On March 9th, 2017 we highlighted the availability of a vulnerability check in Nexpose for CVE-2017-5638 – see the full blog post describing the Apache Struts vulnerability here. This check would be performed against the root URI of any HTTP/S endpoints discovered during a scan.
On March 10th, 2017 we added an additional check that would work in conjunction with Nexpose's web spider functionality. This check will be performed against any URIs discovered with the suffix “.action” (the default configuration for Apache Struts apps).
It may be necessary to configure your scan template to direct Nexpose to specific paths on web servers if they cannot be discovered during the default spidering process. If your app's URI is not linked to from any of these discovered pages, you will need to configure these paths. Follow the steps below to configure your scan template:
Let's say you have 2 Apache Struts apps in the following locations:
Example App URL 1: http://example.com/org/apps/myapp.action
Example App URL 2: http://example.com/other/org/different.action
In Nexpose's web UI, select the scan template that you wish to use (Administration → Templates → manage)
Go to the Web Spidering section of the template (WEB SPIDERING → PATHS) and then add all the paths you wish Nexpose to try accessing to the “Bootstrap paths” section. PLEASE NOTE: Each path must be followed by a trailing slash and are comma separated (e.g. /org/apps/,/other/org/):
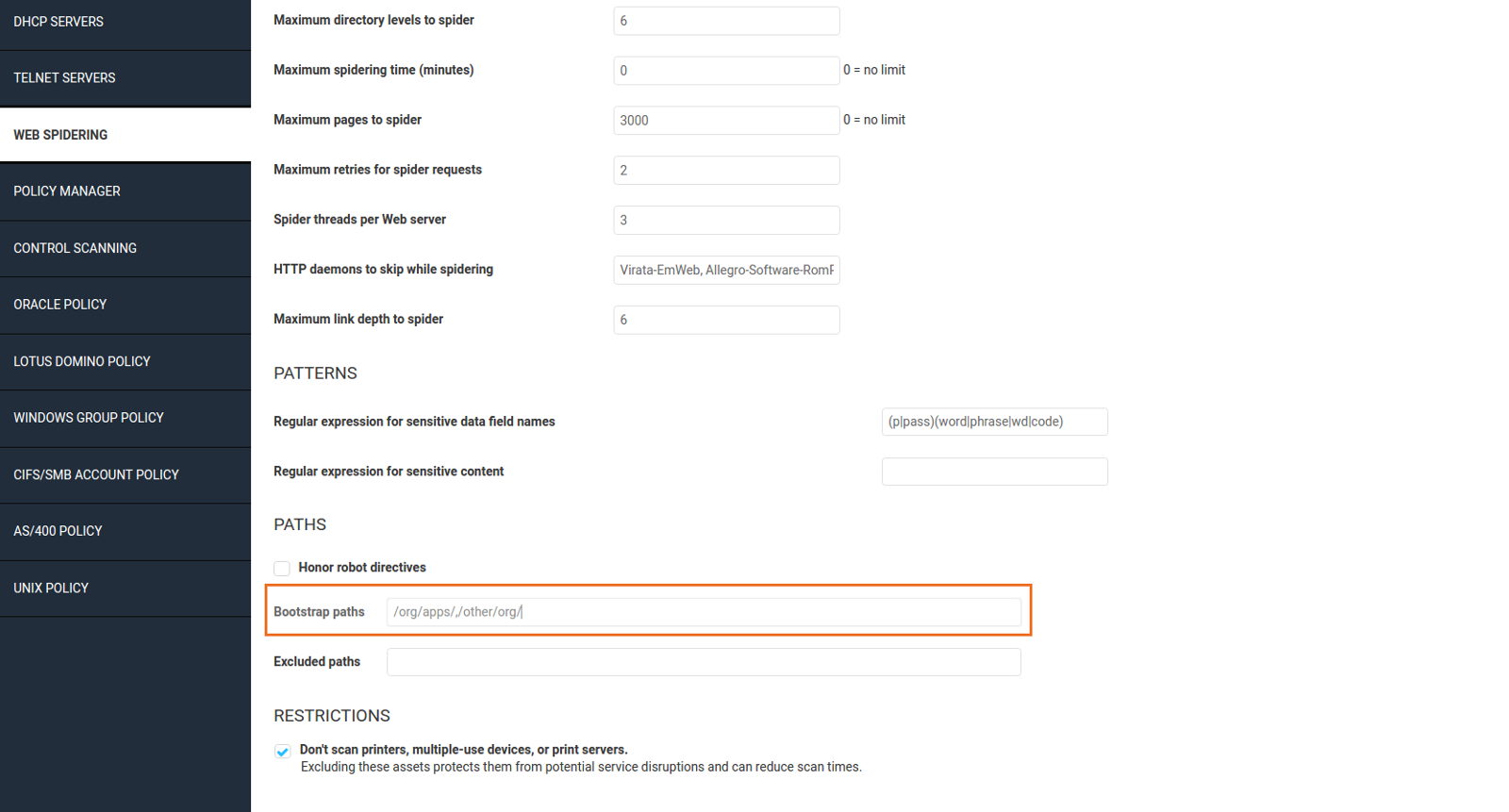
Once you configured the paths, save the changes to the template.
Not a Nexpose customer and want to scan your network for the Apache Struts vulnerability? Download a free trial of Nexpose here.