Security practitioners and the remediating teams they collaborate with are increasingly asked to do more with less. They simply cannot remediate everything; it has never been more important to prioritize and drive remediations from start to finish.
The Remediation Workflow capability in InsightVM was designed to drive more effective remediation efforts by allowing users to project manage efforts both large and small. Remediation Workflow is designed for security practitioners, with the aim of getting them from where they are today to where they envision their security programs to be in the future.
Vulnerability remediation can be a struggle
Let's say a security team wants a set of 10 vulnerabilities remediated across a set of 500 assets. This sounds simple, but in practice could entail months of effort across several remediation teams. There are many considerations:
- What's the most efficient way to eliminate 10 vulnerabilities across 500 assets? Which assets should be remediated first?
- The vulnerability is found across multiple OS's and platforms. As a remediator, how do I track down the solution that is applicable to the asset I am trying to fix?
- How do I get the right instructions to the right asset owners/administrators?
To address these questions through typical means i.e. by vulnerability and by asset means exposing the security team to theoretically 5,000 scenarios (10 vulnerabilities times 500 assets). This is most certainly an exaggeration, but doesn't the back and forth of remediation sometimes FEEL like there are 5,000 questions? We think there's a better way, and we've designed Remediation Projects to be driven by solutions, not vulnerabilities or assets.
Solutions drive vulnerability remediation
Solutions are the remediation steps to eliminate or mitigate a given vulnerability. A vulnerability may contain one or more solutions. Each solution may contain:
- The steps to perform the solution
- References to learn more about the solution or vulnerability
- Risk associated with the solution
Here's the key: A single solution can remediate multiple vulnerabilities. You just have to know which solutions are shared across vulnerabilities. If you knew that, you could determine which solutions to execute on which assets to take down the greatest risk. This is precisely what Remediation Projects are designed to do: take the mindless work of finding the best solutions for the assets within scope.
Creating Actionable Projects
The objective of using a Remediation Project is to drive action in remediation. That's it. To that end, a project should be readily actionable by you and the project's assignees. What do we mean by actionable?
- The project should be able to be understood at a glance, without significant filtering, sorting or scrolling.
- The project should be attainable within a finite period of time.
With these principles in mind, we have a few thoughts on how to create projects for action.
Start with Dynamic Projects
We recommend creating dynamic projects first because the asset and vulnerability filters give you more visibility and control over the number of solutions that will populate the project.
Dynamic projects are very powerful and flexible. They provide elastic scoping based on real time criteria on assets and vulnerabilities. In other words, any assets or vulnerabilities that meet the dynamic project's criteria will be included in the scope of the project.
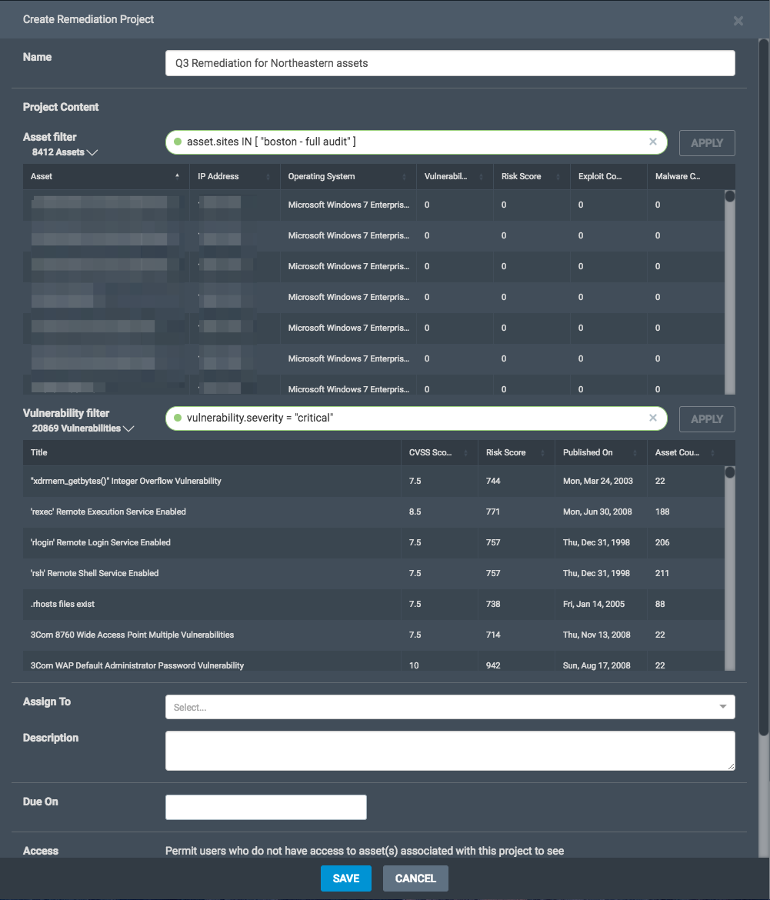
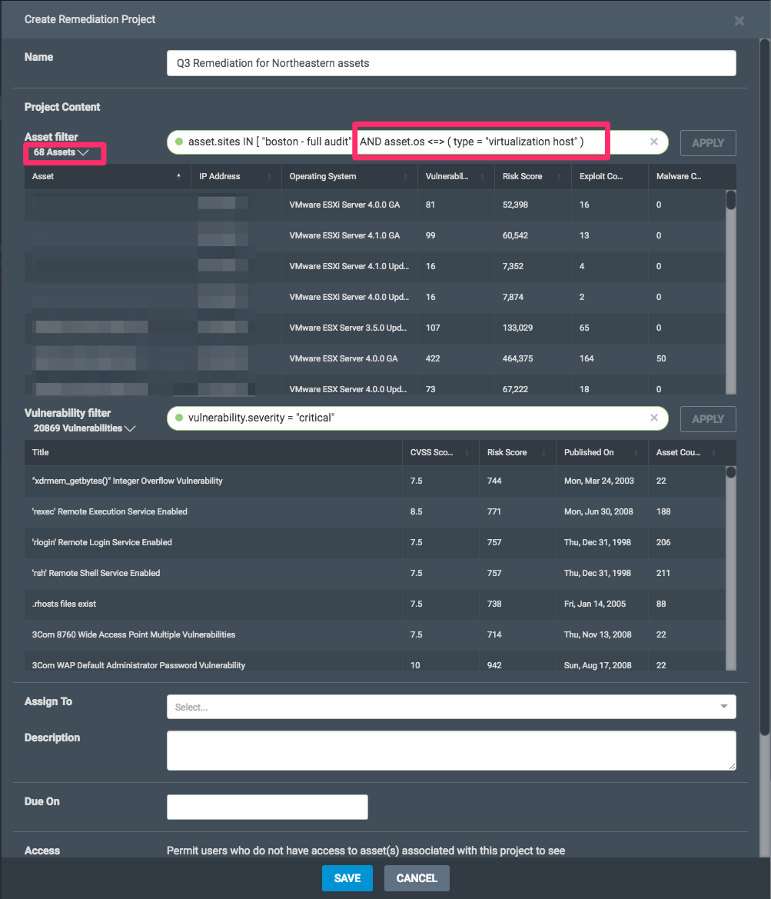
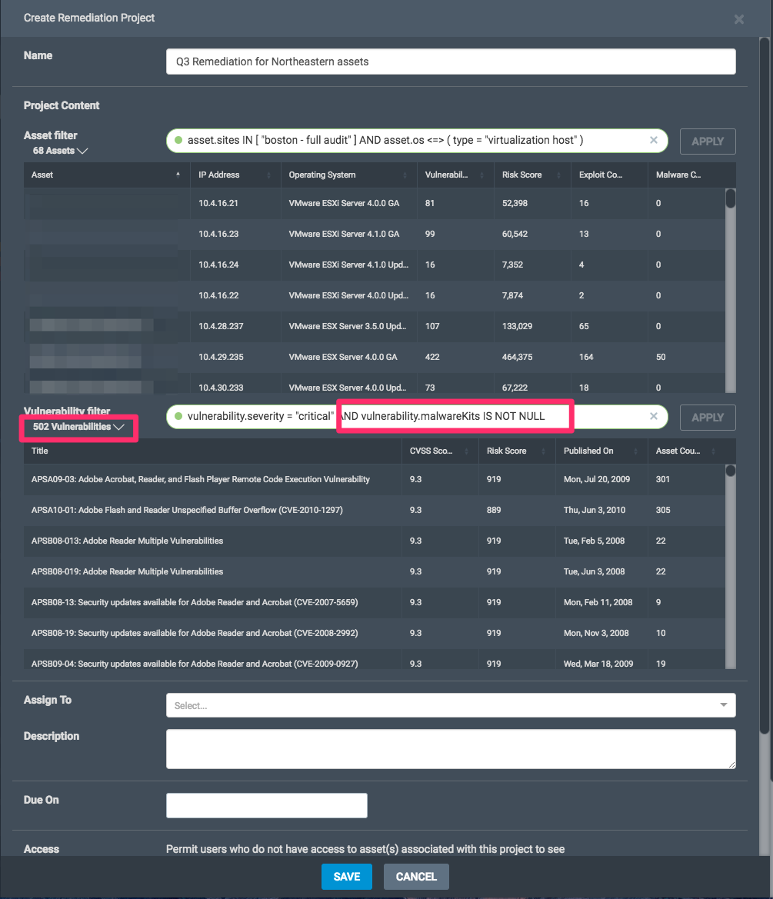
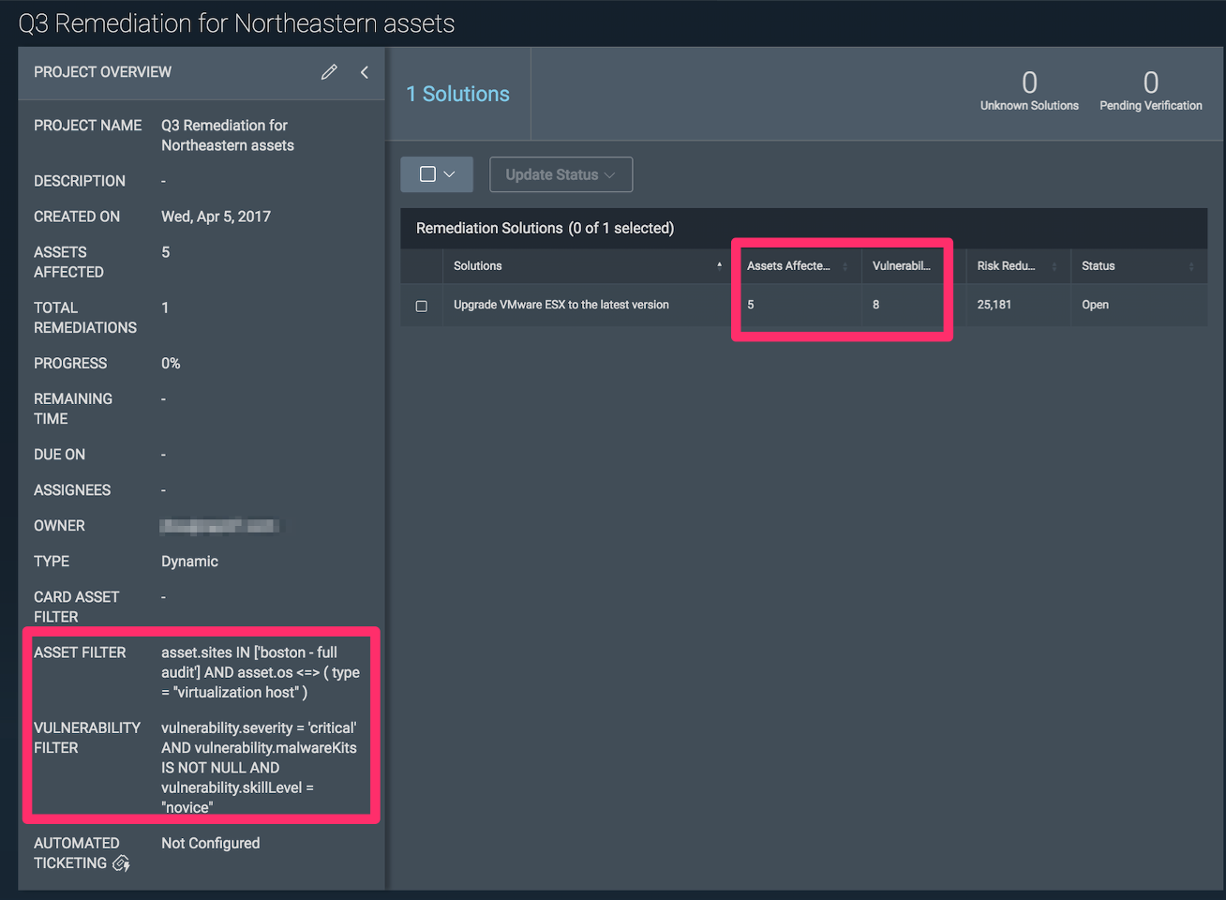
Dynamic projects provide unprecedented ways to maintain oversight on a defined set of work and enable users to pivot quickly in the event there are spikes (numerous instances of a vulnerability found or an influx of matching assets enters the network).
- Any assets of a certain OS or platform family: Windows, Linux, servers, desktops, virtual hosts, etc.
- Any assets with vulnerabilities of a certain category: Critical, Exploitable, CVSS or Risk Scores over a certain threshold.
- Microsoft Patch Tuesday remediation tracking: Utilize the filter criteria such as vulnerability.title CONTAINS “msft-cve-2017” AND vulnerability.datePublished BETWEEN 03-01-2017 AND 04-01-2017.
- Mission-critical, legacy, or otherwise sensitive assets.
- Remediation response to 0-day.
Determine your use case
If you're seeking to drive vulnerability remediation efforts and monitor progress, then utilize the asset filters to help scope by asset ownership (owner tag or OS/Platform) and vulnerability filters to focus on remediations prioritized by risk, CVSS score, severity, category, and exploitability, etc.
Projects are not just for assigning work. There are other uses for Remediation Workflow aside from delegating solutions to assigned remediators. Security Managers can utilize projects without assignees in order to ease ad-hoc and recurring reporting requests. Security Managers can define organization-wide project scopes and separate “sub” projects of increasingly smaller scope in order to have visibility into remediation progress quickly and without disturbing or disrupting remediators.
Is your aim more geared towards reporting and monitoring? If so, create project with a due date and no assignees (unless they are required to aid in reporting).
Refine your project's scope
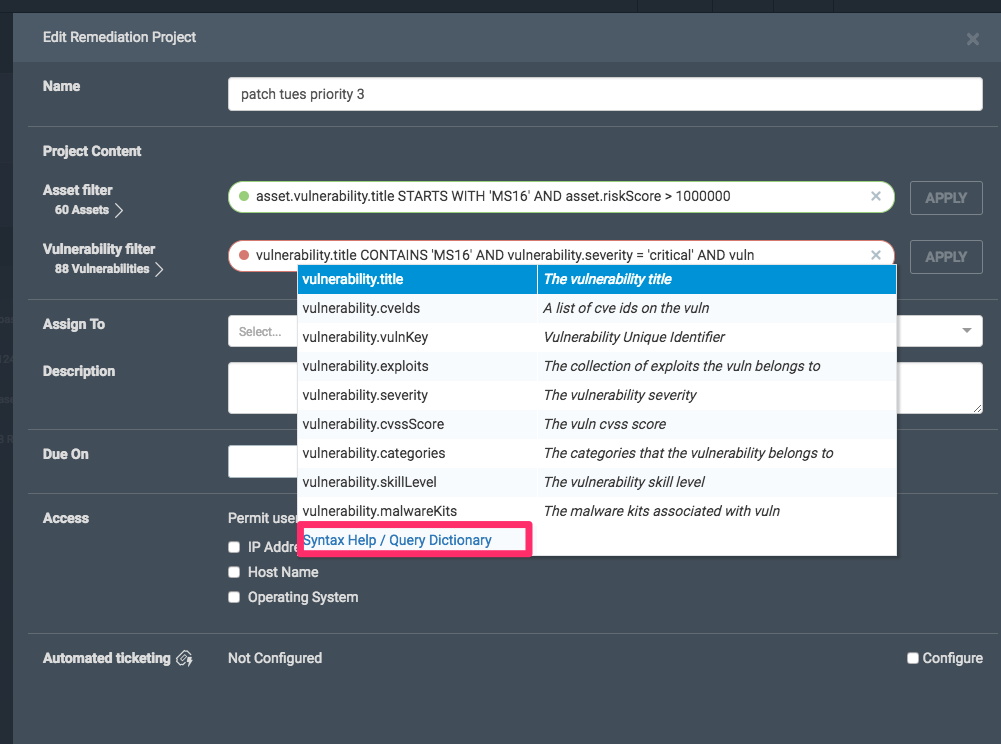
As a project owner, you can edit your dynamic project's scope at any time. Because some solutions can remediate multiple vulnerabilities, a high number of assets and a high number of vulnerabilities do not necessarily guarantee that a large number of solutions will result. However, scoping dynamic projects to a small number of assets and a narrow set of vulnerabilities will help yield a project with a manageable amount of solutions. You can test results of the asset and vulnerability filters by hitting “Apply.”
If your aim is to project manage and drive vulnerability remediation efforts, a dynamic project that is not too broad in scope is best in order to avoid solutions populating a project that are not really part of what you want to have actioned. Utilize the type-ahead behavior of the filters, as well as the Syntax Help/Query Dictionary (see below), in order to get a fuller sense of the filter criteria at your disposal.
- Vulnerability Exploitability
- Skill set required to exploit the vulnerability
- Asset tags (owner, custom, location)
- Asset OS (family, architecture, vendor)
- Asset risk score
- Vulnerability severity, CVSS score
- Vulnerability title contains a certain string
- Vulnerability publish date
How to Get Started
Remediation Workflow provides a powerful and flexible way to define, monitor, manage, and drive remediation efforts big and small throughout your organization. Remediations can be challenging. Remediation Workflow reduces friction between security and IT teams with its solution centric approach that automatically incorporates solution, asset, and vulnerability data, empowering teams to get from start to remediated faster.