We often hear that security teams are overwhelmed by the number of vulnerabilities in their environments: every day they are finding more than they can fix. It doesn't help when rating schemes used for prioritization, like the Common Vulnerability Scoring System (CVSS), don't really work at scale or take the threat landscape into account. How do you know where to focus if your vulnerability management solution shows that you have 10,000 vulnerabilities with a critical or high severity rating? And when a high profile vulnerability comes along, how do you quickly gain insight into its impact on your organization?
Understanding which vulnerabilities are most likely to be exploited by an attacker is critical for effective vulnerability prioritization. That's why the RealRisk score used in InsightVM and Nexpose takes into account whether a vulnerability is targeted by a known exploit or malware kit. In addition, the Rapid7 Critical vulnerability category enables security teams to automatically assess the risk posed by critical threats, particularly 0-days that don't have a CVSS score yet.
But given recent events, there is clearly a need for vulnerability-based threat intelligence. Rapid7 already gathers and analyzes data on attacker methodology and emerging threats through the Rapid7 Insight platform, Rapid7 Labs' Project Heisenberg Cloud, our Managed Detection and Response team, and the Metasploit community. We want to make all this data available to our customers to help them better understand their exposure to the constantly changing threat landscape, but in a way that adds real value and not just noise.
Introducing the Rapid7 Threat Feed in InsightVM
The Rapid7 Threat Feed is a live, curated feed of vulnerabilities being actively exploited by attackers in the wild; these are the most dangerous vulnerabilities and should be addressed immediately. The feed combines data collected by our Heisenberg honeypots and incident response activity with information from trusted third parties:
| Source | Description |
|---|---|
| Heisenberg | Attacks detected by Rapid7 Lab's modern honeypot framework |
| IR Activity | Confirmed incidents from Rapid7's Managed Detection and Response team |
| FBI | Information shared as part of the FBI's private sector partnership |
| InfoSharing | Information shared from a trusted partner tracking this threat |
| Open Source | Publicly available information |
In addition to actively monitoring and curating the feed, the Rapid7 Threat Intelligence team adds important context such as threat vector and actor information so you can see how relevant a threat is to your organization.
Visualizing Threats in Your Environment
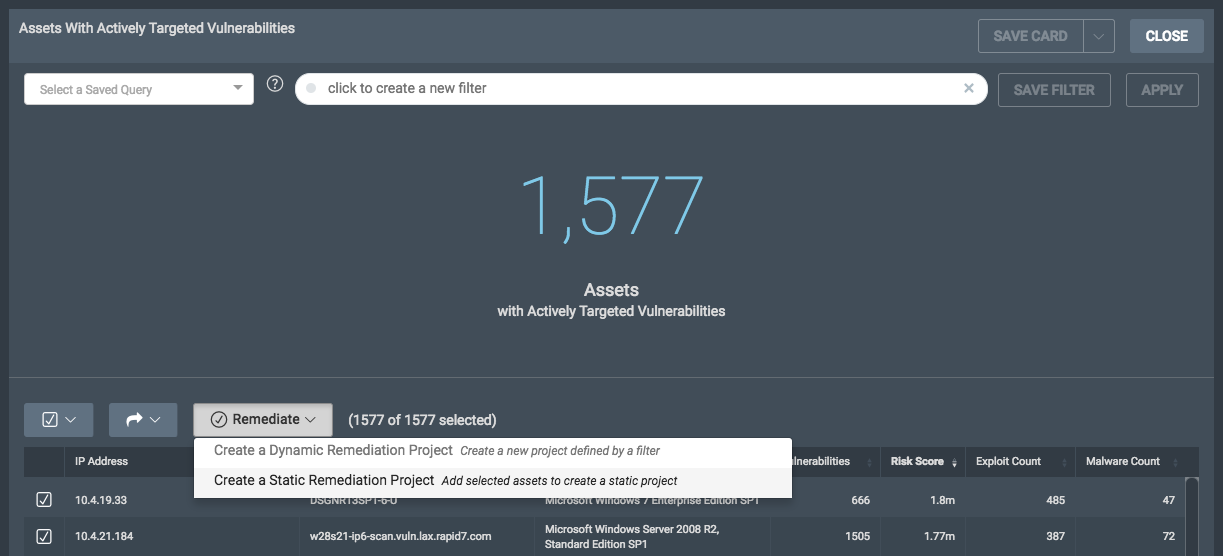
But just having information is not enough, it needs to be combined with context about your organization's environment to make it actionable. We added a new Threat Feed Dashboard template that makes it easy for you to see how exposed your organization is to active threats and where you need to focus to reduce the likelihood of an attack. This dashboard includes information such as the percentage of assets or vulnerabilities in your environment that can be exploited by a novice, the most commonly exploited vulnerabilities, and common exploits and malware kits.
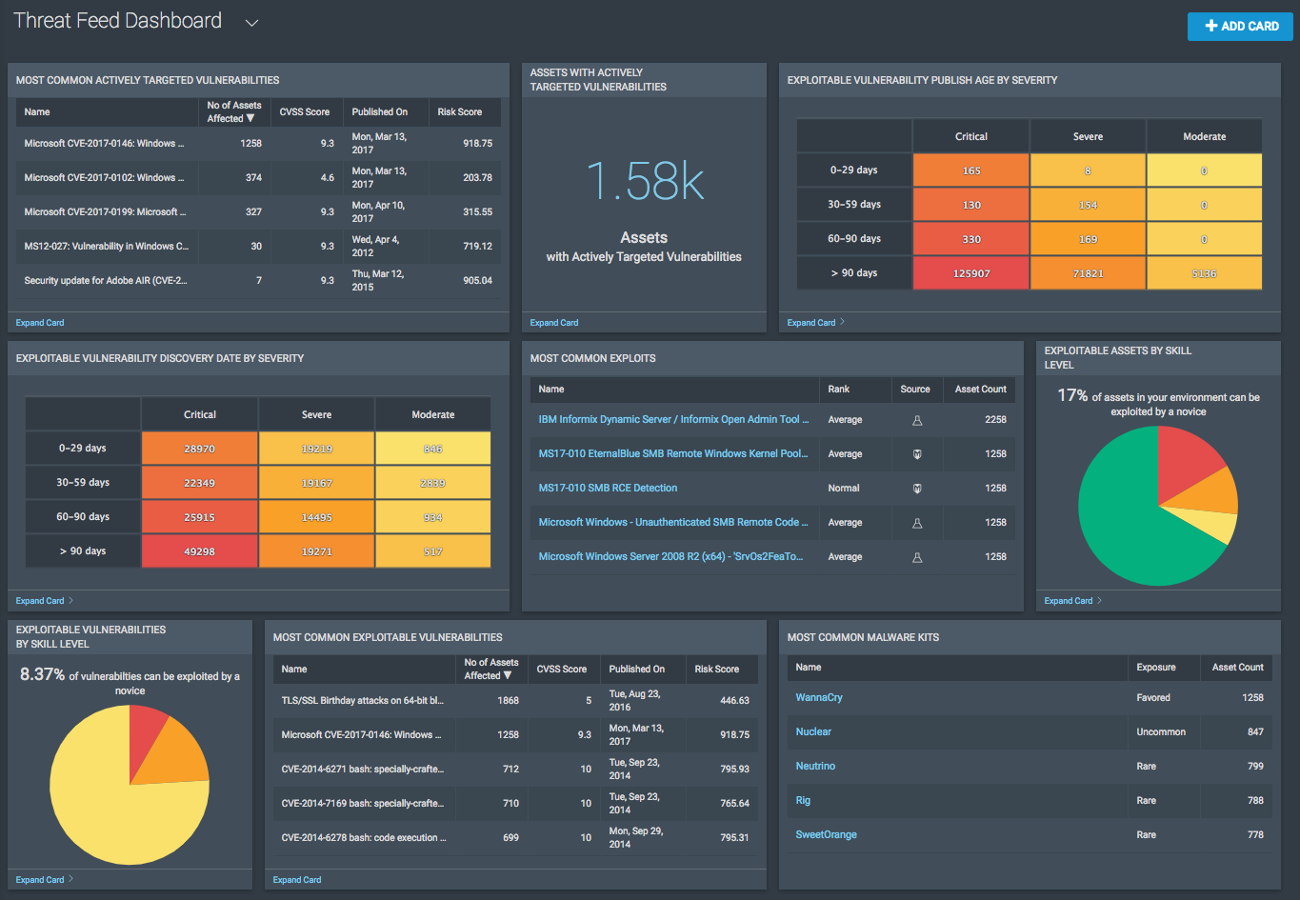
Specifically, there are two new dashboard cards that leverage the Rapid7 Threat Feed. The Most Common Actively Targeted Vulnerabilities card shows you the most prevalent active threats in your environment. Clicking on this card gives a full list of actively exploited vulnerabilities on your network, which you can drill into for the Rapid7 Threat Feed details. The Assets with Actively Targeted Vulnerabilities card shows you the total number of assets on your network that are affected by active threats and which assets you need to prioritize for remediation.
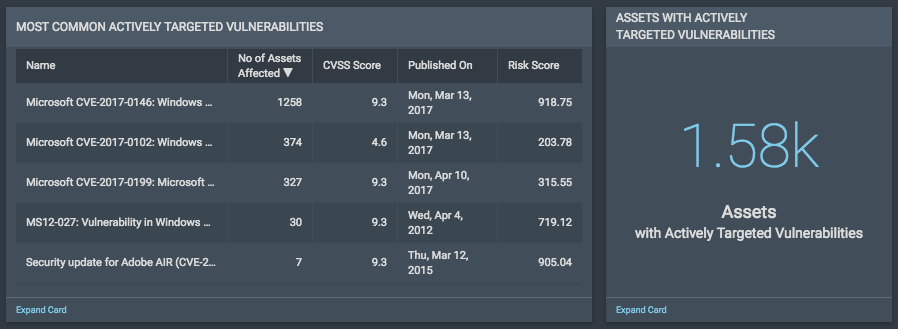
Remediating Threats in Your Environment
Finding the most dangerous vulnerabilities in your environment is only half the job—next you need to actually fix them. Clicking on the Assets with Actively Targeted Vulnerabilities card gives a full list of affected assets, which can be added to a Static Remediation Project for driving action. With Remediation Workflow, you can create and assign tickets automatically, provide relevant and actionable information, and track progress from start to finish.