This post describes three vulnerabilities in the Double Robotics Telepresence Robot ecosystem related to improper authentication, session fixation, and weak Bluetooth pairing. We would like to thank Double Robotics for their prompt acknowledgement of the vulnerabilities, and in addressing the ones that they considered serious. Two of the three vulnerabilities were patched via updates to Double Robotics servers on Mon, Jan 16, 2017.
Credit
These issues were discovered by Rapid7 researcher Deral Heiland. They were reported to Double Robotics and CERT/CC in accordance with Rapid7's disclosure policy.
Product Affected
The Double Telepresence Robot is a mobile conferencing device. Its mobility allows the remote user to roam around an office for meetings and face-to-face conversations.
Vendor Statement
From Double Robotics' co-founder and CEO, David Cann:
At Double Robotics, we seek to provide the best experience possible for our customers, which means not only providing an agile, innovative technology, but also, the highest level of safety and security. Rapid7's thorough penetration tests ensure all of our products run as securely as possible, so we can continue delivering the best experience in telepresence. Before the patches were implemented, no calls were compromised and no sensitive customer data was exposed. In addition, Double uses end-to-end encryption with WebRTC for low latency, secure video calls.
Summary of Vulnerabilities
-
R7-2017-01.1: Unauthenticated access to data
- An unauthenticated user could gain access to Double 2 device information including: device serial numbers, current and historical driver and robot session information, device installation\_keys, and GPS coordinates.
-
R7-2017-01.2: Static user session management
-
The access token (also referred to as the driver
\_token) which is created during account assignment to a Robot was never changed or expired. If this token was compromised, it could be used to take control of a robot without a user account or password.
-
The access token (also referred to as the driver
-
R7-2017-01.3: Weak Bluetooth pairing
- The pairing process between the mobile application (iPad) and robot drive unit does not require the user to know the challenge PIN. Once paired with the robot drive unit, a malicious actor can download the Double Robot mobile application from the Internet and use it (along with the web services) to take control of the drive unit.
Vulnerability Details and Mitigations
R7-2017-01.1: Unauthenticated access to data
In the following example, critical information related to a session was accessed using the URL https://api.doublerobotics.com/api/v1/session/?limit=1&offset=xxxxxxx&format=json. By incrementing the "offset=" number, information for all historical and current sessions could be enumerated:
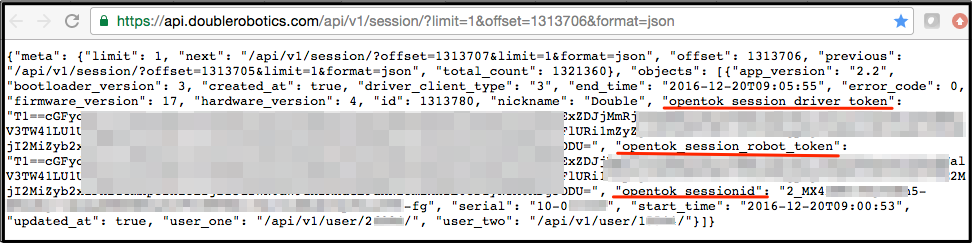
In the next example, robot and user installation keys were enumerated by incrementing the "offset=" number in the URL https://api.doublerobotics.com/api/v1/installation/?limit=1&offset=xxxxxxx&format=json as shown below:
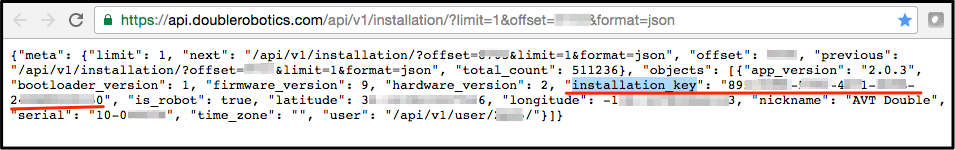
On Mon, Jan 16, 2017, Double deployed a server patch to mitigate this issue.
R7-2017-01.2: Static user session management
Although the driver\_token is a complex, unique, 40-character token (and so unlikely to be guessed), it can still be enumerated by anyone who has access to the Double Robot iPad or is successful in creating an SSL man-in-the-middle attack against the device. For example, via a successful man-in-the middle attack or access to the robot iPad's cache.db file, a malicious actor could identify the robot\_key as shown below:
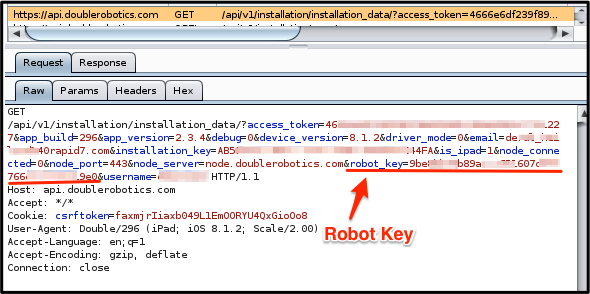
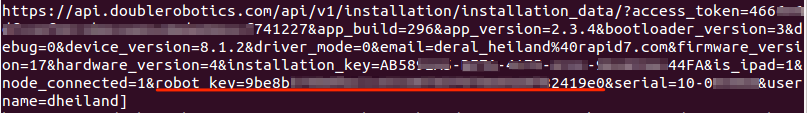
Using this robot\_key, an unauthenticated user could enumerate all of the user access tokens (driver_tokens) which allow remote control access of the robot. An example of this enumeration method is shown below:
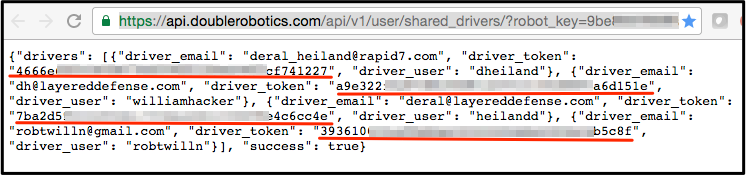
On Mon, Jan 16, 2017, Double Robotics deployed a server patch to mitigate this issue. The API queries described above no longer expose related session tokens to the Double device.
R7-2017-01.3: Weak Bluetooth pairing
The exposure of this vulnerability is limited since the unit can only be paired with one control application at a time. In addition, the malicious actor must be close enough to establish a Bluetooth connection. This distance can be significant (up to 1 mile) with the addition of a high-gain antenna.
On Mon, Jan 16, 2017, Double Robotics indicated it did not see this as a significant security vulnerability, and that it does not currently plan to patch. Users should ensure that the driver assembly remains paired to the control iPad to avoid exposure.
Disclosure Timeline
This vulnerability advisory was prepared in accordance with Rapid7's disclosure policy.
- Dec 2016: Discovered by Rapid7's Deral Heiland
- Mon, Jan 09, 2017: Disclosed to Double Robotics
- Mon, Jan 09, 2017: Double Robotics acknowledged the vulnerabilities
- Mon, Jan 16, 2017: R7-2017-01.1 and R7-2017-01.2 were fixed by Double Robotics via server patches
- Tue, Jan 24, 2017: Disclosed to CERT/CC
- Wed, Jan 25, 2017: Rapid7 and CERT/CC decided to not issue CVEs for these vulnerabilities. R7-2017-01.01 and 01.02 were present in Double's web application server. As there was only one instance of the affected software, and no user action was required to apply the fixes, no CVE is warranted. R7-2017-01.03 is a exposure for users to be aware of, but it only allows control of the drive unit if pairing is successful. User data cannot be modified without additional compromise.
- Sun, Mar 12, 2017: Disclosed to the public