The OISF is a non-profit organization that aims to build a supportive community around open source security technologies. It was formed in 2008 and is led by a team of programmers, security experts and others who share a passion for open source security. The OISF aims to provide robust and relevant security technologies to help combat a range of threats. The main project of the OISF is Suricata, but they also support and engage with the community through a range of conferences, working groups and training events.
The organization has formed partnerships with Emerging Threats and other strategically advantageous groups to help provide up-to-date and comprehensive rule sets for their engine. The OISF is funded by the US Department of Homeland Security (DHS) as well as the OISF consortium, which is composed of numerous private companies. In return for their support, these companies are granted a non-GPL limited license for the Suricata engine.
Installing Suricata
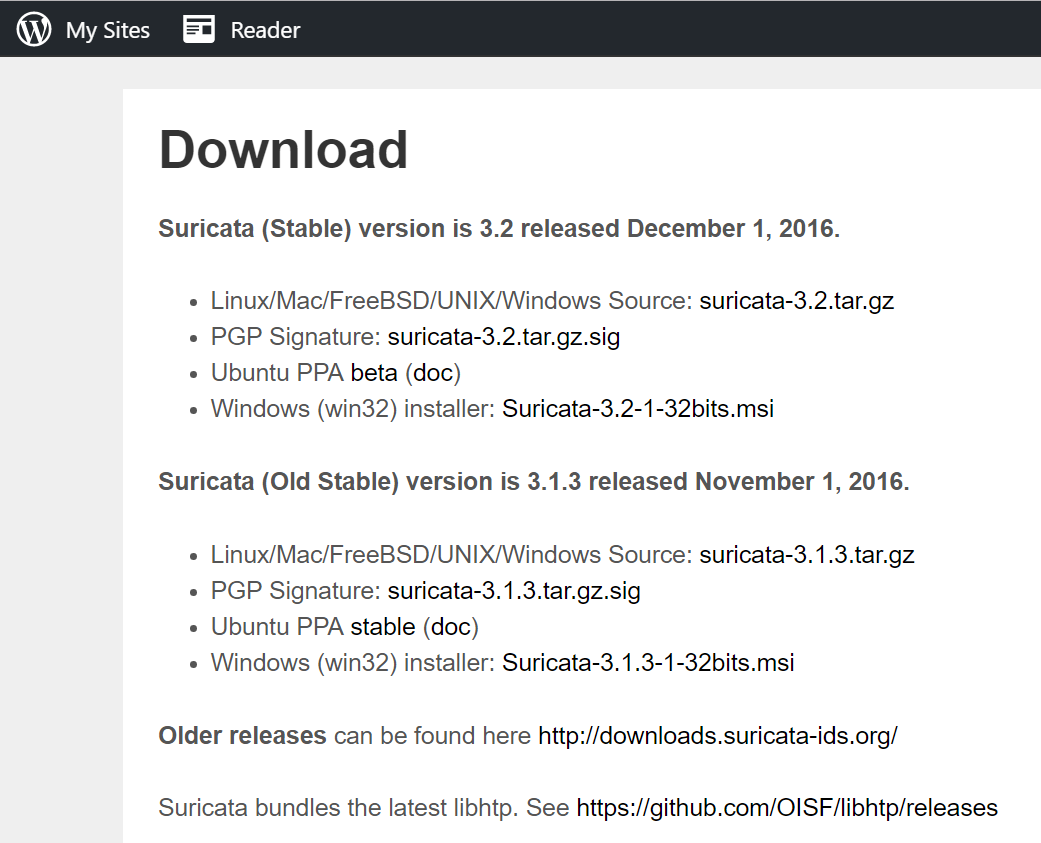
There are two main options for downloading and installing Suricata. For a simple auto-installation, head to the downloads page of their site and select the version that is best suited to your system. Version 3.2 is available on Windows, Mac, Linux, FreeBSD and Unix. If you choose this option, just install it like any other program.
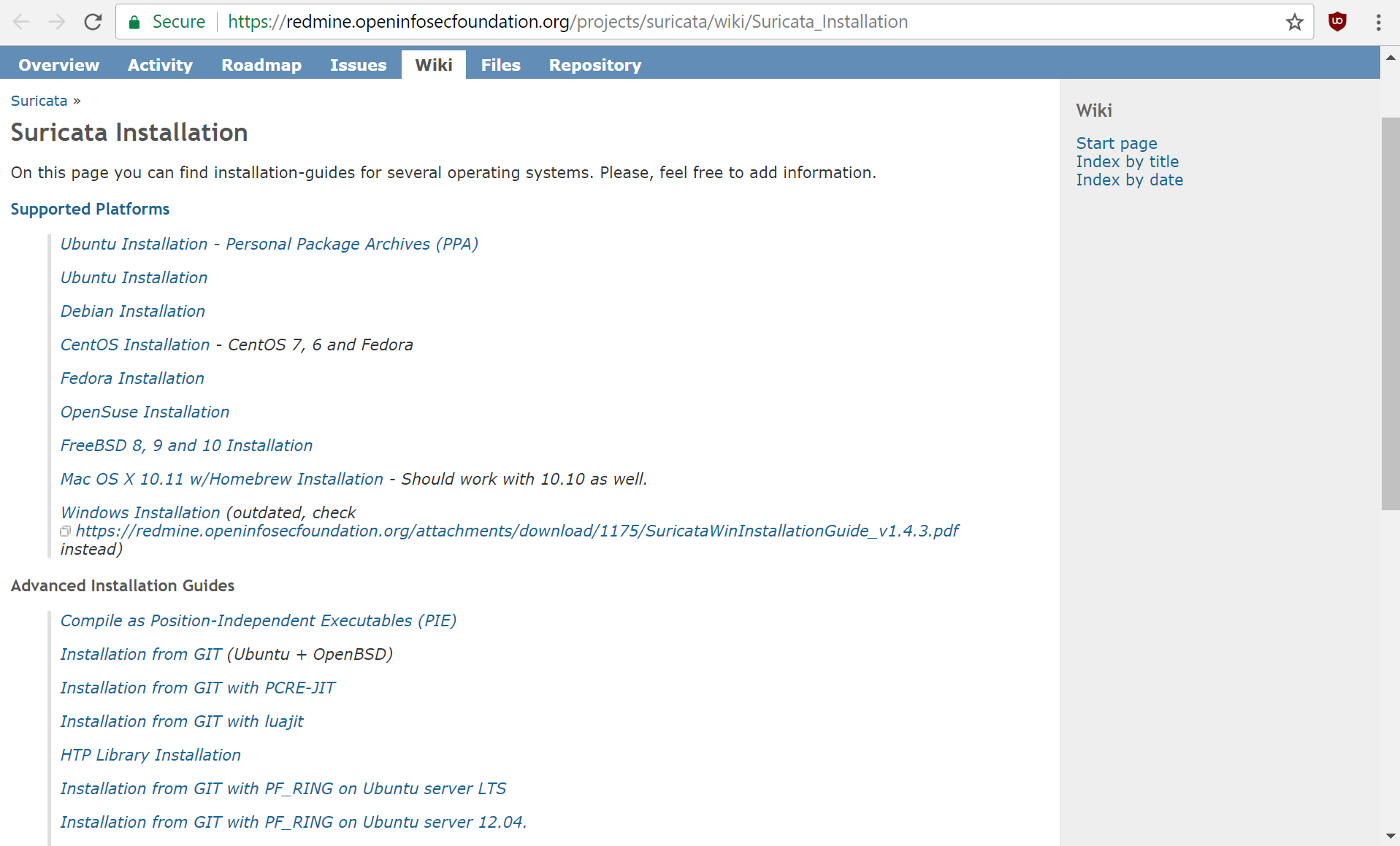
If you intend to compile your own executable Suricata IDS or IPS, you will need to visit their installation page instead. Select the guide for your system and read through the instructions. The OISF offer guides for all supported platforms, as well as advanced installation guides for more complex configurations.
Setting Up Suricata
Once you have downloaded and installed Suricata, you will need to do a basic setup where you create a directory for Suricata and the configuration files. The installation guides offer detailed information on how to get Suricata up and running. You will also need to download and configure a rule set that enables Suricata to register threats. Suricata’s partnership with Emerging Threats has provided an excellent resource for extensive rule sets. These are updated each day with the latest malicious traffic and IP addresses. For troubleshooting, the OIFC has set up a large amount of support documentation. This includes quick start guides, user guides and FAQs, which are all available on their Wiki.