This post describes a vulnerability in Yopify (a plugin for various popular e-commerce platforms), as well as remediation steps that have been taken. Yopify leaks the first name, last initial, city, and recent purchase data of customers, all without user authorization. This poses a significant privacy risk for customers. This vulnerability is characterized as: CWE-213 (Intentional Information Disclosure).
Product Description
Yopify is a notification plugin for a variety of e-commerce platforms, including BigCommerce, WooCommerce, Shopify, and LemonStand. The product is produced by Centire, an IT company based in India. Yopify provides a feature where website visitors are, every few seconds, presented with a popup containing information about one of the last 50 purchases from the site, such as the one shown here:
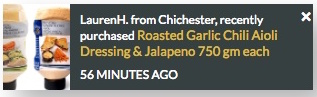
The purported use case is that by demonstrating existing customer activity, it replicates the public bustle and hubbub of a real-world shop, and makes potential customers more engaged. As you can see, the example above contains personal information about the customer (first name, last initial, city).
The various plugin sites for major e-commerce platforms show over 300 reviews of Yopify, which suggests that the number of exploitable sites is at least in the hundreds, and perhaps thousands.
Credit
This vulnerability was discovered by Oliver Keyes, a Rapid7, Inc. senior data scientist. This advisory was prepared in accordance with Rapid7's vulnerability disclosure policy.
Exploitation
Yopify works by having the e-commerce site load a JavaScript widget from the Yopify servers, which contains both the code to generate the UI element and the data used to populate it, stored as JSON. This widget does not require any authorization beyond a site-specific API key, which is embedded in the e-commerce site's source code, and is easily extractable with a regular expression.
The result is that by scraping a customer site to grab the API key and then simply running something like:
curl 'https://yopify.com/api/yo/js/yo/3edb675e08e9c7fe22d243e44d184cdf/events.js?t=1490157080'
where 3edb675e08e9c7fe22d243e44d184cdf is the site ID and t is a cache buster, someone can remotely grab the data pertaining to the last 50 customers. This is updated as purchases are made. Thus an attacker can poll every few hours for a few days/weeks/months and build up a database of an e-commerce site's customer set and associated purchasers.
The data exposed to this polling was, however, far more extensive than the data displayed. While the pop-up only provides first name and last initial, the JSON blob originally contained first and last names in their entirety, along with city-level geolocation. While the casual online customer wouldn't have seen that, a malicious technical user could have trivially gained enough information to potentially target specific users of specific niche e-commerce sites.
Vendor Statement
We were unaware of this security threat when we created the app, however have taken the necessary steps alongside Shopify and Rapid7 to come to a satisfactory resolution where users privacy exposure is reduced.
Remediation
Minimally, we believe users should be asked if they want their name, location, and purchase information shown to complete strangers. Sending and display of the information should be off by default to protect customer privacy and safety.
On May 18, Yopify responded to the bug report by Base64-encoding the JSON blob. This obfuscation may stop some unsophisticated users from finding the information, but it is in no way encrypted. However, by May 20 Yopify did make an additional update and the client no longer receives the full last name even in the JSON, but only the first letter of the last name. This is an improvement as it does limit the exposure of user data, and makes identifying individuals more difficult.
However, as personal information is still sent and displayed, we recommend that until Yopify adds opt-in functionality, users with privacy concerns avoid using e-commerce sites with Yopify installed. Users will know it is installed given the frequent pop-ups displaying other customers' information when they browse an affected site. In addition, we encourage e-commerce store owners to request Yopify add this functionality, or remove the widget in order to protect their customers' privacy.
Disclosure Timeline
This vulnerability advisory was prepared in accordance with Rapid7's vulnerability disclosure policy.
- Tue, Feb 28, 2017: Discovered by Rapid7's Oliver Keyes
- Wed, Mar 22, 2017: Initial vendor contact (Yopify)
- Thu, Mar 30, 2017: Additional vendor contact (Shopify), as no response received from Yopify yet
- Thu, Mar 30, 2017: Response from Shopify
- Fri, Mar 31, 2017: Details sent to [email protected], who forwarded information to Yopify
- Wed, Apr 5, 2017: Additional vendor contact (Centire). Sent reminder to Yopify, and clarification/update to Shopify.
- Fri, Apr 7, 2017: Additional disclosure to [email protected]
- Fri, Apr 7, 2017: Disclosed to CERT/CC
- Fri, Apr 14, 2017: Reached back out to [email protected], no response
- Wed, Apr 26, 2017: CVE-2017-3211 assigned by CERT/CC
- Wed, May 17, 2017: Reached back out to Yopify and Centire
- Thu, May 18, 2017: First response from Yopify; JSON Base64 encoding change deployed
- Sat, May 20, 2017: Additional patch deployed by Yopify: full last name no longer sent to client, only first letter
- Wed, May 31, 2017: Public disclosure