Currently, phishing is seen as one of the largest infiltration points for businesses around the globe, but there is more to social engineering than just phishing. Attackers may use email and USB keys to deliver malicious files to users in the hopes of gaining access to an organization's network. Users that are likely unaware that unsolicited files, such as a Microsoft Word document with a macro, may be malicious and can be a major risk to an organization. Metasploit Pro can assist in the education of employees about these attack vectors.
Metasploit Pro's Social Engineering functionality is often used for its phishing capabilities, but it has other options - such as USB key drops and emailing of malicious files - that are able to obtain sessions on a target's device. As part of an internal training engagement or penetration test, these features will give more insight into the organization's defenses against social engineering attacks. This post will cover emailing malicious files utilizing the current Microsoft Word macro file format module.
To begin, start a new custom campaign and configure your email starting with the email header and target list, similar to a phishing campaign. For Attack Type, select Attach File, give the attachment a name and select File format exploit.
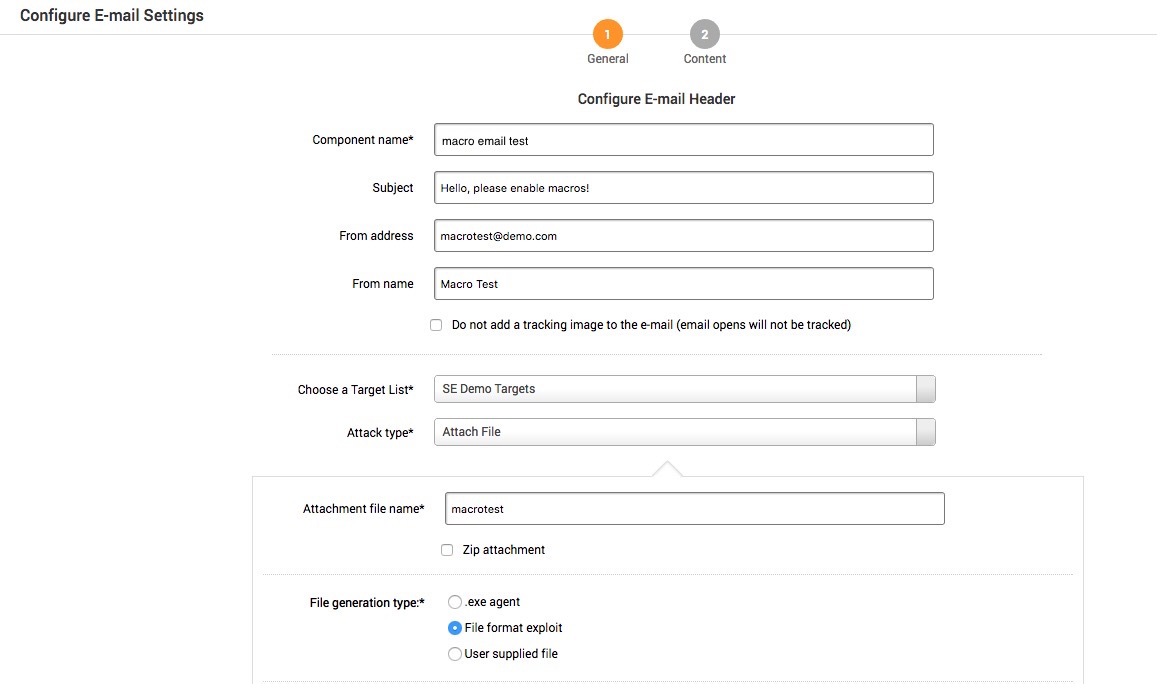
Search for “macro” and select “Microsoft Office Word Malicious Macro Execution”. This will create a Microsoft Word document with a macro that will deliver a payload and open a shell back to Metasploit Pro. Configure your target settings (I'll be using the OS X Python target for this example) and payload options. Then use the “BODY” field for the content of the Word document. (You can use plain text or xml formatted data, which will be injected between the <p> and </p> tags of the Word xml document.) And click OK.
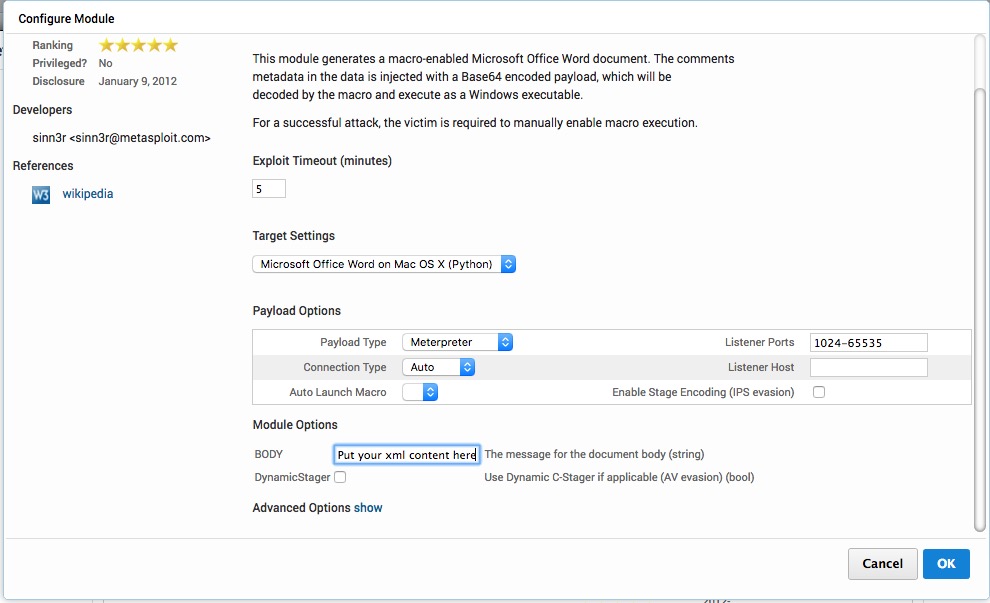
Click “NEXT” and format your email. Save your changes and configure your email server if you haven't done so already.
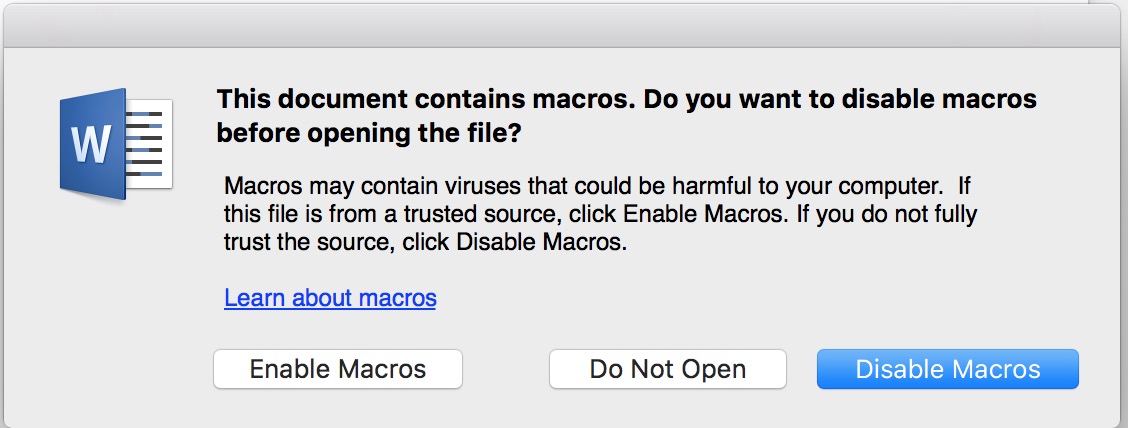
Launch your campaign and the email(s) will be sent to all the members of your target list and a listener will be opened for the payload. The recipients will need to enable macros in order for the payload to launch. All those that enable the macro on the specified platform will have a shell that connects back to your Metasploit instance.
Your campaign findings will list the number of targets, recipients that opened the email and number of sessions opened. If any sessions are opened, you'll be able to interact with that session as you would any others via the Sessions page.
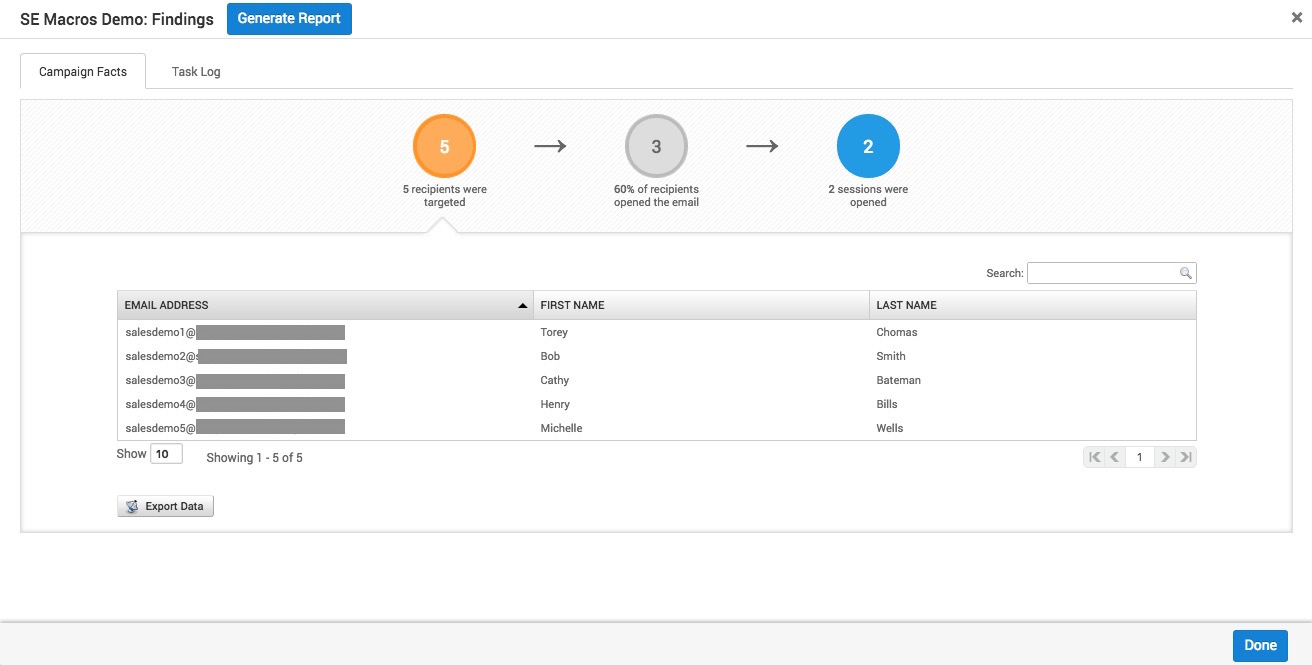
And there you have it. Metasploit has successfully sent malicious files and opened sessions on remote targets via the Social Engineering feature without attempting a phish.
For more on the Microsoft Office Word Malicious Macro Execution module, see sinn3r's post here: /2017/03/08/attacking-micr osoft-office-openoffice-with-metasploit-macro-exploits
Interested in learning more about Metasploit Pro's phishing capabilities? Watch the video below to see how easy it is to build a phishing campaign targeting your users to test their ability to detect malicious emails:
